Sweet, thanks very much. This looks amazing btw, can't wait to explore all its features.
Will this work (without configuration) in an environment where openssh listens on port 22 and dropbear on port 2222? If not, would it be possible to configure it to monitor both?
The logfile parser records all dropbear related events, regardless of the used port ... it should work with 22 and 2222 as well.
Sweet, any chance of adding OpenSSH support in too?
Yes, no problem with that. Could you provide me logread excerpts with openssh and failed login attemps via PM? Thanks!
Please note: banIP update 0.2.0 is broken in master (released yesterday), please wait for 0.2.1 - thanks & sorry for the mess.
Hi there,
Tested the 0.2.1 version. works perfect.
I have a feature request for you to consider:
- to log the ips that have been banned and be able to view that list on luci.
not really.
The idea came to me as I wanted to know who the attackers are.
I mean, I have banip installed and running, but I have no idea of how helpful banip is or has been, because I have no visibility about it's work.
So I would like to have a stats page, where it shows how many threats it has banned, when and why they were banned, and who were they ( ip address with reverse dns query if any and country of origin ).
does this make any sense to you?
That's partly already implemented as all ipsets are initialized with counters, e.g. here is my current "country" ipset with counters > 0:
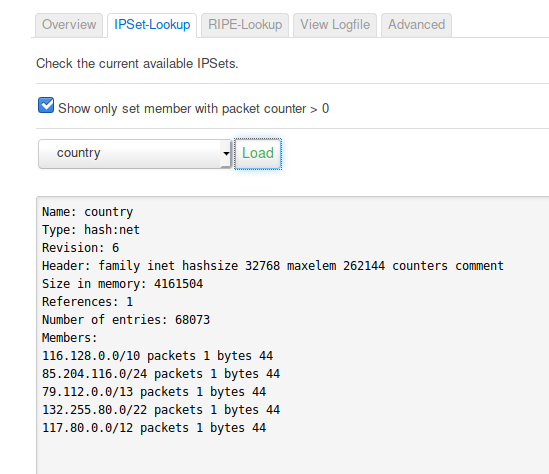
That means the listed ips of this ipset has been blocked. Of course these counters will be reset with the next update of the ipset ... therefore there are currently no longterm statistics.
maybe I am not understanding correctly what banIP does.
As I understand it, banIP:
- bans incoming connections from IP addresses contained in the selected blacklists, irrespective of the destination port. Besides this, it also:
- logs and auto-bans unsuccessful connection attempts to the port where sshd is running.
is this correct?
Would we see an updated (0.2.1) package for 18.06.4?
wow, I haven't realized this!
So, just to make it easier then I would suggest adding reverse dns check and country of origin.
No, banIP will be available in 19.07.
yes, I noticed it, but when you have a list of hundred of IP addresses it's not that useful to check one by one.
The list is great, and knowing from where the threat is coming just makes it quite more useful.
For instance, if I see that most of the IP's are chinese I can simply choose to ban cn issued PI addresses.
**Thu Sep 12 17:11:06 2019 daemon.err banip.sh[18017]: /sbin/uci: Parse error (too many arguments) at line 11, byte 47**
**Thu Sep 12 17:11:06 2019 daemon.err banip.sh[18017]: /sbin/uci: Parse error (too many arguments) at line 11, byte 47**
Thu Sep 12 17:11:06 2019 user.info banIP-[0.2.1]: start banIP processing (reload)
Thu Sep 12 17:11:34 2019 user.info banIP-[0.2.1]: 4 IPSets with overall 52036 IPs/Prefixes loaded successfully
(TP-Link Archer C7 v2, OpenWrt SNAPSHOT r10969-869a0183b9)
your uci config file seems to be corrupt, re-install banIP with the "--force-maintainer" opkg option to start with a fresh config.
My config file was wrong 
Btw, thank you for your great work!!