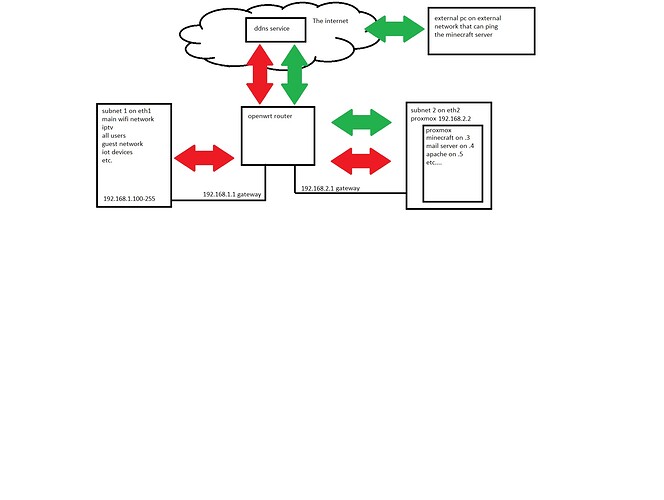
okey i have my network layout drawn., i dont know if this is even possible but:
i can reach my server trough the firewall on a external device on a external network (Green arrows)
But i can't reach (even ping) the servers trough the ddns back from a different subnet (red arrows)
(so the data example minecraft needs to go through the router then to look up the ddns send the data back to the router then the router needs to send the data to the different subnet where the server is located and ofcource all the way back)
here is my network, firewall and ddns configs i really dont know if this is even possible but i can't find the problem. i can if i port forward the subnet ip to the each other reach the server without any problem.
does someone know if this is possible? also why the subnets and proxmox?
im always tinkering inside openwrt and try to fine tune it, build images with configs and firmware already inside. but also want to make a secure place for the home network. so the idea is to use proxmox to create different virtual machines that run different uses to make whit its own firewalls and only open the service needs. im not really great in home security and if it works i find a way to break my own setup and ending up reinstalling the complete machine again. this runs backups and if i mess something up i dont need reinstall the whole machine just the virtual machine where i messed something up.
im still learning linux ![]()
ddns:
config ddns 'global'
option ddns_dateformat '%F %R'
option ddns_loglines '250'
option ddns_rundir '/var/run/ddns'
option ddns_logdir '/var/log/ddns'
config service 'myddns_ipv4'
option enabled '1'
option use_ipv6 '0'
option service_name 'nothinghere'
option lookup_host 'nothinghere'
option domain 'nothinghere.ddns.net'
option username 'nothinghere'
option password 'nothinghere'
option ip_source 'network'
option ip_network 'wan'
option interface 'wan'
option use_syslog '2'
option check_unit 'minutes'
option force_unit 'minutes'
option retry_unit 'seconds'
Network:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'nothinghere' #dont even know what this does just to be sure
config interface 'alles'
option device 'eth1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option type 'bridge'
config interface 'server'
option device 'eth2'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option ip6assign '60'
option type 'bridge'
list dns '192.168.2.1'
config interface 'wan'
option proto 'dhcp'
option type 'bridge'
option device 'eth0.300'
#some wg_interfaces deleted nothing intresting for this problem
Firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'alles_zone'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'alles'
config zone
option name 'server_zone'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'server'
option masq '1'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'alles_zone'
option dest 'wan'
config forwarding
option src 'server_zone'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option proto 'esp'
option target 'ACCEPT'
option dest 'alles_zone'
config rule
option name 'Allow-IPSec-ESP2'
option src 'wan'
option proto 'esp'
option target 'ACCEPT'
option dest 'server_zone'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
option dest 'alles_zone'
config rule
option name 'Allow-ISAKMP2'
option src 'wan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
option dest 'server_zone'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config rule
option name 'proxmox'
option target 'ACCEPT'
list proto 'tcp'
list dest_ip '192.168.2.2'
option src 'alles_zone'
option dest 'server_zone'
option enabled '0'
config rule 'wg'
option src 'wan'
option dest_port '51820'
option proto 'udp'
option target 'ACCEPT'
option name 'Allow-WireGuard-subnet'
config forwarding
option src 'gasten_zone'
option dest 'wan'
config zone
option name 'gasten_zone'
option input 'DROP'
option forward 'DROP'
list network 'wg_gast'
option output 'DROP'
option masq '1'
config redirect
option target 'DNAT'
option name 'minecraft server'
option src 'wan'
option src_dport '25565'
option dest 'server_zone'
option dest_ip '192.168.2.3'
option dest_port '25565'