Yeah, Huawei doesn't expose much configuration for the end user. But, you do what you can with what you have.
I have an E8372 USB dongle which, fortunately, does expose a "DMZ" function. So this afternoon I set up a successfully-working WireGuard connection on OpenWRT and Android, as shown in Buchan's article, with the following equipment and software:
- Huawei E8372 USB 4G modem
- GL-iNet MT300N-v2 with OpenWRT 18.06.4, all post-18.06.4 opkg updates applied, and the following extra packages installed:
** wireguard
** wireguard-tools
** kmod-wireguard
** luci-app-wireguard
** luci-proto-wireguard
** ddns-scripts
** ddns-scripts_no-ip_com
** luci-app-ddns
- Sony Xperia X Compact phone, running Android 8 and WireGuard app version 0.0.20190708
- An account with noip.com for DDNS
- The DDNS hostname lanakane.ddns.net (My choice of DDNS provider is irrelevant; I already had an account with no-ip.com and couldn't be bothered jumping through myriad hoops just to register with DuckDNS. As long as DDNS resolves to the correct IP address, then that's all that matters.)
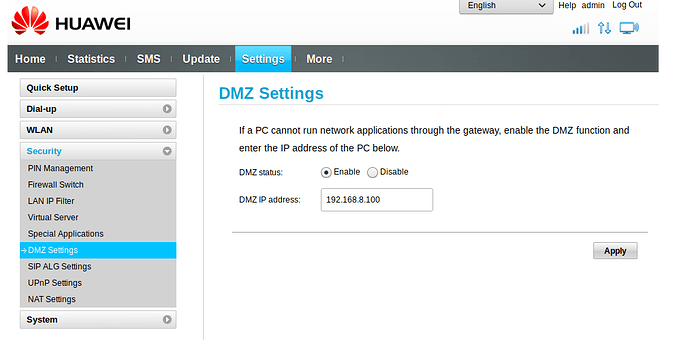
The first thing to note is that if I did not enable the DMZ feature on the Huawei E8372, then nothing reached the MT300N. Once I enabled the DMZ feature on the E8372, then external traffic started reaching the MT300N.
So if you're not seeing any traffic hitting OpenWRT's WAN interface at all, then check the Huawei's configuration, particularly the DMZ setting.
Here are the relevant parts of the MT300N's configuration. Interface names may be different for your setup:
/etc/config/network:
config interface 'mobile'
option proto 'dhcp'
option ifname 'eth1'
config interface 'wg2'
option proto 'wireguard'
option private_key 'ILhaJHp+eK4vCdoCAR2jFtaoHlfGsKPk48DMrj2beV4='
option listen_port '51280'
list addresses '10.200.200.1/24'
config wireguard_wg2
option public_key '4KEBz5GMG2SaxM/mEpMOtj0Rpz6w1/XQaFOZCZNNF1Q='
list allowed_ips '10.200.200.2/32'
option route_allowed_ips '1'
option persistent_keepalive '25'
/etc/config/firewall:
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan wg2'
config rule
option src '*'
option target 'ACCEPT'
option proto 'udp'
option dest_port '51820'
option name 'Allow-Wireguard-Inbound'
/etc/config/ddns:
config service 'NoIP'
option lookup_host 'lanakane.ddns.net'
option service_name 'no-ip.com'
option domain 'lanakane.ddns.net'
option password 'My No-IP password'
option enabled '1'
option username 'My No-IP username'
option interface 'mobile'
option use_syslog '1'
option ip_source 'script'
option ip_script '/etc/ddns/myip'
/etc/ddns/myip:
curl ifconfig.co
Here are the ifconfig and route details from the MT300N:
root@mt300nv2:/etc/config# ifconfig eth1
eth1 Link encap:Ethernet HWaddr 0C:5B:8F:27:9A:64
inet addr:192.168.8.100 Bcast:192.168.8.255 Mask:255.255.255.0
inet6 addr: fe80::e5b:8fff:fe27:9a64/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:39174 errors:0 dropped:0 overruns:0 frame:0
TX packets:35636 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:20355546 (19.4 MiB) TX bytes:10749832 (10.2 MiB)
root@mt300nv2:/etc/config# ifconfig wg2
wg2 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.200.200.1 P-t-P:10.200.200.1 Mask:255.255.255.0
UP POINTOPOINT RUNNING NOARP MTU:1420 Metric:1
RX packets:7075 errors:0 dropped:3 overruns:0 frame:0
TX packets:6696 errors:0 dropped:3 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:4034220 (3.8 MiB) TX bytes:1756180 (1.6 MiB)
root@mt300nv2:/etc/config# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.8.1 0.0.0.0 UG 0 0 0 eth1
10.200.200.0 0.0.0.0 255.255.255.0 U 0 0 0 wg2
10.200.200.2 0.0.0.0 255.255.255.255 UH 0 0 0 wg2
Here is the relevant setting from the Huawei E8372:
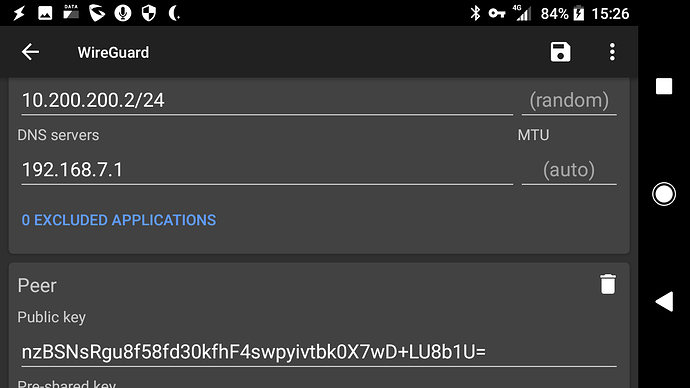
Here is the configuration of WireGuard on my Android phone:
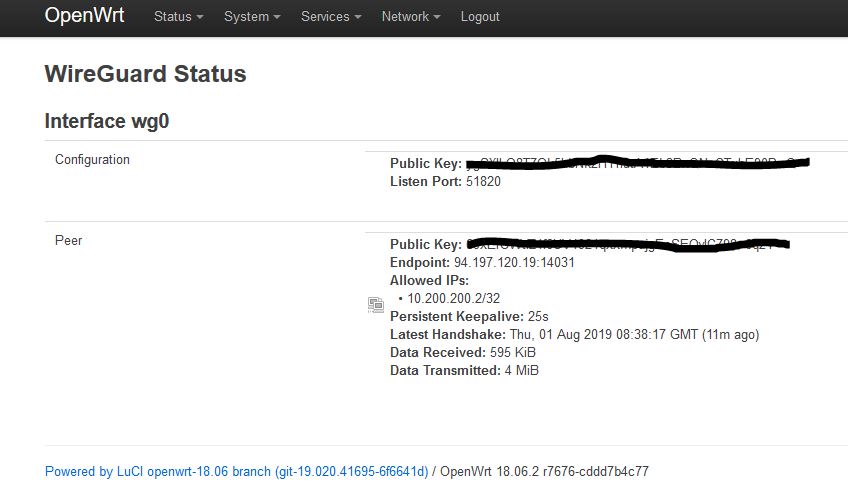
And here's the evidence of the successful connection and response:
If you follow Buchan's instructions, they will work. If they don't, you've missed something. Bear in mind that you're making it more difficult for yourself by trying to host a server (which typically benefits from a static IP address) on a service which is infamous for aggressively recycling DHCP addresses (Three). It's not impossible to achieve (as I've just proven in the course of preparing this reply), but it is more awkward than it needs to be.