I copied the configuration into my gl-inet wireguard client to test and it isn't getting online at all.
What variant are you using, yazdan’s package or the other 2 packages mentioned in the thread?
If you feel compelled to investigate, the first question from Paul @ruralroots is just as important as the configurations you can provide by ssh command executed and copied into preformatted text.
ubus call system board; uci export dhcp; uci export network; uci export firewall
You leave so much to be assumed; however, I will offer this.
I have a valid Surfshark account, my firewall is good, my DNS is good, my device is supported, my Wireguard install on said device is unchanged since 4/15/2022.
However!! Thursday was a bad day for the WireGuard Client app on my pc.
Log shows, and results were no connection out. By Friday morning it was back to normal without me changing anything.
4 unique peers were all not handshaking over the course hours. With the Wireguard App on PC, I can assign the Surfshark DNS servers exactly as assinged from say the Surfshark OpenVPN .ovpn connection. And to that point OpenVPN to Surfshark worked where Wireguard did not for this period of time below.
2022-06-23 14:47:19.413694: [MGR] [us-dal.prod] Trying again to stop zombie tunnel
2022-06-23 16:00:41.575181: [MGR] [nl-ams.prod] Trying again to stop zombie tunnel
2022-06-23 17:01:37.582344: [MGR] [ca-tor.prod] Trying again to stop zombie tunnel
2022-06-23 17:10:21.627157: [MGR] [nl-ams.prod] Trying again to stop zombie tunnel
2022-06-23 17:11:03.165115: [MGR] [pl-waw.prod] Trying again to stop zombie tunnel
2022-06-24 09:43:08.220643: [MGR] [nl-ams.prod] Trying again to stop zombie tunnel ```Hi,
I cannot find some conf files for wireguard i.e. they are not returned via the API call.
e.g in-vrt.prod.conf
Am I missing something on my side, could someone please help ?
These are only ones returned in my conf folder:
in-chn.prod.conf
in-idr.prod.conf
in-mum.prod.conf
Where did you see in-vrt.prod.conf
Hi @RuralRoots,
Surfshark no longer had physical servers in India and API call does not return the three config's you mentioned above (these files might exists from earlier API calls).
Now they have only one virtual server that's named as in-vrt
Guy's you can try a different api call that is baked into the scripts listed here.
I modded the code a bit and generated the required in-vrt.prod.conf file. Try these two peers in your wg config:
Summary
cat in-vrt.prod.conf
[Interface]
PrivateKey=+++ Add Your Private wg Key +++
Address=10.14.0.2/8
MTU=1350
[Peer]
PublicKey=o07k/2dsaQkLLSR0dCI/FUd3FLik/F/HBBcOGUkNQGo=
AllowedIPs=172.16.0.36/32
Endpoint=wgs.prod.surfshark.com:51820
PersistentKeepalive=25
[Peer]
PublicKey=AvyHyRd/P4AnYV/5hSrR+ATx+Ogt8CFe/r7WR+C6Uyo=
AllowedIPs=0.0.0.0/0
Endpoint=in-vrt.prod.surfshark.com:51820
PersistentKeepalive=25
No guarantees, but if this works for you I’ll post what to change in the script to generate virtual server .conf files.
Thanks @RuralRoots
It worked ![]() Could you please let me know the changes I need to make in the script ?
Could you please let me know the changes I need to make in the script ?
Thanks for you help
Here you go:
Replace Line 86 in the select_servers () function with
cat_res=$(cat $servers_file | jq 'select(any(.[].tags[]; . == "virtual" or . == "p2p" or . == "physical"))')
This adds virtual servers to the selected_servers.json file that is used to generate the `.conf. files.
rm surf_servers.json
rm selected_servers.json
rm -r conf
and run gen_wg_config.sh to regenerate the .conf files.
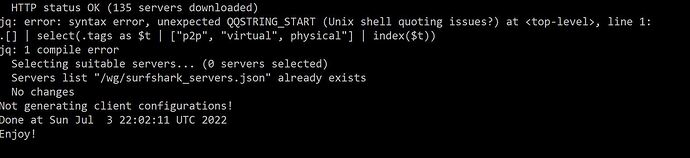
following the guide but get presented with the jq 1 compilation error and no config files in the folder.
im a total newbie. please be patient
thank you
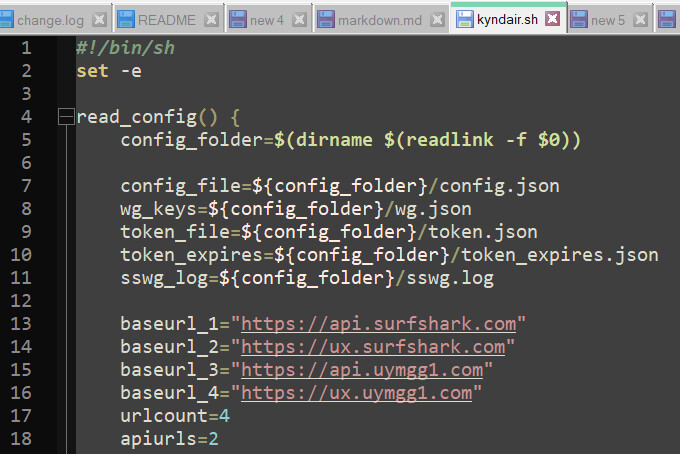
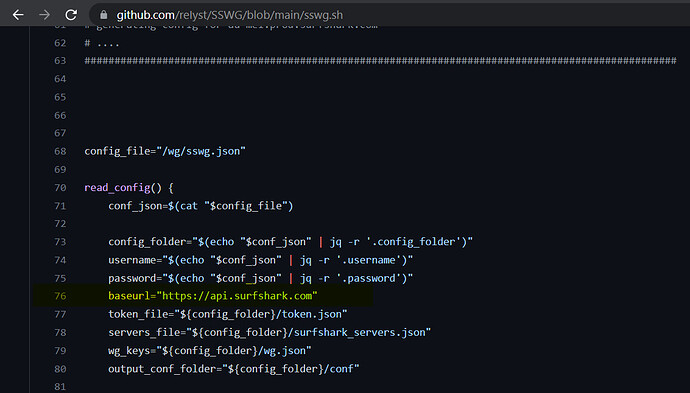
jq '.[] | select(.tags as $t | ["p2p", "virtual", "physical"] | index($t))' "$tmpfile" | jq -s '.' > "$tmpfile2"
Line 125 of the sswg.sh file is missing the quote string in your picture at physical.
Look at your output and compare it to the line above. A simple edit or replace by download and replace can rectify this error.
Thank You.
This was my error in the two files edited on GitHub's merge. I have edited the two relevant files to correct my mistake for future user's interest.
Thank you @max414 for making this honest mistake evident and corrected, sorry that you were inconvenienced.
Awesome @Bill . Can you point me to the link of the newly updated files which you have now edited ?
Ill be happy to give it a go ![]()
Thanks for the quick response
I've direct messaged you, but to be certain you're on track...these were corrected highlighted in pic.
You only need to edit line 125 of the sswg.sh script using the editor you used to edit your sswg.json file. Or download the sswg.sh script and copy it over in the same process used in your initial install.
Proper line 125; now edited on GitHub, should/will look like this:
jq '.[] | select(.tags as $t | ["p2p", "virtual", "physical"] | index($t))' "$tmpfile" | jq -s '.' > "$tmpfile2"
hey guys, thank you all and a big shout out to @Bill for the continued support.
i have the openwrt surfshark up connected via wireguard using yazdan and sswg script.
to all newbies ill post my 2 cents as to how the thing works.
how i did it personally, your mileage may vary.
fresh install openwrt
after login.... all the relevant software installed ( jq, curl, wireguard-app, ntpdate etc. )
downloaded and installed win SCP and ssh into root directory of router.
downloaded sswg script and extracted to its own folder.
created directory /wg in root and added the sswg.json and sswg.sh into directory (copied from the sswg script directory )
edit sswg.json and enter your personal surfsharf credentials and save.
run the scripts as previously stated in the thread and you have all the configs with the info needed.
crontab configuration to automate regeneration of keys... following the script commands was easy
created a wg0 interface using the script commands in the thread
configured firewall using the scripts in the thread
after all this was done, i headed back into openwrt gui interface and could see that wg0 interface said missing protocols.
a quick restart on the router did the trick and im running stable wireguard surfshark vpn since.
thank you for the continued support and to all newcomers, dont be shy to ask.
wonderful lot of people here.
thank you
It seems like this feature will be officially supported next month, you can check in the comments of this video

Update: Remove the Stubby DNS packages and my speed is nominal.
Kind of topical, but I moved into the new OpenWrt 22.03.0-rc5. Using the Tut's and Peer Swap and playing around I finally did a call for the script. It was an obvious improvement from running this on OpenWrt 19.07.10
The process only took 32 seconds and the noticeable lag (as always) was on:
Just a Sec 'ntpdate' sycning clock
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
OpenWrt 22.03.0-rc5, r19523-bfd070e7fa
-----------------------------------------------------
root@Dachshund:~# cd /
root@Dachshund:/# cd /wg
root@Dachshund:/wg# ./sswg.sh -g
Just a Sec 'ntpdate' sycning clock
Running at Sun Jul 10 13:47:06 EDT 2022
WireGuard keys "/wg/wg.json" already exist
Using public key:+c523x0yWWG3Xy/h84 AfrO0LDUpfLXoedXmj7QB06Ts=
Token file "/wg/token.json" exists, skipping login
Registering public key...
Access denied: Expired JWT Token
Token file corrupted! Deleting if available, and attempting to Login...
Logging in...
HTTP status OK
Registering public key...
Already registered
Renewed! (expires: 2022-07-17T17:47:12+00:00)
Hello World Wide WireGuard©
Thanks Jason A. Donenfeld
Retrieving servers list...
HTTP status OK (136 servers downloaded)
Selecting suitable servers... (86 servers selected)
Servers list "/wg/surfshark_servers.json" already exists
Servers changed! Updating servers file
generating config for al-tia.prod.surfshark.com
generating config for dz-alg.prod.surfshark.com
generating config for ad-leu.prod.surfshark.com
### Truncated ###
generating config for vn-hcm.prod.surfshark.com
Done at Sun Jul 10 13:47:38 EDT 2022
Enjoy!
root@Dachshund:/wg#
Users that have a cron job set for Thursday:
will you check your wg.log file for renewal or failure please.
Using Putty issue command
cat /wg/wg.log
WinSCP just navigate to the /wg directory and double click on your wg.log
Look for similar.
This is the first time since 4/15/2022 I've seen a "HTTP 000".
To fix my issue I just changed peers and ran the script manually.
/wg$ cat /wg/wg.log
Just a Sec 'ntpdate' sycning clock
Running at Thu Jul 14 00:25:09 EDT 2022
WireGuard keys "/wg/wg.json" already exist
Using public key: LD23x04UyfLedXmjWWAfrO0Xo6Ts+c5G3Xy/h8p7QB0=
Token file "/wg/token.json" exists, skipping login
Registering public key...
Failed: HTTP 000,
Done at Thu Jul 14 00:25:10 EDT 2022
Enjoy!
7/14/2022 edit
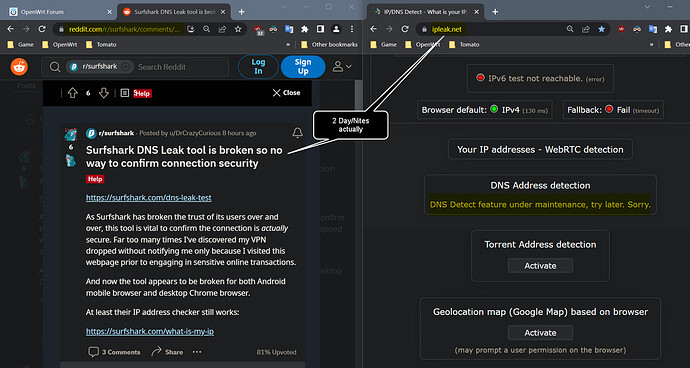
Troubles in SurfShark waters... Soooo... i've been testing DNS leaking for 4 days/nights now, using their own DNS severs and the test page @ is now rate limited.
Please don't use the PSA as a reason to get on Reddit and Rant
(https://www.reddit.com/r/surfshark/comments/w05beb/interesting_banning_its_own_ips_from_accessing/)
7/28/2022 edit
7/31/2022 edit
Updated Git with new sswg2.sh to "Overcome 000 failure"
Log and Link
https://github.com/reIyst/SSWG/blob/main/sswg2.sh
BusyBox v1.35.0 (2022-07-06 19:09:39 UTC) built-in shell (ash)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
OpenWrt 22.03.0-rc5, r19523-bfd070e7fa
-----------------------------------------------------
root@Dachshund:/wg# ./sswg.sh
Just a Sec 'ntpdate' sycning clock
Running at Sun Jul 31 00:23:10 EDT 2022
WireGuard keys "/wg/wg.json" already exist
Using public key: 04dXmj7QB0XoAfrO0+c523x6TsLDUyWWG3Xy/h8pfLe=
Logging in...
HTTP status OK
Registering public key...
Already registered
Renewed! (expires: 2022-08-07T04:23:13+00:00)
Hello World Wide WireGuard©
Thanks Jason A. Donenfeld
Done at Sun Jul 31 00:23:14 EDT 2022
Enjoy!
root@Dachshund:/wg# ./sswg.sh -g
Just a Sec 'ntpdate' sycning clock
Running at Sun Jul 31 00:23:43 EDT 2022
WireGuard keys "/wg/wg.json" already exist
Using public key: 04dXmj7QB0XoAfrO0+c523x6TsLDUyWWG3Xy/h8pfLe=
Logging in...
Overcoming Curl 000 failure...
HTTP status OK
Registering public key...
Already registered
Renewed! (expires: 2022-08-07T04:23:47+00:00)
Hello World Wide WireGuard©
Thanks Jason A. Donenfeld
Retrieving servers list...
HTTP status OK (137 servers downloaded)
Selecting suitable servers... (87 servers selected)
Servers list "/wg/surfshark_servers.json" already exists
Servers changed! Updating servers file
generating config for al-tia.prod.surfshark.com
generating config for dz-alg.prod.surfshark.com
### Truncated ###
8/10/2022 Find the Release Here Keys.sh new functions.
Readme-Keys
-
 Tested on OpenWrt 22.03.0-rc6 : MikroTik RouterBOARD 951Ui-2nD (hAP) : YMMV
Tested on OpenWrt 22.03.0-rc6 : MikroTik RouterBOARD 951Ui-2nD (hAP) : YMMV 
- Use custom DNS servers on
if wg0has DNSSEC and DNSSEC check unsigned :
: dnsmasq-full - 2.86-13package. - If deciding to run with DNSSEC you'll need
dnsmasqto be uninstalled anddnsmasq-fullinstalled. Link : Right Click/Open New Tab to go to highlighted section. opkg updateopkg install dnsmasq-full --download-only && opkg remove dnsmasq && opkg install dnsmasq-full --cache . && rm *.ipk
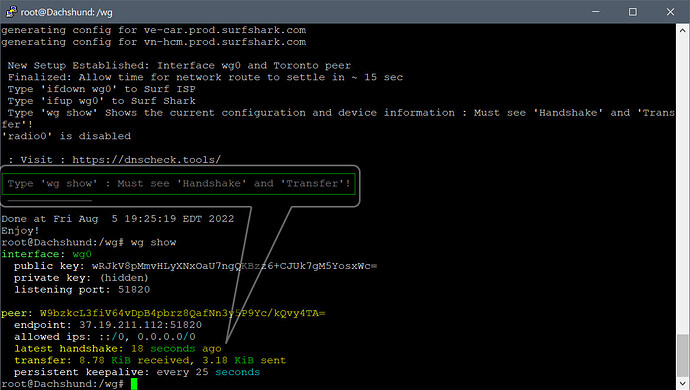
New Setup: Interface "wg0" in the WAN zone firewall and Toronto peer activated!
Use LuCi Interface Settings to drag-n-drop new conf.
Import configuration
Load configuration…
Imports settings from an existing WireGuard configuration file.
Your Options
" #### Switch -'option' #### "
" ____________________________________________________________"
""
" '-n' : eg : ./keys.sh -n :New Setup Establish "
" '-d' : eg : ./keys.sh -d :Delete 'wg0' and trace settings "
" '-g' : eg : ./keys.sh -g :Generate Server conf "
" ' ' : eg : ./keys.sh :Extend Key Duration "
" ____________________________________________________________"
Usage Inline (existing /wg install)
- If your are considering using this with a current install: Save your
wg.jsonfile before runningkeys.sh -d. - The
keys.sh -dwill only remove from/etc/config/networkand/etc/config/firewallwhat thekeys.sh -ncommand implanted. - However, it will wipe the /wg/ directory of
token.json,wg.json,surfshark_servers.json, and the/wg/conf/*directory.
Backup if unsure!
Safe usage of keys.sh inline with a current install would be to run with option:
-
./keys.sh -g"Generate Server conf" or -
./keys.sh"Extend Key Duration".
Those commands are considered standard option issswg.sh.
Usage Fresh Run
I just flashed my router. Bare-bones till online via keys.sh -n ~ 17 minutes  You Can Be Better!
You Can Be Better! 
-
opkg updateopkg install diffutils curl jq ntpdate -
mkdir -p /wg/Edit yoursswg.jsonwith your up-to-date SurfShark VPN account creds:
############################## Example of sswg.json ##############################################
# {
# "config_folder": "/wg",
# "username": "user@neverland.com",
# "password": "admin"
# }
###################################################################################################
Transfer sswg.json and keys.sh to /wg/ dir.
chmod +x keys.sh allows script to be executable.
opkg update opkg install luci-app-wireguard
- Reboot your system so the above packages can manifest in Luci.
ssh into your router's ip and issue the command from the /wg dir ./keys.sh -n
The Main Functions Explained Here
New Functions:
wg0_new()
The function is calling all other MAIN funtions to do their job and pull in all the SurfShark goodness. Addionally; one peer, with all the setting needed to get online WireGuard/SurfShark style fast is configured therein. A custom if name config wireguard_wg0 'peertorc' that allows for the use of peer swapping via cli. Your script can be modified in this section to suit your needs. Learn the uci paramaters. This can be studied via the LuCi save view in the upper right hand corner before you hit Save and Apply. This is true no matter if you are adding or deleting item from your web session in LuCi. Just look at what is being held in the pre-commit stage ~ copy/paste into an editor of choice and learn your way thru it.
reset_keys()
Quick/Quiet removal of the /wg/conf/ folder, wg.json , token.json , surfshark_servers.json . Leaving keys.sh , sswg.json , and all user placed item not mentiond here.
Copyright and Attribution of developed software, tool, logo, names are the right of the following entities respectively.
![]() CC Attribution-Share Alike 4.0 International
CC Attribution-Share Alike 4.0 International
© 2022 Copyright Surfshark. All rights reserved.
 © Copyright 2015-2022 Jason A. Donenfeld. All Rights Reserved. "WireGuard" and the "WireGuard" logo are registered trademarks of Jason A. Donenfeld.
© Copyright 2015-2022 Jason A. Donenfeld. All Rights Reserved. "WireGuard" and the "WireGuard" logo are registered trademarks of Jason A. Donenfeld.
Updated the ReyIst Git for
Tested on MikroTik RouterBOARD 951Ui-2nD (hAP) : OpenWrt 22.03.0-rc6
....ohh EOF or Easter Egg? Quick Run...Have needed web pages open for cheet sheets, make a current backup-OpenWrt-2022-now-now.tar.gz Flash your system (only if part of plan)..
Flash your system (only if part of plan).. ..SSH via Putty into 192.168.1.1
..SSH via Putty into 192.168.1.1 opkg update 
opkg install dnsmasq-full --download-only && opkg remove dnsmasq && opkg install dnsmasq-full --cache . && rm *.ipk  during the opkg sessions make use of time by copying item from your backup to your new install: IE
during the opkg sessions make use of time by copying item from your backup to your new install: IE rc.local crontab/root etc/config/system... 
opkg install diffutils curl jq ntpdate 
opkg install wireguard-tools luci-app-wireguard luci-proto-wireguard kmod-wireguard WinSCP into 192.168.1.1 and create
WinSCP into 192.168.1.1 and create /wg/ directory and move your keys.sh and sswg.json files, right click on script and set executable or cli chmod +x keys.sh. Check opkg and if done, run ./keys.sh -n till done;issue command wg show and  !! Navigate via WinSCP to
!! Navigate via WinSCP to /etc/config/network set the subnet you desire/save and REBOOT via Putty or the WinSCP Command windowlet. Release any device IP that got a dhcp addy from OpenWrt's install and kill your Putty/WinSCP session that were on the 192.168.1.0/24 subnet.
You will be better!
These Comments may be helpful for reference: