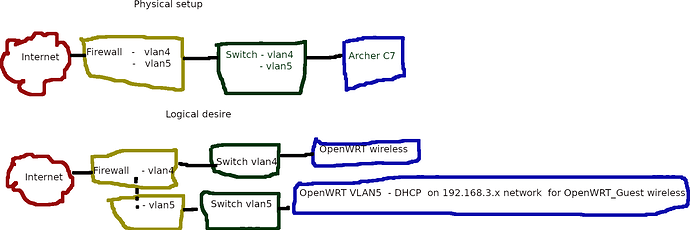
only partially. A diagram would really help if you aren't entirely certain how this is all going to come together. I still don't really understand how, in your specific network, VLANs 4 and 5 route to the internet. If they have internet access, they must obviously have a router that is handling those VLANs already. And if that it the case, does this device purely act as an AP and switch? or its it doing active routing?
I use IPFire.org firewall as my router. VLAN4 is my "Green" network and VLAN5 is my "Orange" or DMZ zone.
And while the port works on VLAN4, I'm not getting the wireless to work... Any thoughts on what I've goofed up?
config wifi-device 'radio0'
option type 'mac80211'
option path 'pci0000:00/0000:00:00.0'
option channel '36'
option band '5g'
option htmode 'VHT80'
option cell_density '0'
option country 'US'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'psk2'
option key 'Password'
option network 'vlan4'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/ahb/18100000.wmac'
option channel '1'
option band '2g'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdd0:fe45:0c99::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'eth0.2'
option macaddr 'd8:07:b6:74:13:d5'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 2'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
config device
option type '8021q'
option ifname 'eth0'
option vid '4'
option name 'eth0.4'
option ipv6 '0'
config interface 'vlan4'
option proto 'static'
option ipaddr '10.0.4.102'
option netmask '255.255.255.0'
option type 'bridge'
option device 'br-vlan4'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '4'
option ports '0t 1t 5'
config device
option type 'bridge'
option name 'br-vlan4'
list ports 'eth0.4'
I should also add... For this test that I'm doing, the AP is plugged into the switch and the port is configured to only allow tagged traffic for VLAN4 and VLAN5. I did test that and make sure it is working.
Remove the option type bridge from this section:
Have you verified that VLAN 4 (10.0.4.0/24) is setup properly and passing through the switch as expected? It is currently tagged on logical port 1 and untagged on logical port 5. So if you plug a device into the physical port that corresponds with logical port 5, does it get the connectivity you expect?
Whoo! OK. So the OpenWRT wireless now works on VLAN4 and one of the ports works on VLAN4.
So, your recommendation to have one VLAN working the way that I want it is now working!
So now, I'm going to duplicate that for VLAN5. The only difference there is that I will need DHCP but I can work with static IPs for it to get started.
cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'pci0000:00/0000:00:00.0'
option channel '36'
option band '5g'
option htmode 'VHT80'
option cell_density '0'
option country 'US'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'psk2'
option key 'Password'
option network 'vlan4'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/ahb/18100000.wmac'
option channel '1'
option band '2g'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdd0:fe45:0c99::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'eth0.2'
option macaddr 'd8:07:b6:74:13:d5'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 2'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
config device
option type '8021q'
option ifname 'eth0'
option vid '4'
option name 'eth0.4'
option ipv6 '0'
config interface 'vlan4'
option proto 'static'
option ipaddr '10.0.4.102'
option netmask '255.255.255.0'
option device 'br-vlan4'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '4'
option ports '0t 1t 5'
config device
option type 'bridge'
option name 'br-vlan4'
list ports 'eth0.4'
EDIT
Sorry. Got excited that it was working and forgot to answer your questions.
Have you verified that VLAN 4 (10.0.4.0/24) is setup properly and passing through the switch as expected?
Yes, I've verified that the port on the switch passes tagged ports properly.
It is currently tagged on logical port 1 and untagged on logical port 5. So if you plug a device into the physical port that corresponds with logical port 5, does it get the connectivity you expect?
It does!
Duplicated it.... and couldn't figure out why it wasn't working.... then remembered I had to set the country code. ![]()
So hooray! VLAN4 works the way I want, and VLAN5 is getting close! Just need to configure DHCP for the wireless clients on VLAN5 and any advice you might have for firewall (or if it is really needed since this is really a pass through device and I'm not really doing anything with the firewall).
I enabled DHCP on the interface and it created a DHCP server for me on my 10.0.5.x network... which isn't what I want from the wireless.... I use the 5 network for various playground projects and I do not want a DHCP server on that segment.
So what I'd like to do is configure wireless connections to get a 192.168.1.1 network range like it exists for br-lan but route outbound on the vlan5 configuration. But tomorrow... it's really late for me now. ![]()
Thanks for your help tonight! I've learned a ton!
cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'pci0000:00/0000:00:00.0'
option channel '36'
option band '5g'
option htmode 'VHT80'
option cell_density '0'
option country 'US'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'psk2'
option key 'Password'
option network 'vlan4'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/ahb/18100000.wmac'
option channel '1'
option band '2g'
option htmode 'HT20'
option cell_density '0'
option country 'US'
config wifi-iface 'default_radio1'
option device 'radio1'
option mode 'ap'
option ssid 'OpenWrt_n'
option network 'vlan5'
option encryption 'psk2'
option key 'Password'
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdd0:fe45:0c99::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'eth0.2'
option macaddr 'd8:07:b6:74:13:d5'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 2'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
config device
option type '8021q'
option ifname 'eth0'
option vid '4'
option name 'eth0.4'
option ipv6 '0'
config interface 'vlan4'
option proto 'static'
option ipaddr '10.0.4.75'
option netmask '255.255.255.0'
option device 'br-vlan4'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '4'
option ports '0t 1t 5'
config device
option type 'bridge'
option name 'br-vlan4'
list ports 'eth0.4'
config device
option type '8021q'
option ifname 'eth0'
option vid '5'
option name 'eth0.5'
option ipv6 '0'
config interface 'vlan5'
option proto 'static'
option ipaddr '10.0.5.75'
option netmask '255.255.255.0'
option device 'br-vlan5'
config device
option type 'bridge'
option name 'br-vlan5'
list ports 'eth0.5'
config switch_vlan
option device 'switch0'
option vlan '4'
option ports '0t 1t 4'
option vid '5'For VLAN 5, you need to choose if you want a DHCP server or not. You cannot have a situation where the wired clients on VLAN 5 get a DHCP server and the wireless ones don't. It is all or none. I'm not sure why you don't want a DHCP server on that network -- you can reserve plenty of space for static allocations, but it makes it easier for when you just want a plug-n-play type situation with devices connecting to that network.
I'm not entirely certain what you're asking here... yes, it is possible to use the 192.168.1.0/24 network for wireless devices. And it can be routed to the 10.0.5.0/24 network. There are two ways of doing this -- one involves setting up a static route on your primary router, and the other involves using masquerading on the vlan 5 zone.
Since they are bridged to a main router, VLANs 4 and 5 are both dumb APs on the C7. If you want DHCP served to those networks you'd do it on the main router.
It makes no sense to issue .1 DHCP addresses to devices on the .5 network. I guess you are talking about having a local .1 network which routes back to the main router at .5.1. This would be an entirely separate network from the others, and it is routed, not bridged.
In order for this router to route to .5 it needs to hold an IP on the .5 network.
What I'm after here would be something like this:
VLAN5 <-> Archer C7 <-> wireless DHCP of 192.168.1.1
And as I was thinking about it earlier this morning, I think I might know how to do it. Depending on how the day goes I may take a stab at it. Since this is a testing system I'm not in a hurry and this has been a fantastic learning experience.
Thanks for all the advice!
Just to be clear, these will necessarily be two different networks. Routing between them is not an issue, of course.
Right. That's what kinda hit me this morning. It seemed so obvious after a night of sleep. ![]()
So I had some issues with the 192.168.1.1/24 and I think it's because I was conflicting with br-lan. So I changed it to 192.168.3.1/24 and with the help of the Guest Wireless guide, I think I've got it working....
Any thoughts or feedback?
Also, since I am not using br-lan, what's the best way to "disable" it? I was going to set it to unmanaged and then assign all of the ports to either vlan4 or vlan5. Is that sufficient?
root@OpenWrt:/etc/config# cat dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
list server '10.0.5.103'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'guest'
option interface 'guest'
option start '100'
option limit '15'
option leasetime '1h'
option netmask '255.255.255.0'
list ra_flags 'none'
root@OpenWrt:/etc/config# cat firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config zone 'guest'
option name 'guest'
option network 'guest'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
config forwarding 'guest_wan'
option src 'guest'
option dest 'wan'
config rule 'guest_dns'
option name 'Allow-DNS-Guest'
option src 'guest'
option dest_port '53'
option proto 'tcp udp'
option target 'ACCEPT'
config rule 'guest_dhcp'
option name 'Allow-DHCP-Guest'
option src 'guest'
option src_port '68'
option dest_port '67'
option proto 'udp'
option family 'ipv4'
option target 'ACCEPT'
root@OpenWrt:/etc/config# cat network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdd0:fe45:0c99::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'eth0.2'
option macaddr 'd8:07:b6:74:13:d5'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 2'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
config device
option type '8021q'
option ifname 'eth0'
option vid '4'
option name 'eth0.4'
option ipv6 '0'
config interface 'vlan4'
option proto 'static'
option ipaddr '10.0.4.75'
option netmask '255.255.255.0'
option device 'br-vlan4'
list dns '10.0.5.103'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '4'
option ports '0t 1t 5'
config device
option type 'bridge'
option name 'br-vlan4'
list ports 'eth0.4'
config device
option type '8021q'
option ifname 'eth0'
option vid '5'
option name 'eth0.5'
option ipv6 '0'
config interface 'vlan5'
option proto 'static'
option ipaddr '10.0.5.75'
option netmask '255.255.255.0'
option device 'br-vlan5'
config device
option type 'bridge'
option name 'br-vlan5'
list ports 'eth0.5'
config switch_vlan
option device 'switch0'
option vlan '4'
option ports '0t 1t 4'
option vid '5'
config device 'guest_dev'
option type 'bridge'
option name 'br-guest'
list ports 'eth0.5'
config interface 'guest'
option proto 'static'
option device 'br-guest'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
list dns '10.0.5.103'
option delegate '0'
root@OpenWrt:/etc/config# cat wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'pci0000:00/0000:00:00.0'
option channel '36'
option band '5g'
option htmode 'VHT80'
option cell_density '0'
option country 'US'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'psk2'
option key 'Password'
option network 'vlan4'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/ahb/18100000.wmac'
option channel '1'
option band '2g'
option htmode 'HT20'
option cell_density '0'
option country 'US'
config wifi-iface 'default_radio1'
option device 'radio1'
option mode 'ap'
option ssid 'OpenWrt_n'
option network 'guest'
option encryption 'psk2'
option key 'Password'
Typically, this rule is setup as only the dest port.
You could have just used br-lan for this purpose. Unless your upstream is already 192.168.1.0/24, in which case you cannot use that subnet for the guest network. I still don't know your complete network topology, so I cannot comment beyond that.
If you're not using br-lan for anything, you can just delete the network definitions (device for br-lan, lan network interface, lan firewall zone (and associated rules) and lan from the DHCP file). Or you can leave it there -- it won't hurt anything. If you remove the switch, you can put them into the other VLANs, if you desire.
Typically, this rule is setup as only the dest port.
That makes sense. On the firewall rules I followed the guide on those.
Thanks again for your help! If there are no further suggestions then I'm going to clean up a few things then call it good enough as it's doing what I hoped it would be doing! Huzzah!
Welp, while trying to clean up and tweak firewall rules - I've really goofed things up. Good thing this is a learning experience! ![]()
So I'm not sure what I did to break my setup, but it was working. VLAN4 is still working as I want it to, the guest network routing out through VLAN5 is broken. However, VLAN5 itself is just fine. I tried to follow along with some other things I found in the forum. The latest was setting a vlan tag on the guest bridge... But honestly, that makes the least sense to me. Why tag the bridge to the interface that should be tagging it... But with it or without it, the setup is still broke.
What happens when I connect to the OpenWRT_Guest network is that the device gets a 192.168.3.x ip and I can ping any other device on the network, but it does NOT route out. I can't access anything on the 10.0.5.x network nor any internet beyond that.
So the two things I'm trying to wrap my head around are the path through the bridges and the firewall.
If I put the wireless on vlan5 directly it works with static IP (again, I don't want a DHCP on that range).
When I put wireless on the guest interface that goes to the br-guest device which then goes to the eth0.5 device which is really eth0 + the vlan5 tag. I believe I've mapped that correctly but whether that is the right path I'm not sure of. But supposing that is the right path, then it might be that I've got something borked in my firewall.
Any thoughts on where I went wrong?
Thanks!
root@OpenWRT:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
list server '10.0.5.103'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'guest'
option interface 'guest'
option start '100'
option limit '15'
option leasetime '1h'
option netmask '255.255.255.0'
list ra_flags 'none'
root@OpenWRT:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdd0:fe45:0c99::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config device
option name 'eth0.2'
option macaddr 'd8:07:b6:74:13:d5'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 2'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
config device
option type '8021q'
option ifname 'eth0'
option vid '4'
option name 'eth0.4'
option ipv6 '0'
config interface 'vlan4'
option proto 'static'
option netmask '255.255.255.0'
option device 'br-vlan4'
list dns '10.0.5.103'
option ipaddr '10.0.4.102'
option gateway '10.0.4.1'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '4'
option ports '0t 1t 5'
config device
option type 'bridge'
option name 'br-vlan4'
list ports 'eth0.4'
config device
option type '8021q'
option ifname 'eth0'
option vid '5'
option name 'eth0.5'
option ipv6 '0'
config interface 'vlan5'
option proto 'static'
option netmask '255.255.255.0'
option device 'br-vlan5'
option ipaddr '10.0.5.102'
list dns '10.0.5.103'
config device
option type 'bridge'
option name 'br-vlan5'
list ports 'eth0.5'
config switch_vlan
option device 'switch0'
option vlan '4'
option ports '0t 1t 4'
option vid '5'
config device 'guest_dev'
option type 'bridge'
option name 'br-guest'
list ports 'eth0.5'
config interface 'guest'
option proto 'static'
option device 'br-guest'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
list dns '10.0.5.103'
option delegate '0'
# This part is seriously questionable to me....
config bridge-vlan
option device 'br-guest'
option vlan '5'
list ports 'eth0:t*'
root@OpenWRT:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config zone 'guest'
option name 'guest'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'guest'
config forwarding 'guest_wan'
option src 'guest'
option dest 'wan'
config rule 'guest_dns'
option name 'Allow-DNS-Guest'
option src 'guest'
option dest_port '53'
option proto 'tcp udp'
option target 'ACCEPT'
config rule 'guest_dhcp'
option name 'Allow-DHCP-Guest'
option src 'guest'
option src_port '68'
option dest_port '67'
option proto 'udp'
option family 'ipv4'
option target 'ACCEPT'
root@OpenWRT:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'pci0000:00/0000:00:00.0'
option channel '36'
option band '5g'
option htmode 'VHT80'
option cell_density '0'
option country 'US'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option encryption 'psk2'
option network 'vlan4'
option ssid 'OpenWRT'
option key 'Password'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/ahb/18100000.wmac'
option channel '1'
option band '2g'
option htmode 'HT20'
option cell_density '0'
option country 'US'
config wifi-iface 'default_radio1'
option device 'radio1'
option mode 'ap'
option encryption 'psk2'
option ssid 'OpenWRT_Guest_n'
option key 'Password'
option network 'guest'
config wifi-iface 'wifinet2'
option device 'radio0'
option mode 'ap'
option ssid 'OpenWRT_Guest'
option encryption 'psk2'
option key 'Password'
option network 'guest'
I'm still confused about the "origin" of each of your VLANs... it appears that the guest network is VLAN 5, but you also have another network using VLAN 5.
Does the VLAN 5 exist on your upstream router, and is it your guest VLAN? If so, you don't need to do any routing for VLAN 5, just bridging wired and wireless.
You should not be tagging the bridge... this is relevant for devices that use DSA. Your router is still using swconfig. So what you've done is introduced invalid bridges into your network.
Simply stated, a bridge is effectively a software switch (L2). Firewall generally only acts on routed traffic (L3), so anything that is being passed through your device as a bridge (and not being routed by the OpenWrt device) is not going to interact with the firewall at all.
I see a bunch of issues with VLAN 5, but I cannot understand what your goal is with it. A diagram would be very useful here.
Not sure if this is much help. But here's the diagram.
I'm still confused about the "origin" of each of your VLANs... it appears that the guest network is VLAN 5, but you also have another network using VLAN 5.
From the firewall VLAN5 is just a DMZ separated from my home network where I set up various things I want to test and goof off with without risking breaking anything on my network where my family does stuff. The "guest" network I simply want to be a DHCP server for 192.168.3.x on the wireless side and a 10.0.5.x IP routing through to the vlan5 network. Which, the vlan5 network is functional right now and the DHCP server is working too. But the two pieces aren't talking properly.
You should not be tagging the bridge... this is relevant for devices that use DSA. Your router is still using swconfig. So what you've done is introduced invalid bridges into your network.
I thought it was wrong... I removed that.
Try modifying your test network configuration to look like this:
config interface 'guest'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
list dns '10.0.5.103'
option delegate '0'
Since guest is only wifi, remove this entirely:
The guest network routes through VLAN 5, so we need to assign the vlan5 network interface to a firewall zone with masquerading enabled.
config zone
option name 'vlan5'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'vlan5'
option masq '1'
Then we need to allow guest to route through VLAN5.
config forwarding 'guest_wan'
option src 'guest'
option dest 'vlan5'
You can remove this... it doesn't do anything because you don't have any networks assigned to the wan zone:
And if you want to prevent the guest network from accessing VLAN5 in general, you want to create a rule to drop all traffic to 10.0.5.0/24
config rule
option name 'drop-guest-to-vlan5'
list proto 'all'
option src 'guest'
option dest '*'
list dest_ip '10.0.5.0/24'
option target 'REJECT'
BTW, given that your main firewall already has VLANs configured, I'd actually recommend creating your guest network on another VLAN on the main router and then using your OpenWrt device as a VLAN aware dumb AP.
In other words, you could put 192.168.3.0/24 on your main router/firewall (maybe on VLAN3) and then simply switch/bridge it through for guest wifi.