Timed out
The thing is that the current configuration on peers and WG server allows me to access from Internet to both networks with my phone (what is essential), so i am a bit afraid of change something ![]()

Timed out
The thing is that the current configuration on peers and WG server allows me to access from Internet to both networks with my phone (what is essential), so i am a bit afraid of change something ![]()
I assume your phone is connecting to the router in network A? There doesn't appear to be a peer config for the phone in network B.
If that's the case, then the one peer in network B should have the following allowed IPs:
192.168.9.1/32192.168.9.3/32192.168.2.0/24The 'Proxmox' peer in network A should have:
192.168.9.2/32192.168.1.0/24And, the phone peer in network A should have:
192.168.9.3/32While it might not be the cause of the current issues it'd be ideal to ensure the configs are correct before proceeding further. You should also install tcpdump on the wireguard devices in network A and B so can start doing some packet captures.
I think it does make sense to point out a comment I made in the other thread about this topic:
I suspect that a large part of the issue with the connectivity here is related to the proxmox system and its configuration with respect to routing. Fundamentally, if there was an OpenWrt (bare metal) device at that site, things would be much easier. But the proxmox environment adds quite a bit of additional complexity with routing.
The phone has connection from everywhere, i can connect both network with data plan of ISP, as the diagram shows.
I think this is not necessary because i want, most of all, to connect from phone to both nets.
Ok, i will do it when i arrive home. I have to make sure to not lose access to A from phone (in that case i have i wait 1 week to arrive again to A)
I suposse in that case that is the problem the routing table of the Proxmox system, i can add any route entry in that host that makes me have access from B to A. Dont you hink so?
Do you have a specific peer config in network B (and a corresponding one on the phone) for your phone? If not then the connection is being made to network A regardless of what you can access once it's made. And the peer configs should be updated to reflect the correct allowed IPs.
The configuration of the only pair I have in B, is in the post above.
Phone settings are here:
(Sorry for that edit, im not at home)
Right, so the phone connects to A and accesses B through the wireguard tunnel between A and B. It has no direct connection to B. This means the allowed IPs on the peers should be as I set out above. As you only need to change the peer configs for the A to B tunnel it won't change anything to do with your phone's access to A.
Sorry for the long wait, i didnt have any time to test.
So, do i need to do this then?
Should i do this changes in the server too?
Remember that i need to have access from the Phone Peer to A and B networks and i want to have access from network B to A. Access from A to B is done
Yes, you should ensure the wireguard config at each location contains an accurate list of allowed ips.
And what if i configure a Site To Site Wireguard? Could i access that network from my mobile? will be easier?
I have buyed a RPI4 and installed OpenWRT 23.0.5, if i configure that RPI as site A, and my remote router as site B, could i add a peer somewhere in A or B and have access to A and B at the same time (from my phone) and have access from computers from A to B and B to A?
Your phone would be C, it would be a peer of either A or B. If the site to site network is configured for symmetric routing, an additional peer C could access both the A and B LANs regardless of which site it is peered with.
Is that not essentially what you already have? Just changing one of the existing routers to an rpi4?
I dont know, to be honest. I only have one WG Server. With the PtP Wireguard i should have 2 servers, right?
I dont think so by the way because i can access from A to B but not from B to A
Do you mean adding the static route in A and B, right?
Oh, and by the way, "the one peer in network B" is the same as "The 'Proxmox' peer"
Anyways i have one OpenWRT device now.
There's no such thing as a server in wireguard. Every peer is equivalent. As I understand it, your current setup is A and B are direct peers. A and C (your phone) are also peers. The allowed IPs in my earlier post would (based on the IP information you provided) allowed A, B, and C to access each other.
That is wrong, if i change the IP 192.168.9.2/32 for 192.168.9.1/32 i lose access from C to Proxmox peer in B
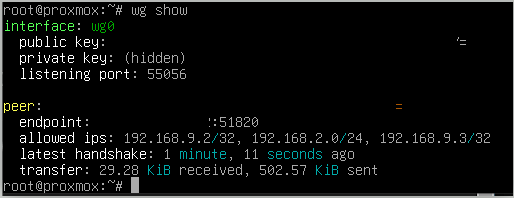
Then the information you've previously provided is wrong. For each device A, B, and C what is the allocated WG address? For A and B what is the LAN subnet?
Ok, there i go:
Net A, LAN subnet 192.168.2.0/24
Peers:
Net B, LAN subnet 192.168.1.0/24
RPI4 with IP 192.168.1.253 on net B running OpenWRT
Peers:
Proxmox peers:
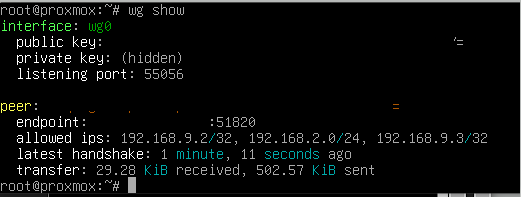
iPhone Peers:
I have added a new peer to my PC on Windows that is allowing me to connect to A in 192.168.2.1:
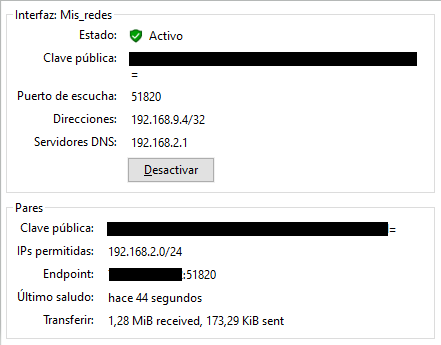
I think i dont forget anything.
Your setup is a mess. A and B (assuming they are the two 'sites') should have a single device in them (ideally the default gateway) running wireguard and allowing access to the local subnet. Any other devices within those sites should not be running wireguard and connecting to the other site. Remote devices should connect to one of the two 'fixed' sites and have the necessary allowed IPs added to the A-B peers to allow access to both sites.
Also, please don't post screenshots if at all possible. Copy and paste from config files, adding as 'preformatted text' to your post
It is ![]()
Do you mean that Wireguard on A shoud have only the B subnet IP and B should have only A subnet IP, right?
So on my Phone, i should have the A and B IP subnet IPs? Or all the IPs on the Wireguard "system"?
No.
Also, no. I'm not entirely sure how you've got that from what I said.
Start with setting up a working site to site VPN between A and B. Once you've got that you can start thinking about adding additional peers to allow remote devices access.