xenDE
September 11, 2021, 9:22pm
1
Hi,
I have a routing problem on my OpenWRT GL-AR300M.
I use the OpenWRT Router (10.123.0.1/24) with the WAN-RJ45 port on my NAT-home-internet-router(fritzbox 192.168.11.1/24)
The OpenWRT autoconnects 2 VPNs:
as WireGuard client to a WireGuard Server (116.203.xx.xx) for all Traffic
as vpnc Client to a AVM Fritzbox (84.140.xx.xx) for connect to my office net (10.111.0.0/16)
All works fine, I surf the internet over the WireGuard endpoint and can connect to devices in the office over the vpnc.
problem:
my routing table:
$ route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default * 128.0.0.0 U 0 0 0 wg0
default wpad.fritz.box 0.0.0.0 UG 10 0 0 eth0
default wpad.fritz.box 0.0.0.0 UG 20 0 0 eth0
10.111.0.0 10.111.0.1 255.255.0.0 UG 0 0 0 vpn-TUN0
10.123.0.0 * 255.255.255.0 U 0 0 0 br-lan
84.140.xx.xx wpad.fritz.box 255.255.255.255 UGH 10 0 0 eth0
116.203.xx.xx wpad.fritz.box 255.255.255.255 UGH 0 0 0 eth0
128.0.0.0 * 128.0.0.0 U 0 0 0 wg0
172.16.16.0 * 255.255.255.0 U 0 0 0 wg0
192.168.11.0 * 255.255.255.0 U 10 0 0 eth0
192.168.11.0 * 255.255.255.0 U 20 0 0 eth0
$ traceroute 84.140.xx.xx
traceroute to 84.140.xx.xx, 64 hops max, 52 byte packets
1 console.gl-inet.com (10.123.0.1) 1090.792 ms 1.041 ms 0.921 ms
2 * * *
ends here
172.16.x.x is the WireGuard transport net
I need to ssh 84.140.xx.xx while VPN is running.
best regards,
edit/add: OpenWrt 19.07.7, r11306-c4a6851c72
trendy
September 11, 2021, 9:33pm
2
One thing, irrelevant to your issue is that you have two default gateways:
Apart from that, since you have a route for the 84.140 and vpnc works, then it is not a routing issue.
1 Like
xenDE
September 11, 2021, 9:56pm
3
trendy:
Apart from that, since you have a route for the 84.140 and vpnc works, then it is not a routing issue.
if i stop the "TUN0" (VPNC (CISCO 3000 (and others) VPN)) interface:
no ping working for clients (* ping from router always working)
routing entry removed:10.111.0.0 10.111.0.1 255.255.0.0 UG 0 0 0 vpn-TUN0
*) sorry, I forgot to mention that the ping from the router is working, only the clients (wifi) on my openwrt can not ping the 84.140.xx.xx
I admin the vpnc endpoint too, but its only a avm fritzbox (closed source, no ssh)
trendy
September 11, 2021, 10:00pm
4
What is the output of uci export firewall ?
1 Like
xenDE
September 11, 2021, 10:09pm
5
WireGuard+vpnc is on, can ping endpoint and private IP at the endpoint:
# wget -O- https://19216801.de/ip/?plain 2> /dev/null
116.203.xx.xx
# ping 10.111.0.1
PING 10.111.0.1 (10.111.0.1): 56 data bytes
64 bytes from 10.111.0.1: seq=0 ttl=64 time=14.088 ms
64 bytes from 10.111.0.1: seq=1 ttl=64 time=12.605 ms
64 bytes from 10.111.0.1: seq=2 ttl=64 time=12.061 ms
^C
--- 10.111.0.1 ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max = 12.061/12.918/14.088 ms
# ping 84.140.xx.xx
PING 84.140.xx.xx (84.140.xx.xx): 56 data bytes
64 bytes from 84.140.xx.xx: seq=0 ttl=60 time=12.196 ms
64 bytes from 84.140.xx.xx: seq=1 ttl=60 time=9.810 ms
64 bytes from 84.140.xx.xx: seq=2 ttl=60 time=10.309 ms
^C
--- 84.140.xx.xx ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max = 9.810/10.771/12.196 ms
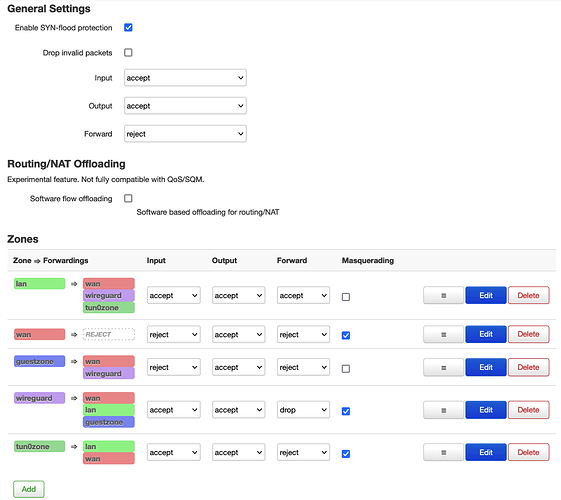
root@my-local-route:~# uci export firewall
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'TUN0 lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wwan'
config forwarding
option src 'lan'
option dest 'wan'
option enabled '1'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
option reload '1'
config include 'glfw'
option type 'script'
option path '/usr/bin/glfw.sh'
option reload '1'
config zone 'guestzone'
option name 'guestzone'
option network 'guest'
option forward 'REJECT'
option output 'ACCEPT'
option input 'REJECT'
config forwarding 'guestzone_fwd'
option src 'guestzone'
option dest 'wan'
option enabled '1'
config rule 'guestzone_dhcp'
option name 'guestzone_DHCP'
option src 'guestzone'
option target 'ACCEPT'
option proto 'udp'
option dest_port '67-68'
config rule 'guestzone_dns'
option name 'guestzone_DNS'
option src 'guestzone'
option target 'ACCEPT'
option proto 'tcp udp'
option dest_port '53'
config rule 'sambasharewan'
option src 'wan'
option dest_port '137 138 139 445'
option dest_proto 'tcpudp'
option target 'DROP'
config rule 'sambasharelan'
option src 'lan'
option dest_port '137 138 139 445'
option dest_proto 'tcpudp'
option target 'ACCEPT'
config include 'gls2s'
option type 'script'
option path '/var/etc/gls2s.include'
option reload '1'
config include 'glqos'
option type 'script'
option path '/usr/sbin/glqos.sh'
option reload '1'
config rule 'AllowWireguard'
option name 'Allow-Wireguard'
option target 'ACCEPT'
option src 'wan'
option proto 'udp tcp'
option family 'ipv4'
option dest_port '47824'
config zone 'wireguard'
option name 'wireguard'
option forward 'DROP'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option device 'wg0'
option masq6 '1'
config forwarding 'wireguard_wan'
option src 'wireguard'
option dest 'wan'
config forwarding 'wireguard_lan'
option src 'wireguard'
option dest 'lan'
option enabled '0'
config forwarding 'lan_wireguard'
option src 'lan'
option dest 'wireguard'
config forwarding 'guest_wireguard'
option src 'guestzone'
option dest 'wireguard'
config forwarding 'wireguard_guest'
option src 'wireguard'
option dest 'guestzone'
config rule 'safe_mode_lan'
option name 'safe_mode_lan'
option proto 'all'
option src 'lan'
option dest 'wan'
option target 'DROP'
config rule 'safe_mode_guest'
option name 'safe_mode_guest'
option proto 'all'
option src 'guestzone'
option dest 'wan'
option target 'DROP'
config zone
option network 'TUN0'
option name 'tun0zone'
option mtu_fix '1'
option forward 'REJECT'
option masq '1'
option output 'ACCEPT'
option family 'ipv4'
list subnet '10.111.0.0/16'
option input 'ACCEPT'
config forwarding
option dest 'tun0zone'
option src 'lan'
config forwarding
option dest 'lan'
option src 'tun0zone'
config forwarding
option dest 'wan'
option src 'tun0zone'
don't know if screenshots helps too:
trendy
September 11, 2021, 10:40pm
6
So the only problem is that you cannot ping the fritzbox from a lan host, but it works when you ping from the OpenWrt, right?ip -4 ruopkg update; opkg install tcpdump; tcpdump -i PHY_IF -evn 84.140....
1 Like
xenDE
September 11, 2021, 10:47pm
7
yes
root@my-local-route:~# ip -4 ru
0: from all lookup local
31: from all fwmark 0x60000/0x60000 lookup 31
1002: from all iif br-wwan [detached] lookup 2
2002: from all fwmark 0x200/0x3f00 lookup 2
2061: from all fwmark 0x3d00/0x3f00 blackhole
2062: from all fwmark 0x3e00/0x3f00 unreachable
32766: from all lookup main
32767: from all lookup default
tcpdump tomorrow, need some sleep now.
thanks for your help!
trendy
September 11, 2021, 10:48pm
8
How did you setup the policy routing?
1 Like
xenDE
September 11, 2021, 10:52pm
9
dont know what you mean, can you explain?
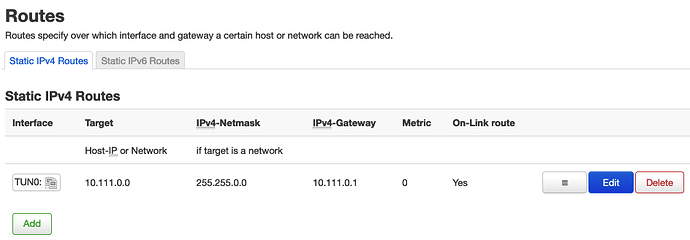
one more thing, i set up this stgatic route on the webinterface:
trendy
September 11, 2021, 11:13pm
10
It is evident from the output of ip rules above that you have added some policy based routing rules, which change routing decisions based on source address or other factors.
This doesn't look right. The gateway is not part of the target network, but an IP which is directly connected to the interfaces of the router. For example the fritzbox vpnc interface IP.
1 Like
xenDE
September 12, 2021, 10:41am
11
i have not added any policies imho.
but:
i added the static route for the vpnc network, because the starting of vpnc does not generate a route for the net.
i think best i reset the router and starting from scratch.
xenDE
September 12, 2021, 2:32pm
12
looks like a fresh install fixed the problem.
my steps:
install: mc luci-proto-vpnc luci-app-wireguard vpn-policy-routing
config LAN IP/16 + DHCP and wireless network, remove WAN6 interface (no IP6 needed)
reboot
new interface TUN0 as VPNC
vpnc connection is working, now I can ping in the VPN and I can access the VPN endpoint public IP.
root@my-local-route:~$ ping -I vpn-TUN0 10.111.0.12
PING 10.111.0.12 (10.111.0.12): 56 data bytes
64 bytes from 10.111.0.12: seq=0 ttl=63 time=13.936 ms
64 bytes from 10.111.0.12: seq=1 ttl=63 time=13.445 ms
^C
--- 10.111.0.12 ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 13.445/13.690/13.936 ms
Now I need a solution for create the route after VPN connect.
trendy
September 12, 2021, 8:11pm
13
Keep in mind that this is the OpenWrt forum. For support of firmwares from other vendors, you'll have better luck asking in the designated forum or support pages.
2 Likes
system
September 22, 2021, 8:12pm
14
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.