Hello,
I continue to discover openwrt and I have a strange behaviour...
I create a VLAN 10 on interface 2 of my linksys
I disable the forward between my 2 network.
When I am connected tho the network 192.168.2.0 I can access to the 192.168.10.0
What's wrong with my configuration?
Disabling forward prevents connections originating on that network from forwarding it doesn't prevent them from replying to stuff originating elsewhere. To completely isolate a network prevent forwarding from other places to that network as well.
trendy
January 15, 2021, 2:43pm
3
You'll need to post your configuration first: uci export network; uci export firewall
1 Like
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdda:0d63:1557::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.2.1'
config interface 'wan'
option ifname 'eth1.2'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth1.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '3 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '10'
option ports '2 5t'
option vid '10'
config interface 'WAN_Nume'
option proto 'static'
option netmask '255.255.255.0'
option type 'bridge'
option ifname 'eth0.10'
option ipaddr '192.168.10.1'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option log '1'
option network 'lan'
option forward 'REJECT'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option input 'ACCEPT'
option forward 'REJECT'
option name 'WAN_Numeri'
option output 'ACCEPT'
option network 'WAN_Nume'
mikma
January 15, 2021, 3:57pm
5
And you mean devices in the 192.168.10.0/24 network? Access to any IP address of the OpenWrt router itself is controlled via the input setting of the source zone, i.e. the lan zone in the case above.
1 Like
trendy
January 15, 2021, 4:34pm
6
Configuration looks correct, can you show us the text output or a screenshot of the host in 192.168.2.X that can connect to the hosts in 192.168.10.X ?
trendy:
192.168.2.X
I reset router and try again....
When I am in the network 192.168.10.X I can access to the LuCi web interface on 192.168.2.X normal?
trendy
January 19, 2021, 9:01am
8
Very normal, the INPUT of the WAN_Numeri zone is ACCEPT.
1 Like
Thanks for the tips.
Any documentation about this system ?
trendy
January 19, 2021, 9:11am
10
About the firewall and more details on the configuration file
1 Like
Hello,
Thanks for the doc
When I compar the LuCI web interface switch and the file in /etc/config/network it's seems to be different :
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdfb:c58d:c11b::/48'
config interface 'wan'
option ifname 'eth1.2'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth1.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '14'
option ports '3t 5t'
config interface 'WAN_Nume'
option proto 'static'
option ifname 'eth0.14'
option type 'bridge'
option netmask '255.255.255.0'
option ipaddr '10.0.14.1'
config switch_vlan
option device 'switch0'
option vlan '4'
option vid '24'
option ports '2t 5t'
config interface 'LAN_Nume'
option proto 'static'
option ifname 'eth0.24'
option type 'bridge'
option netmask '255.255.255.0'
option ipaddr '10.0.24.1'
config switch_vlan
option device 'switch0'
option vlan '5'
option vid '54'
option ports '0 5t'
config interface 'LAN_Home'
option proto 'static'
option type 'bridge'
option netmask '255.255.255.0'
option ipaddr '10.0.34.1'
option ifname 'eth0.34'
option stp '1'
config switch_vlan
option device 'switch0'
option vlan '6'
option vid '34'
option ports '1t 5t'
config interface 'DMZ_Nume'
option proto 'static'
option type 'bridge'
option netmask '255.255.255.0'
option ipaddr '10.0.54.1'
option delegate '0'
option force_link '0'
option ifname 'eth0.54'
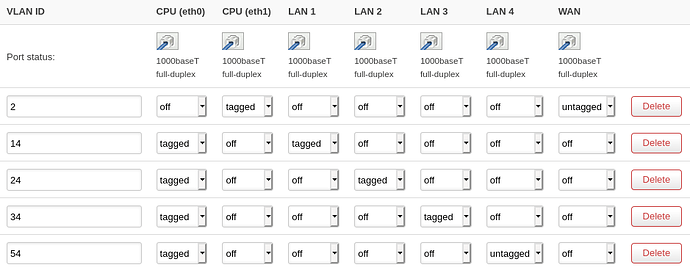
I don't really understand the "number" of ports in network config file :
trendy
January 21, 2021, 10:22am
12
From the mapping it seems that:
Whet a beautiful idea to invert the id of physicall port and number
Other question ... (Sorry I try to understand how openwrt work)
I have a DHCP server on 3 interface.
Problem with vlan ?
trendy
January 21, 2021, 10:56am
14
What is the output of uci export dhcp; uci export firewall ?
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'LAN_Home'
option interface 'LAN_Home'
option start '100'
option leasetime '12h'
option limit '150'
config dhcp 'LAN_Nume'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'LAN_Nume'
config dhcp 'DMZ_Nume'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'DMZ_Nume'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'ACCEPT'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
option input 'ACCEPT'
option log '1'
option forward 'REJECT'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option network 'WAN_Nume'
option input 'ACCEPT'
option name 'WAN_Nume'
option output 'ACCEPT'
option log '1'
option forward 'REJECT'
config zone
option network 'LAN_Nume'
option input 'ACCEPT'
option name 'LAN_Nume'
option output 'ACCEPT'
option log '1'
option forward 'REJECT'
config zone
option network 'LAN_Home'
option input 'ACCEPT'
option name 'LAN_Home'
option output 'ACCEPT'
option log '1'
option forward 'REJECT'
config forwarding
option dest 'wan'
option src 'LAN_Home'
config forwarding
option dest 'wan'
option src 'WAN_Nume'
config forwarding
option dest 'wan'
option src 'LAN_Nume'
config zone
option network 'DMZ_Nume'
option input 'ACCEPT'
option name 'DMZ_Nume'
option output 'ACCEPT'
option log '1'
option forward 'REJECT'
config redirect
option dest_port '80'
option name 'revproxy-80'
option src_dport '80'
option target 'DNAT'
option dest 'DMZ_Nume'
option src 'wan'
option dest_ip '10.0.54.11'
config redirect
option dest_port '443'
option src 'wan'
option name 'revproxy-443'
option src_dport '443'
option target 'DNAT'
option dest_ip '10.0.54.11'
option dest 'DMZ_Nume'
config nat
option src_port '80'
list proto 'tcp'
list proto 'udp'
option name 'Revproxy-80'
option dest_port '443'
option src 'wan'
option dest_ip '10.0.54.11'
option target 'ACCEPT'
config nat
option src_port '443'
option src 'wan'
option name 'Revproxy-443'
option target 'ACCEPT'
option dest_port '443'
list proto 'tcp'
list proto 'udp'
option dest_ip '10.0.54.11'
config forwarding
option dest 'wan'
option src 'DMZ_Nume'
trendy
January 21, 2021, 11:06am
16
It is correct, maybe the problem is elsewhere. If you connect a hot with static IP does it work?
Not working with a static ip.
I have a wifi network brige into this interface and in wifi I have a DHCP and internet connection
trendy
January 21, 2021, 11:16am
18
Then temporarily change from tagged to untagged, connect a PC directly without switch on the LAN3 port, and check again.
I change to untagged and my computer directly take a DHCP lease.
What is the problem ?
trendy
January 21, 2021, 11:29am
20
Obviously the device that you connect there doesn't understand tagged frames.