Yes, my patch is based on xt_flow_offload which firewall3 is using.
Many thanks for your contribution. I used your new patch (slighty modified) with a new 5.15 build and indeed the CPU usage is close to zero ![]() when using an ethernet-connected client (previously the CPU usage was even higher than for WLAN clients).
when using an ethernet-connected client (previously the CPU usage was even higher than for WLAN clients).
But for WLAN clients the CPU usage is still the same like your previous fix for PPPoE (with wed enabled), about 25% when download and 50% when uploading. Also I noticed after the ethernet test that the bridger process started to consume 50% CPU so I restarted it, don't know what caused this. I really hope now that you've managed to discover the PPPoE issue, Felix will look into it and make a final hw offloading patch that applies also to PPPoE and doesn't break other packages.
It's normal that wan->wifi consume 25% cpu. Stock firmware also consume some cpu usage during wan->wifi test. This patch only fix the wire performance issue.
Bridger is only about lan->wifi offload. If it works, you can see some bind from cat /sys/kernel/debug/mtk_ppe/bind during lan->wifi speedtest.
The default profile needs to be modified (delete # like this) to make bridger works correctly. I haven't meet the situation that bridger process consumes a lot of cpu usage.
i have download a last version for rt3200 work very well
the packages is donwloadable everywhere with this version you know ?
openwrt 22.03.0 rc1 e19302
Anyone know when we'll get brave and swap out 5.10 for 5.15 for these chipsets by default for master? Seems like it is pretty stable but I'm sure I'm not touching sections that other people do (like PPPoE).
Hi, does anyone know if RT3200 support jumbo frames wan-side (I need 1540 MTU to overcome encapsulation overhead)?
If it does not, is it a driver or hardware issue?
I tried raising MTU in luci but it seems not working well
Hi everybody do you have a news about UPNP on this router ?
I try work with nftables but always not
Thanks
Just double-checking, but I assume after using the owrt-ubi-installer, it’s fine to upgrade to newer OpenWrt versions with just the ubi-sysupgrade.itb?
For instance, with the 22.03-rc1, openwrt-22.03.0-rc1-mediatek-mt7622-linksys_e8450-ubi-squashfs-sysupgrade.itb?
Yes, the installer is only needed once for changing the u-boot bootloader and creating the recovery partition/instance.
After that it is quite normal sysupgrading with the ubi sysupgrade image.
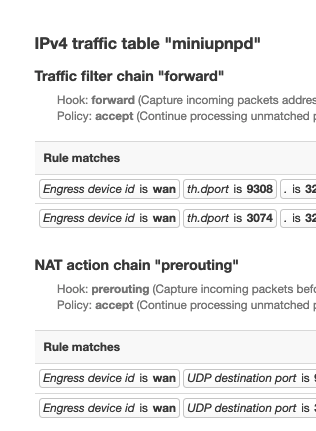
hi everybody my upnp rework with the last snapshot of rt3200 and miniupnp nftables 2.2.3.1
i has modem router + router openwrt
so in usr/share .... ruleset.uc i has apply this patch
like this
{% let flowtable_devices = fw4.resolve_offload_devices(); -%}
table inet fw4
flush table inet fw4
{% if (fw4.check_flowtable()): %}
delete flowtable inet fw4 ft
{% endif %}
table inet fw4 {
{% if (length(flowtable_devices) > 0): %}
#
# Flowtable
#
flowtable ft {
hook ingress priority 0;
devices = {{ fw4.set(flowtable_devices, true) }};
{% if (fw4.default_option("flow_offloading_hw")): %}
flags offload;
{% endif %}
}
{% endif %}
#
# Set definitions
#
{% for (let set in fw4.ipsets()): %}
set {{ set.name }} {
type {{ fw4.concat(set.types) }}
{% if (set.maxelem > 0): %}
size {{ set.maxelem }}
{% endif %}
{% if (set.timeout >= 0): %}
timeout {{ set.timeout }}s
{% endif %}
{% if (set.interval): %}
flags interval
auto-merge
{% endif %}
{% fw4.print_setentries(set) %}
}
{% endfor %}
#
# Defines
#
{% for (let zone in fw4.zones()): %}
{% if (length(zone.match_devices)): %}
define {{ zone.name }}_devices = {{ fw4.set(zone.match_devices, true) }}
{% endif %}
{% if (length(zone.match_subnets)): %}
define {{ zone.name }}_subnets = {{ fw4.set(zone.match_subnets, true) }}
{% endif %}
{% endfor %}
#
# User includes
#
include "/etc/nftables.d/*.nft"
#
# Filter rules
#
chain input {
type filter hook input priority filter; policy {{ fw4.input_policy(true) }};
iifname "lo" accept comment "!fw4: Accept traffic from loopback"
ct state established,related accept comment "!fw4: Allow inbound established and related flows"
{% if (fw4.default_option("drop_invalid")): %}
ct state invalid drop comment "!fw4: Drop flows with invalid conntrack state"
{% endif %}
{% if (fw4.default_option("synflood_protect") && fw4.default_option("synflood_rate")): %}
tcp flags & (fin | syn | rst | ack) == syn jump syn_flood comment "!fw4: Rate limit TCP syn packets"
{% endif %}
{% for (let rule in fw4.rules("input")): %}
{%+ include("rule.uc", { fw4, rule }) %}
{% endfor %}
{% for (let zone in fw4.zones()): for (let rule in zone.match_rules): %}
{%+ include("zone-jump.uc", { fw4, zone, rule, direction: "input" }) %}
{% endfor; endfor %}
{% if (fw4.input_policy() == "reject"): %}
jump handle_reject
{% endif %}
}
chain forward {
type filter hook forward priority filter; policy {{ fw4.forward_policy(true) }};
{% if (length(flowtable_devices) > 0): %}
meta l4proto { tcp, udp } flow offload @ft;
{% endif %}
ct state established,related accept comment "!fw4: Allow forwarded established and related flows"
{% if (fw4.default_option("drop_invalid")): %}
ct state invalid drop comment "!fw4: Drop flows with invalid conntrack state"
{% endif %}
{% for (let rule in fw4.rules("forward")): %}
{%+ include("rule.uc", { fw4, rule }) %}
{% endfor %}
{% for (let zone in fw4.zones()): for (let rule in zone.match_rules): %}
{%+ include("zone-jump.uc", { fw4, zone, rule, direction: "forward" }) %}
{% endfor; endfor %}
{% if (fw4.forward_policy() == "reject"): %}
jump handle_reject
{% endif %}
}
chain output {
type filter hook output priority filter; policy {{ fw4.output_policy(true) }};
oifname "lo" accept comment "!fw4: Accept traffic towards loopback"
ct state established,related accept comment "!fw4: Allow outbound established and related flows"
{% if (fw4.default_option("drop_invalid")): %}
ct state invalid drop comment "!fw4: Drop flows with invalid conntrack state"
{% endif %}
{% for (let rule in fw4.rules("output")): %}
{%+ include("rule.uc", { fw4, rule }) %}
{% endfor %}
{% for (let zone in fw4.zones()): for (let rule in zone.match_rules): %}
{%+ include("zone-jump.uc", { fw4, zone, rule, direction: "output" }) %}
{% endfor; endfor %}
{% if (fw4.output_policy() == "reject"): %}
jump handle_reject
{% endif %}
}
chain handle_reject {
meta l4proto tcp reject with {{
(fw4.default_option("tcp_reject_code") != "tcp-reset")
? "icmpx type " + fw4.default_option("tcp_reject_code")
: "tcp reset"
}} comment "!fw4: Reject TCP traffic"
reject with {{
(fw4.default_option("any_reject_code") != "tcp-reset")
? "icmpx type " + fw4.default_option("any_reject_code")
: "tcp reset"
}} comment "!fw4: Reject any other traffic"
}
{% if (fw4.default_option("synflood_protect") && fw4.default_option("synflood_rate")):
let r = fw4.default_option("synflood_rate");
let b = fw4.default_option("synflood_burst");
%}
chain syn_flood {
limit rate {{ r.rate }}/{{ r.unit }}
{%- if (b): %} burst {{ b }} packets{% endif %} return comment "!fw4: Accept SYN packets below rate-limit"
drop comment "!fw4: Drop excess packets"
}
{% endif %}
{% for (let zone in fw4.zones()): %}
chain input_{{ zone.name }} {
{% for (let rule in fw4.rules("input_"+zone.name)): %}
{%+ include("rule.uc", { fw4, rule }) %}
{% endfor %}
ct status dnat accept comment "!fw4: Accept port redirections"
jump {{ zone.input }}_from_{{ zone.name }}
}
chain output_{{ zone.name }} {
{% for (let rule in fw4.rules("output_"+zone.name)): %}
{%+ include("rule.uc", { fw4, rule }) %}
{% endfor %}
jump {{ zone.output }}_to_{{ zone.name }}
}
chain forward_{{ zone.name }} {
{% for (let rule in fw4.rules("forward_"+zone.name)): %}
{%+ include("rule.uc", { fw4, rule }) %}
{% endfor %}
ct status dnat accept comment "!fw4: Accept port forwards"
jump {{ zone.forward }}_to_{{ zone.name }}
}
{% for (let verdict in ["accept", "reject", "drop"]): %}
{% if (zone.sflags[verdict]): %}
chain {{ verdict }}_from_{{ zone.name }} {
{% for (let rule in zone.match_rules): %}
{%+ include("zone-verdict.uc", { fw4, zone, rule, egress: false, verdict }) %}
{% endfor %}
}
{% endif %}
{% if (zone.dflags[verdict]): %}
chain {{ verdict }}_to_{{ zone.name }} {
{% for (let rule in zone.match_rules): %}
{%+ include("zone-verdict.uc", { fw4, zone, rule, egress: true, verdict }) %}
{% endfor %}
}
{% endif %}
{% endfor %}
{% endfor %}
#
# NAT rules
#
chain dstnat {
type nat hook prerouting priority dstnat; policy accept;
{% for (let zone in fw4.zones()): %}
{% if (zone.dflags.dnat): %}
{% for (let rule in zone.match_rules): %}
{%+ include("zone-jump.uc", { fw4, zone, rule, direction: "dstnat" }) %}
{% endfor %}
{% endif %}
{% endfor %}
}
chain srcnat {
type nat hook postrouting priority srcnat; policy accept;
{% for (let redirect in fw4.redirects("srcnat")): %}
{%+ include("redirect.uc", { fw4, redirect }) %}
{% endfor %}
{% for (let zone in fw4.zones()): %}
{% if (zone.dflags.snat): %}
{% for (let rule in zone.match_rules): %}
{%+ include("zone-jump.uc", { fw4, zone, rule, direction: "srcnat" }) %}
{% endfor %}
{% endif %}
{% endfor %}
}
{% for (let zone in fw4.zones()): %}
{% if (zone.dflags.dnat): %}
chain dstnat_{{ zone.name }} {
{% for (let redirect in fw4.redirects("dstnat_"+zone.name)): %}
{%+ include("redirect.uc", { fw4, redirect }) %}
{% endfor %}
}
{% endif %}
{% if (zone.dflags.snat): %}
chain srcnat_{{ zone.name }} {
{% for (let redirect in fw4.redirects("srcnat_"+zone.name)): %}
{%+ include("redirect.uc", { fw4, redirect }) %}
{% endfor %}
{% if (zone.masq): %}
{% for (let saddrs in zone.masq4_src_subnets): %}
{% for (let daddrs in zone.masq4_dest_subnets): %}
{%+ include("zone-masq.uc", { fw4, zone, family: 4, saddrs, daddrs }) %}
{% endfor %}
{% endfor %}
{% endif %}
{% if (zone.masq6): %}
{% for (let saddrs in zone.masq6_src_subnets): %}
{% for (let daddrs in zone.masq6_dest_subnets): %}
{%+ include("zone-masq.uc", { fw4, zone, family: 6, saddrs, daddrs }) %}
{% endfor %}
{% endfor %}
{% endif %}
}
{% endif %}
{% endfor %}
#
# Raw rules (notrack & helper)
#
chain raw_prerouting {
type filter hook prerouting priority raw; policy accept;
{% for (let target in ["helper", "notrack"]): %}
{% for (let zone in fw4.zones()): %}
{% if (zone.dflags[target]): %}
{% for (let rule in zone.match_rules): %}
{% let devices_pos = fw4.filter_loopback_devs(rule.devices_pos, false); %}
{% let subnets_pos = fw4.filter_loopback_addrs(rule.subnets_pos, false); %}
{% if (rule.devices_neg || rule.subnets_neg || devices_pos || subnets_pos): %}
{%+ if (rule.family): -%}
meta nfproto {{ fw4.nfproto(rule.family) }} {%+ endif -%}
{%+ include("zone-match.uc", { fw4, egress: false, rule: { ...rule, devices_pos, subnets_pos } }) -%}
jump {{ target }}_{{ zone.name }} comment "!fw4: {{ zone.name }} {{ fw4.nfproto(rule.family, true) }} {{
(target == "helper") ? "CT helper assignment" : "CT bypass"
}}"
{% endif %}
{% endfor %}
{% endif %}
{% endfor %}
{% endfor %}
}
chain raw_output {
type filter hook output priority raw; policy accept;
{% for (let target in ["helper", "notrack"]): %}
{% for (let zone in fw4.zones()): %}
{% if (zone.dflags[target]): %}
{% for (let rule in zone.match_rules): %}
{% let devices_pos = fw4.filter_loopback_devs(rule.devices_pos, true); %}
{% let subnets_pos = fw4.filter_loopback_addrs(rule.subnets_pos, true); %}
{% if (devices_pos || subnets_pos): %}
{%+ if (rule.family): -%}
meta nfproto {{ fw4.nfproto(rule.family) }} {%+ endif -%}
{%+ include("zone-match.uc", { fw4, egress: false, rule: { ...rule, devices_pos, subnets_pos } }) -%}
jump {{ target }}_{{ zone.name }} comment "!fw4: {{ zone.name }} {{ fw4.nfproto(rule.family, true) }} {{
(target == "helper") ? "CT helper assignment" : "CT bypass"
}}"
{% endif %}
{% endfor %}
{% endif %}
{% endfor %}
{% endfor %}
}
{% for (let helper in fw4.helpers()): %}
{% if (helper.available): %}
{% for (let proto in helper.proto): %}
ct helper {{ helper.name }} {
type {{ fw4.quote(helper.name, true) }} protocol {{ proto.name }};
}
{% endfor %}
{% endif %}
{% endfor %}
{% for (let target in ["helper", "notrack"]): %}
{% for (let zone in fw4.zones()): %}
{% if (zone.dflags[target]): %}
chain {{ target }}_{{ zone.name }} {
{% for (let rule in fw4.rules(target+"_"+zone.name)): %}
{%+ include("rule.uc", { fw4, rule }) %}
{% endfor %}
}
{% endif %}
{% endfor %}
{% endfor %}
#
# Mangle rules
#
chain mangle_prerouting {
type filter hook prerouting priority mangle; policy accept;
{% for (let rule in fw4.rules("mangle_prerouting")): %}
{%+ include("rule.uc", { fw4, rule }) %}
{% endfor %}
}
chain mangle_postrouting {
type filter hook postrouting priority mangle; policy accept;
{% for (let rule in fw4.rules("mangle_postrouting")): %}
{%+ include("rule.uc", { fw4, rule }) %}
{% endfor %}
}
chain mangle_input {
type filter hook input priority mangle; policy accept;
{% for (let rule in fw4.rules("mangle_input")): %}
{%+ include("rule.uc", { fw4, rule }) %}
{% endfor %}
}
chain mangle_output {
type filter hook output priority mangle; policy accept;
{% for (let rule in fw4.rules("mangle_output")): %}
{%+ include("rule.uc", { fw4, rule }) %}
{% endfor %}
}
chain mangle_forward {
type filter hook forward priority mangle; policy accept;
{% for (let rule in fw4.rules("mangle_forward")): %}
{%+ include("rule.uc", { fw4, rule }) %}
{% endfor %}
{% for (let zone in fw4.zones()): %}
{% if (zone.mtu_fix): %}
{% for (let rule in zone.match_rules): %}
{%+ include("zone-mssfix.uc", { fw4, zone, rule, egress: false }) %}
{%+ include("zone-mssfix.uc", { fw4, zone, rule, egress: true }) %}
{% endfor %}
{% endif %}
{% endfor %}
}
}
then i has add my ipv4 public behind router
with /etc/config/upnpd
you add
option external_ip
![]()
my nat is now open i'm so very happy
Is this necessary if I'm on Release v0.6.2 ?
I thought using the attended sys upgrade is sufficient? Am I still on an older variant unless I re-flash v0.6.4?
I am also on v0.6.2 and I believe that is sufficient, but I am trying to figure out how to use 'auc' to obtain the rc1 with my additional packages for a minimal hassle transition to the new rc1 (and subsequent rc's).
@aparcar has just added the release candidate to the sysupgrade server, so now you can
auc -n -b 22.03 -B 22.03.0-rc1
Sweet - thanks so much @daniel and @aparcar! The whole dynamic sysupgrade/auc process fantastic, and it's terrific to be able to leverage it for these release candidates too.
Just upgraded all my x3 RT3200's connected via WDS (each with their own package mix) and so far so good.
FWIW I have been using this setup for business and personal use based on the master snapshots for months without issue, whilst waiting for (more) stable release(s). I use: a) WireGuard; b) adaptive bandwidth CAKE on LTE connection notwithstanding VPN PBR; c) WDS extended WiFi and separate WDS extended Guest-WiFi, both with fast transition to support roaming. And it all just works beautifully. So a huge thanks to the OpenWrt devs for making experiences like mine possible.
very good news ![]()
thanks for your work
any chance to appair that ? 22.03 rc1
https://asu.aparcar.org/?version=SNAPSHOT&target=mediatek%2Fmt7622&id=linksys_e8450-ubi
I tried your command to use auc to upgrade to rc1. It fails for me.
root@e8450:~# auc -n -b 22.03 -B 22.03.0-rc1
auc (0.2.5-2)
Server: https://sysupgrade.openwrt.org
Running: SNAPSHOT r19519-39799974a3 on mediatek/mt7622 (linksys,e8450-ubi)
Available: 22.03.0-rc1 r19302-df622768da
Requesting package lists...
kmod-usb-storage: 5.10.112-1 -> 5.10.111-1
kmod-crypto-gf128: 5.10.112-1 -> 5.10.111-1
kmod-usb-core: 5.10.112-1 -> 5.10.111-1
kmod-usb-storage-uas: 5.10.112-1 -> 5.10.111-1
kmod-crypto-manager: 5.10.112-1 -> 5.10.111-1
kmod-nft-nat6: 5.10.112-1 -> 5.10.111-1
kmod-crypto-ctr: 5.10.112-1 -> 5.10.111-1
kmod-nft-fib: 5.10.112-1 -> 5.10.111-1
kmod-nfnetlink: 5.10.112-1 -> 5.10.111-1
kmod-crypto-hash: 5.10.112-1 -> 5.10.111-1
kmod-nf-reject6: 5.10.112-1 -> 5.10.111-1
kmod-crypto-aead: 5.10.112-1 -> 5.10.111-1
luci-mod-system: git-22.102.44067-b6fb2b1 -> git-22.102.44406-0c0cf78
openssl-util: 1.1.1n-2 -> 1.1.1n-1
kmod-nf-flow: 5.10.112-1 -> 5.10.111-1
kmod-lib-crc-ccitt: 5.10.112-1 -> 5.10.111-1
getrandom: 2022-01-06-b87a4fdc-2 -> 2021-08-03-205defb5-2
ucode-mod-ubus: 2022-04-13-e14b0993-1 -> 2022-02-11-a29bad94-1
luci-theme-bootstrap: git-22.084.38997-8e09f18 -> git-22.084.39030-f187425
kmod-pppoe: 5.10.112-1 -> 5.10.111-1
kmod-pppox: 5.10.112-1 -> 5.10.111-1
kmod-nf-reject: 5.10.112-1 -> 5.10.111-1
base-files: 1485-r19519-39799974a3 -> 1475-r19302-df622768da
kmod-lib-crc16: 5.10.112-1 -> 5.10.111-1
kmod-nf-nat: 5.10.112-1 -> 5.10.111-1
kmod-crypto-crc32c: 5.10.112-1 -> 5.10.111-1
ucode-mod-uci: 2022-04-13-e14b0993-1 -> 2022-02-11-a29bad94-1
kmod-mt7615e: 5.10.112+2022-04-23-a666d563-4 -> 5.10.111+2022-03-15-053668ac-4
firewall4: 2022-04-21-fc83d462-1 -> 2022-02-12-53caa1a7-1
uboot-envtools: 2022.01-23 -> 2022.01-22
kmod-usb-xhci-hcd: 5.10.112-1 -> 5.10.111-1
kmod-crypto-hmac: 5.10.112-1 -> 5.10.111-1
kmod-crypto-sha256: 5.10.112-1 -> 5.10.111-1
kmod-mt7615-common: 5.10.112+2022-04-23-a666d563-4 -> 5.10.111+2022-03-15-053668ac-4
kmod-nf-nat6: 5.10.112-1 -> 5.10.111-1
kmod-lib-crc32c: 5.10.112-1 -> 5.10.111-1
luci-mod-status: git-22.087.28325-8a46648 -> git-22.089.68955-66d9387
kmod-mt76-connac: 5.10.112+2022-04-23-a666d563-4 -> 5.10.111+2022-03-15-053668ac-4
kmod-crypto-seqiv: 5.10.112-1 -> 5.10.111-1
kmod-fs-vfat: 5.10.112-1 -> 5.10.111-1
kmod-nft-nat: 5.10.112-1 -> 5.10.111-1
kmod-usb3: 5.10.112-1 -> 5.10.111-1
kmod-fs-exfat: 5.10.112-1 -> 5.10.111-1
luci-app-firewall: git-22.089.67453-0eb3aeb -> git-22.089.67563-7e3c1b4
kmod-thermal: 5.10.112-1 -> 5.10.111-1
kmod-crypto-ghash: 5.10.112-1 -> 5.10.111-1
kmod-fs-ext4: 5.10.112-1 -> 5.10.111-1
ucode-mod-fs: 2022-04-13-e14b0993-1 -> 2022-02-11-a29bad94-1
kmod-hwmon-core: 5.10.112-1 -> 5.10.111-1
kmod-nls-utf8: 5.10.112-1 -> 5.10.111-1
kmod-nls-cp437: 5.10.112-1 -> 5.10.111-1
odhcpd-ipv6only: 2022-03-22-860ca900-1 -> 2021-08-11-01b4e604-1
ucode: 2022-04-13-e14b0993-1 -> 2022-02-11-a29bad94-1
kmod-mt7915e: 5.10.112+2022-04-23-a666d563-4 -> 5.10.111+2022-03-15-053668ac-4
kmod-crypto-ccm: 5.10.112-1 -> 5.10.111-1
kmod-nf-log: 5.10.112-1 -> 5.10.111-1
libucode: 2022-04-13-e14b0993-1 -> 2022-02-11-a29bad94-1
luci-base: git-22.089.43958-7110635 -> git-22.083.69105-af8e91c
kmod-leds-gpio: 5.10.112-1 -> 5.10.111-1
kmod-gpio-button-hotplug: 5.10.112-3 -> 5.10.111-3
logd: 2022-01-06-b87a4fdc-2 -> 2021-08-03-205defb5-2
kmod-nf-log6: 5.10.112-1 -> 5.10.111-1
kmod-mac80211: 5.10.112+5.15.33-1-1 -> 5.10.111+5.15.33-1-1
libopenssl: 1.1.1n-2 -> 1.1.1n-1
openwrt-keyring: 2022-03-25-62471e69-2 -> 2022-03-25-62471e69-3
luci-app-attendedsysupgrade: git-22.081.81213-8936e3c -> git-22.068.37885-65266c4
kmod-nft-offload: 5.10.112-1 -> 5.10.111-1
kmod-ppp: 5.10.112-1 -> 5.10.111-1
libopenssl-conf: 1.1.1n-2 -> 1.1.1n-1
kmod-fs-f2fs: 5.10.112-1 -> 5.10.111-1
kmod-crypto-null: 5.10.112-1 -> 5.10.111-1
kmod-mt7615-firmware: 5.10.112+2022-04-23-a666d563-4 -> 5.10.111+2022-03-15-053668ac-4
kmod-nf-conntrack: 5.10.112-1 -> 5.10.111-1
kmod-crypto-gcm: 5.10.112-1 -> 5.10.111-1
kmod-fs-autofs4: 5.10.112-1 -> 5.10.111-1
kmod-nls-iso8859-1: 5.10.112-1 -> 5.10.111-1
kmod-crypto-cmac: 5.10.112-1 -> 5.10.111-1
luci-lib-jsonc: git-22.079.54693-45f411b -> git-22.097.61921-7513345
kmod-crypto-rng: 5.10.112-1 -> 5.10.111-1
kmod-nf-conntrack6: 5.10.112-1 -> 5.10.111-1
kmod-mt76-core: 5.10.112+2022-04-23-a666d563-4 -> 5.10.111+2022-03-15-053668ac-4
ubox: 2022-01-06-b87a4fdc-2 -> 2021-08-03-205defb5-2
kmod-crypto-crc32: 5.10.112-1 -> 5.10.111-1
luci-mod-network: git-22.087.28325-8a46648 -> git-22.089.68955-66d9387
kmod-nft-core: 5.10.112-1 -> 5.10.111-1
kmod-nls-base: 5.10.112-1 -> 5.10.111-1
kmod-scsi-core: 5.10.112-1 -> 5.10.111-1
kmod-slhc: 5.10.112-1 -> 5.10.111-1
kmod-cfg80211: 5.10.112+5.15.33-1-1 -> 5.10.111+5.15.33-1-1
Are you sure you want to continue the upgrade process? [N/y] y
Segmentation fault
Update:
Re-ran the command and it worked fine.
Notably, the first time around where it segfaulted never printed:
Requesting build...
Full successful result:
root@e8450:~# auc -n -b 22.03 -B 22.03.0-rc1
auc (0.2.5-2)
Server: https://sysupgrade.openwrt.org
Running: SNAPSHOT r19519-39799974a3 on mediatek/mt7622 (linksys,e8450-ubi)
Available: 22.03.0-rc1 r19302-df622768da
Requesting package lists...
kmod-usb-storage: 5.10.112-1 -> 5.10.111-1
kmod-crypto-gf128: 5.10.112-1 -> 5.10.111-1
kmod-usb-core: 5.10.112-1 -> 5.10.111-1
kmod-usb-storage-uas: 5.10.112-1 -> 5.10.111-1
kmod-crypto-manager: 5.10.112-1 -> 5.10.111-1
kmod-nft-nat6: 5.10.112-1 -> 5.10.111-1
kmod-crypto-ctr: 5.10.112-1 -> 5.10.111-1
kmod-nft-fib: 5.10.112-1 -> 5.10.111-1
kmod-nfnetlink: 5.10.112-1 -> 5.10.111-1
kmod-crypto-hash: 5.10.112-1 -> 5.10.111-1
kmod-nf-reject6: 5.10.112-1 -> 5.10.111-1
kmod-crypto-aead: 5.10.112-1 -> 5.10.111-1
luci-mod-system: git-22.102.44067-b6fb2b1 -> git-22.102.44406-0c0cf78
openssl-util: 1.1.1n-2 -> 1.1.1n-1
kmod-nf-flow: 5.10.112-1 -> 5.10.111-1
kmod-lib-crc-ccitt: 5.10.112-1 -> 5.10.111-1
getrandom: 2022-01-06-b87a4fdc-2 -> 2021-08-03-205defb5-2
ucode-mod-ubus: 2022-04-13-e14b0993-1 -> 2022-02-11-a29bad94-1
luci-theme-bootstrap: git-22.084.38997-8e09f18 -> git-22.084.39030-f187425
kmod-pppoe: 5.10.112-1 -> 5.10.111-1
kmod-pppox: 5.10.112-1 -> 5.10.111-1
kmod-nf-reject: 5.10.112-1 -> 5.10.111-1
base-files: 1485-r19519-39799974a3 -> 1475-r19302-df622768da
kmod-lib-crc16: 5.10.112-1 -> 5.10.111-1
kmod-nf-nat: 5.10.112-1 -> 5.10.111-1
kmod-crypto-crc32c: 5.10.112-1 -> 5.10.111-1
ucode-mod-uci: 2022-04-13-e14b0993-1 -> 2022-02-11-a29bad94-1
kmod-mt7615e: 5.10.112+2022-04-23-a666d563-4 -> 5.10.111+2022-03-15-053668ac-4
firewall4: 2022-04-21-fc83d462-1 -> 2022-02-12-53caa1a7-1
uboot-envtools: 2022.01-23 -> 2022.01-22
kmod-usb-xhci-hcd: 5.10.112-1 -> 5.10.111-1
kmod-crypto-hmac: 5.10.112-1 -> 5.10.111-1
kmod-crypto-sha256: 5.10.112-1 -> 5.10.111-1
kmod-mt7615-common: 5.10.112+2022-04-23-a666d563-4 -> 5.10.111+2022-03-15-053668ac-4
kmod-nf-nat6: 5.10.112-1 -> 5.10.111-1
kmod-lib-crc32c: 5.10.112-1 -> 5.10.111-1
luci-mod-status: git-22.087.28325-8a46648 -> git-22.089.68955-66d9387
kmod-mt76-connac: 5.10.112+2022-04-23-a666d563-4 -> 5.10.111+2022-03-15-053668ac-4
kmod-crypto-seqiv: 5.10.112-1 -> 5.10.111-1
kmod-fs-vfat: 5.10.112-1 -> 5.10.111-1
kmod-nft-nat: 5.10.112-1 -> 5.10.111-1
kmod-usb3: 5.10.112-1 -> 5.10.111-1
kmod-fs-exfat: 5.10.112-1 -> 5.10.111-1
luci-app-firewall: git-22.089.67453-0eb3aeb -> git-22.089.67563-7e3c1b4
kmod-thermal: 5.10.112-1 -> 5.10.111-1
kmod-crypto-ghash: 5.10.112-1 -> 5.10.111-1
kmod-fs-ext4: 5.10.112-1 -> 5.10.111-1
ucode-mod-fs: 2022-04-13-e14b0993-1 -> 2022-02-11-a29bad94-1
kmod-hwmon-core: 5.10.112-1 -> 5.10.111-1
kmod-nls-utf8: 5.10.112-1 -> 5.10.111-1
kmod-nls-cp437: 5.10.112-1 -> 5.10.111-1
odhcpd-ipv6only: 2022-03-22-860ca900-1 -> 2021-08-11-01b4e604-1
ucode: 2022-04-13-e14b0993-1 -> 2022-02-11-a29bad94-1
kmod-mt7915e: 5.10.112+2022-04-23-a666d563-4 -> 5.10.111+2022-03-15-053668ac-4
kmod-crypto-ccm: 5.10.112-1 -> 5.10.111-1
kmod-nf-log: 5.10.112-1 -> 5.10.111-1
libucode: 2022-04-13-e14b0993-1 -> 2022-02-11-a29bad94-1
luci-base: git-22.089.43958-7110635 -> git-22.083.69105-af8e91c
kmod-leds-gpio: 5.10.112-1 -> 5.10.111-1
kmod-gpio-button-hotplug: 5.10.112-3 -> 5.10.111-3
logd: 2022-01-06-b87a4fdc-2 -> 2021-08-03-205defb5-2
kmod-nf-log6: 5.10.112-1 -> 5.10.111-1
kmod-mac80211: 5.10.112+5.15.33-1-1 -> 5.10.111+5.15.33-1-1
libopenssl: 1.1.1n-2 -> 1.1.1n-1
openwrt-keyring: 2022-03-25-62471e69-2 -> 2022-03-25-62471e69-3
luci-app-attendedsysupgrade: git-22.081.81213-8936e3c -> git-22.068.37885-65266c4
kmod-nft-offload: 5.10.112-1 -> 5.10.111-1
kmod-ppp: 5.10.112-1 -> 5.10.111-1
libopenssl-conf: 1.1.1n-2 -> 1.1.1n-1
kmod-fs-f2fs: 5.10.112-1 -> 5.10.111-1
kmod-crypto-null: 5.10.112-1 -> 5.10.111-1
kmod-mt7615-firmware: 5.10.112+2022-04-23-a666d563-4 -> 5.10.111+2022-03-15-053668ac-4
kmod-nf-conntrack: 5.10.112-1 -> 5.10.111-1
kmod-crypto-gcm: 5.10.112-1 -> 5.10.111-1
kmod-fs-autofs4: 5.10.112-1 -> 5.10.111-1
kmod-nls-iso8859-1: 5.10.112-1 -> 5.10.111-1
kmod-crypto-cmac: 5.10.112-1 -> 5.10.111-1
luci-lib-jsonc: git-22.079.54693-45f411b -> git-22.097.61921-7513345
kmod-crypto-rng: 5.10.112-1 -> 5.10.111-1
kmod-nf-conntrack6: 5.10.112-1 -> 5.10.111-1
kmod-mt76-core: 5.10.112+2022-04-23-a666d563-4 -> 5.10.111+2022-03-15-053668ac-4
ubox: 2022-01-06-b87a4fdc-2 -> 2021-08-03-205defb5-2
kmod-crypto-crc32: 5.10.112-1 -> 5.10.111-1
luci-mod-network: git-22.087.28325-8a46648 -> git-22.089.68955-66d9387
kmod-nft-core: 5.10.112-1 -> 5.10.111-1
kmod-nls-base: 5.10.112-1 -> 5.10.111-1
kmod-scsi-core: 5.10.112-1 -> 5.10.111-1
kmod-slhc: 5.10.112-1 -> 5.10.111-1
kmod-cfg80211: 5.10.112+5.15.33-1-1 -> 5.10.111+5.15.33-1-1
Are you sure you want to continue the upgrade process? [N/y] y
Requesting build................
Image available at https://sysupgrade.openwrt.org/store/ae043418cf8e656082bb91a6737087ff/openwrt-22.03.0-rc1-bd1840e6cc53-mediatek-mt7622-linksys_e8450-ubi-squashfs-sysupgrade.itb
done
To actually do the upgrade you need to remove the -n switch.
root@OpenWrt:~# auc --help
auc (0.2.5-2)
auc: Attended sysUpgrade CLI client
Usage: auc [-b <branch>] [-B <ver>] [-c] [-f] [-h] [-r] [-y]
-b <branch> use specific release branch
-B <ver> use specific release version
-c only check if system is up-to-date
-f use force
-h output help
-n dry-run (don't download or upgrade)
-r check only for release upgrades
-F <fstype> override filesystem type
-y don't wait for user confirmation
Please report issues to improve the server:
https://github.com/aparcar/asu/issues
Hi @Dopam-IT_1987 thanks for the update!
Do you apply the patch in /usr/share/firewall4/templates/ruleset.uc ? I just upgraded to the RC1 and I went there and I checked the code using a website to scan differences and it is completely the same in the RC1 build I think.
Also, do you apply the option external_ip in /etc/config/upnpd and then in the first part config upnpd 'config' portion? Do you specify the IP or leave it blank? I tried both, but so far, my switch still gets NAT Type B ![]()
Thanks!!!
