Easiest way setup second WiFi, for your son, disable it at night.
Which you can do on the Archer C7 by adding a second SSID, without needing another router.
You'll want to remember change passwords on the "old" SSID, since he'll probably figure out pretty quickly to log in to that one if it is the one that is up when "his" isn't.
If the problem is wired, then you'll at a minimum need to set a fixed IP on his machine and block that IP address. If he's smart, he'll set a static IP on his machine, so you'd need to get him on his own VLAN and own physical cable (since, like IP addresses, VLAN tags can be set by the host).
Hello,
Jeff, rj-45, thank you for your answers!
I don't use WIFI. My son talk on discord via his computer connected by Ethernet.
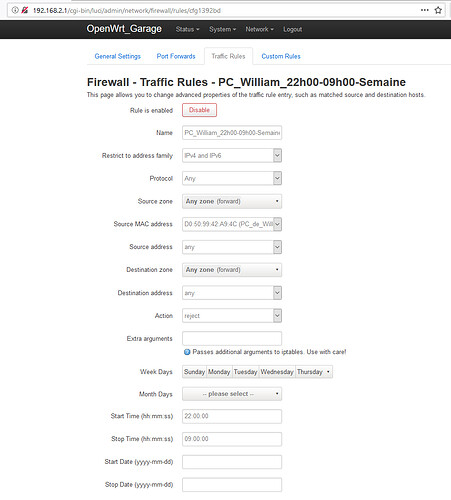
I have create a rule like this to cute connection from 22h00 to 09:00 from Monday to Thursday :
A print Screen:
The rule in a file :
config rule
option name 'PC_William_22h00-09h00-Semaine'
option src '*'
option src_mac 'D0:50:99:42:A9:4C'
option start_time '22:00:00'
option stop_time '09:00:00'
option proto 'all'
option target 'REJECT'
option weekdays 'Sun Mon Tue Wed Thu'
option dest '*'
Internet is cut at 22:00 but discord still works.
What can I do please?
Restart the firewall at 22:00.
Hello,
Thank you for your answer IIeachii!
I will try but can you explain to me how can I do this automatically?
Regards.
https://openwrt.org/packages/pkgdata/kmod-ipt-ipopt
Is required for time based iptables rules do you have it installed?
Hello,
Thank you dlakelan
Yes the pakage " kmod-ipt-ipopt" version 4.9.120-1 is installed:
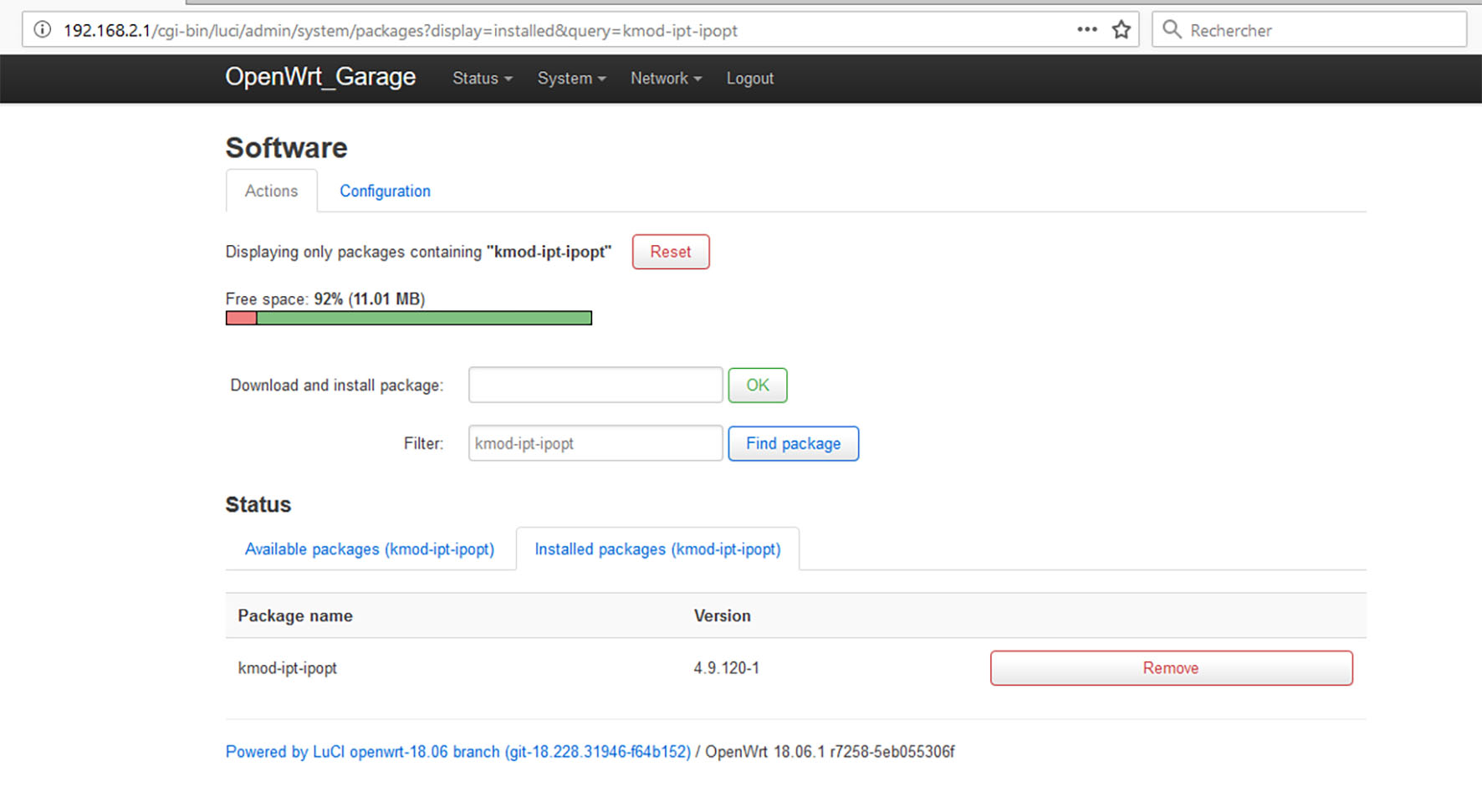
Time based rules in Firewall works to block intenet acces (online games for exemple) but not for VoIP like "Discord".
Have you any idea. Perhapps I have to configure something on the package "kmod-ipt-ipopt"?
Regards.
I tried with my router to block traffic from a host and for existing connections (ping some host on the wan side) the traffic wasn't blocked but it wasn't possible to start new connections.
So there must be a way to stop the traffic from the host?!?
Can you clarify this statement?
I think this may be the same reason I advised the OP to restart the firewall.
I made a scheduled firewall rule that should block pakets from one host (host a) in the lan zone send to one other zone, in this case the wan zone
config rule
option enabled '1'
option src 'lan'
option name 'block_test'
option src_mac 'aa:aa:aa:aa:aa:aa'
option weekdays 'Sat'
option start_date '2019-01-05'
option stop_date '2019-01-06'
option target 'DROP'
option proto 'all'
option start_time '10:12:00'
option stop_time '10:13:00'
option dest 'wan'
from that blocked host a I started pinging host b (a host in zone wan) before the scheduled firewall rule starts
these ping pakets are successful, even after the firewall should block it
when I try to ping host b from host a in the blocked time frame no pings were successful
Correct. It was Established/Related traffic prior to the rule taking effect!
okay, than I think this is the "problem" with discord. the discord session was established before the firewall blocking time frame.
Is there a way to "reset" firewall. In my case
/etc/init.d/firewall restartdidn't work
on the other hand, I thought that every ping is a new "session" so that the firewall has to look into every paket?!?
What does reload do?
Nope, you're forgetting the sequence number of the pings. ![]()
And we're not talking about "sessions," that's only a close synonymy of Established/Related in the case of TCP.
same result like restart
I know that, that is why I put the word session in question marks
Hello,
I'm glad to see that some body talk about my problem.
But, I'm French, I don't understand very well; do you have a solution for me?
Regards.
untill now I don't see any quick solution.
Somehow getting the rule to be executed before the check for established/related traffic would work but it will require some looking carefully at how and where to put the rule.
Something like this
iptables -I FORWARD -m mac --mac-source xx:xx:xx:xx:xx:xx -m conntrack --ctstate ESTABLISHED,RELATED -j DROP
and this to allow access again:
iptables -D FORWARD -m mac --mac-source xx:xx:xx:xx:xx:xx -m conntrack --ctstate ESTABLISHED,RELATED -j DROP