I'm using OpenWRT routers as Wireguard_client which will be connected to a wireguard_server having public IP.
I was trying to block site to site communication, for example: 10.0.0.1 should be able to communicate with only 10.0.0.5, and 10.0.0.1 should not be able to communicate with 10.0.0.2, 10.0..0.3 and 10.0.0.4. similarly 10.0.0.2, 10.0.0.3 and 10.0.0.4 should communicate only with 10.0.0.5.
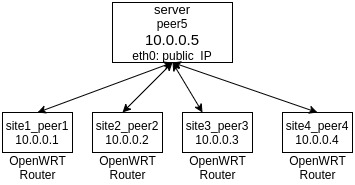
Below is the server configuration.
[Interface]
PrivateKey = <PrK>
Address = 10.0.0.5/24
ListenPort = 51820
PostUp = iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = <PbKey>
AllowedIPs = 10.0.0.1/32
[Peer]
PublicKey = <PbKey>
AllowedIPs = 10.0.0.2/32
[Peer]
PublicKey = <PbKey>
AllowedIPs = 10.0.0.3/32
[Peer]
PublicKey = <PbKey>
AllowedIPs = 10.0.0.4/32
And below is the configuration of one of the site i.e site1 _peer1
[Interface]
PrivateKey = <PrKey>
Address = 10.0.0.1/32
[Peer]
PublicKey = <PbKey>
AllowedIPs = 10.0.0.5/32
Endpoint = <public_IP_of_server_peer5>:<port>
PersistentKeepalive = 25
With this configuration, I'm able to ping only 10.0.0.5 and not other(10.0.0.2, 10.0.0.3,10.0.04)
but when I try:
ping -I wg0 8.8.8.8
I get the below error, What I'm doing wrong?. I want all the traffic frrom wg0 should go to server_peer5 and then it should leave from the eth0 of the server_peer5
root@174e60689eba:/# ping -I wg0 8.8.8.8
PING 8.8.8.8 (8.8.8.8) from 10.0.0.1 wg0: 56(84) bytes of data.
From 20.0.0.1 icmp_seq=1 Destination Host Unreachable
From 20.0.0.1 icmp_seq=1 Destination Host Unreachable
From 20.0.0.1 icmp_seq=1 Destination Host Unreachable
From 20.0.0.1 icmp_seq=1 Destination Host Unreachable
ping: sendmsg: Required key not available