nft requires a lot of main memory for certain actions ... to limit the search requirements you should limit the used cores by banIP/nft, e.g. set the ban_cores to '2' and try again ...
hello, I just switched from release 21 to 22 and installed banip new. I tried to set it up, but it doesn't block any incoming lists, what am I doing wrong?
also when I try to use
root@OpenWrt:/etc/init.d# banip search xxx.xxx.xxx.xxx
it just says: -ash: banip: not found
thx in advance!
so long
edit: config file:
root@OpenWrt:/etc/config# cat banip
config banip 'global'
option ban_debug '0'
option ban_autodetect '1'
list ban_logterm 'Exit before auth from'
list ban_logterm 'luci: failed login'
list ban_logterm 'error: maximum authentication attempts exceeded'
list ban_logterm 'sshd.*Connection closed by.*\[preauth\]'
list ban_logterm 'SecurityEvent=\"InvalidAccountID\".*RemoteAddress='
option ban_enabled '1'
option ban_deduplicate '1'
option ban_loginput '1'
option ban_logforwardwan '1'
option ban_logforwardlan '0'
list ban_country 'af'
list ban_country 'ax'
list ban_country 'al'
list ban_country 'dz'
list ban_country 'as'
list ban_country 'ad'
list ban_country 'ao'
list ban_country 'ai'
list ban_country 'aq'
list ban_country 'ag'
list ban_country 'ar'
list ban_country 'am'
list ban_country 'aw'
list ban_country 'au'
list ban_country 'az'
list ban_country 'bs'
list ban_country 'bh'
list ban_country 'bd'
list ban_country 'bb'
list ban_country 'by'
list ban_country 'be'
list ban_country 'bz'
list ban_country 'bj'
list ban_country 'bm'
list ban_country 'bt'
list ban_country 'bo'
list ban_country 'ba'
list ban_country 'bw'
list ban_country 'bv'
list ban_country 'br'
list ban_country 'io'
list ban_country 'vg'
list ban_country 'bn'
*just shortened here*
option ban_autoblocklist '1'
option ban_allowlistonly '0'
option ban_fetchcmd 'wget'
option ban_protov4 '1'
list ban_ifv4 'wan_indoor'
list ban_ifv4 'wan_outdoor'
list ban_dev 'br-lan.xx'
list ban_trigger 'wan_indoor'
list ban_trigger 'wan_outdoor'
list ban_feed 'backscatterer'
list ban_feed 'bogon'
list ban_feed 'cinsscore'
list ban_feed 'country'
list ban_feed 'darklist'
list ban_feed 'debl'
list ban_feed 'doh'
list ban_feed 'drop'
list ban_feed 'dshield'
list ban_feed 'edrop'
list ban_feed 'feodo'
list ban_feed 'firehol1'
list ban_feed 'firehol2'
list ban_feed 'firehol3'
list ban_feed 'firehol4'
list ban_feed 'greensnow'
list ban_feed 'iblockads'
list ban_feed 'iblockspy'
list ban_feed 'myip'
list ban_feed 'nixspam'
list ban_feed 'proxy'
list ban_feed 'sslbl'
list ban_feed 'stevenblack'
list ban_feed 'talos'
list ban_feed 'threat'
list ban_feed 'threatview'
list ban_feed 'tor'
list ban_feed 'urlhaus'
list ban_feed 'urlvir'
list ban_blockinput 'allowlist'
list ban_blockinput 'blocklist'
list ban_blockinput 'backscatterer'
list ban_blockinput 'bogon'
list ban_blockinput 'cinsscore'
list ban_blockinput 'country'
list ban_blockinput 'darklist'
list ban_blockinput 'debl'
list ban_blockinput 'drop'
list ban_blockinput 'dshield'
list ban_blockinput 'edrop'
list ban_blockinput 'feodo'
list ban_blockinput 'firehol1'
list ban_blockinput 'firehol2'
list ban_blockinput 'firehol3'
list ban_blockinput 'firehol4'
list ban_blockinput 'myip'
list ban_blockinput 'nixspam'
list ban_blockinput 'proxy'
list ban_blockinput 'sslbl'
list ban_blockinput 'talos'
list ban_blockinput 'threat'
list ban_blockinput 'threatview'
list ban_blockinput 'tor'
list ban_blockinput 'urlhaus'
list ban_blockinput 'urlvir'
list ban_blockforwardwan 'allowlist'
list ban_blockforwardwan 'blocklist'
list ban_blockforwardwan 'backscatterer'
list ban_blockforwardwan 'bogon'
list ban_blockforwardwan 'cinsscore'
list ban_blockforwardwan 'drop'
list ban_blockforwardwan 'dshield'
list ban_blockforwardwan 'greensnow'
list ban_blockforwardwan 'iblockspy'
list ban_blockforwardwan 'sslbl'
list ban_blockforwardwan 'urlvir'
option ban_autoallowlist '0'
edit2: active (nft: ✘, monitor: ![]() ) is that normal?
) is that normal?
I don't know what router is in place, but it makes no sense to simply activate all sources and start from there ... most probably you run in an OOM condition. Start with a few sources, enable debug logging, consult the readme and check the local logs.
ok thx, I already try to.
its a virtual openwrt installation done with qemu. running on a raspberry pi 4.
oom is not possible ![]()
update: installed banip again, and status is: active (nft: ![]() , monitor:
, monitor: ![]() )
)
but still the website is reachable from blocked countries... any ideas?
thx!
edit: in the logs I can see like:
banIP/inp-wan/drp/countryv4:
reject wan in:
with the blocked source ip address, but the website is still shown.
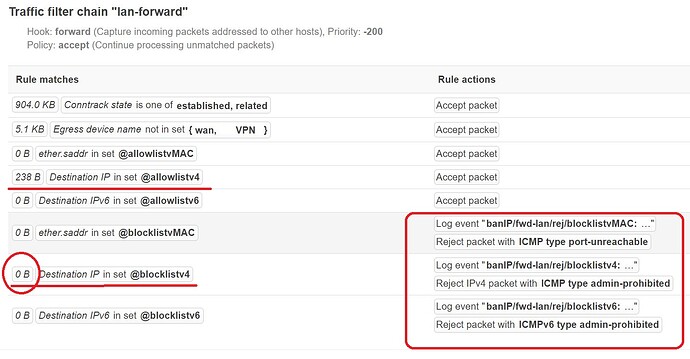
edit: seems to be solved, must be a misunderstanding, wan-forward chain has to be set, not input.
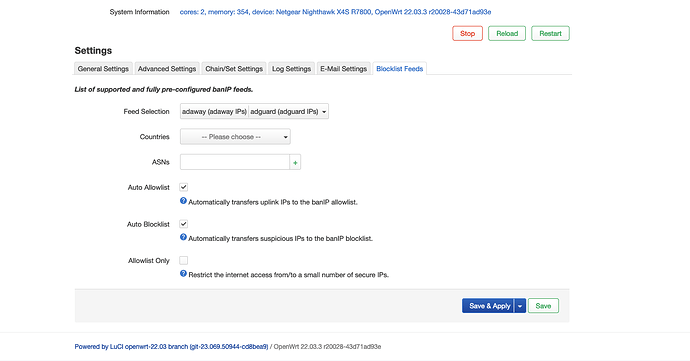
I setup option ban_cores '2' in luci, rebooted and waited for the system to be idle.
Then when searching for IP 1.1.1.1, I still have the same OOM issue.
Looking at htop we see 4 processes related to 1.1.1.1 search using 100% of all 4 cores:
banip config
`root@D1:/etc/config# cat banip
config banip 'global'
option ban_enabled '1'
option ban_debug '1'
option ban_autodetect '0'
list ban_logterm 'Exit before auth from'
list ban_logterm 'luci: failed login'
list ban_logterm 'error: maximum authentication attempts exceeded'
list ban_logterm 'sshd.Connection closed by.[preauth]'
list ban_logterm 'SecurityEvent="InvalidAccountID".*RemoteAddress='
option ban_deduplicate '1'
option ban_loginput '1'
option ban_logforwardwan '1'
option ban_logforwardlan '1'
option ban_autoallowlist '1'
option ban_autoblocklist '1'
option ban_allowlistonly '0'
option ban_fetchcmd 'uclient-fetch'
option ban_protov4 '1'
list ban_ifv4 'wan'
list ban_dev 'wan'
option ban_logcount '10'
option ban_nftpolicy 'memory'
option ban_filelimit '1024'
list ban_feed 'adaway'
list ban_feed 'adguard'
list ban_feed 'adguardtrackers'
list ban_feed 'antipopads'
list ban_feed 'backscatterer'
list ban_feed 'bogon'
list ban_feed 'cinsscore'
list ban_feed 'darklist'
list ban_feed 'debl'
list ban_feed 'doh'
list ban_feed 'drop'
list ban_feed 'dshield'
list ban_feed 'edrop'
list ban_feed 'feodo'
list ban_feed 'firehol1'
list ban_feed 'greensnow'
list ban_feed 'iblockads'
list ban_feed 'iblockspy'
list ban_feed 'myip'
list ban_feed 'nixspam'
list ban_feed 'proxy'
list ban_feed 'sslbl'
list ban_feed 'talos'
list ban_feed 'threat'
list ban_feed 'threatview'
list ban_feed 'tor'
list ban_feed 'uceprotect1'
list ban_feed 'urlhaus'
list ban_feed 'urlvir'
list ban_feed 'voip'
list ban_feed 'webclient'
list ban_feed 'yoyo'
option ban_cores '2'
`
Note:
1.1.1.1 is not in my allow list and is not my DNS server, but is in the doh list I'm using.
Than it might be a bug, I'll take a look and come back to you.
edit: confirmed: it's a search bug to not respect the ban_cores setting. Will be fixed in the next update.
@itsphilos I've got a follow-up question regarding your issue. Did you switch from IPTABLES to NFT setup?
I've encountered same issue on my main router but more testing lead something weird happening in the NFT firewall as nothing is being blocked even adding a manual firewall rule just to test (with banip disabled), and it didn't work.
I might do more testing once I switch my main and test router as my test router has a working setup of firewall and banip. I might do this in the coming Holy Week holiday.
Installed banIP and it was blocking homebrew.
Error: Failed to download https://formulae.brew.sh/api/formula.jws.json!
Failed to download https://formulae.brew.sh/api/cask.jws.json!
after stopping banIP homebrew works again
cat config/banip
config banip 'global'
option ban_debug '0'
option ban_autodetect '1'
list ban_logterm 'Exit before auth from'
list ban_logterm 'luci: failed login'
list ban_logterm 'error: maximum authentication attempts exceeded'
list ban_logterm 'sshd.*Connection closed by.*\[preauth\]'
list ban_logterm 'SecurityEvent=\"InvalidAccountID\".*RemoteAddress='
option ban_enabled '1'
option ban_deduplicate '1'
option ban_loginput '1'
option ban_logforwardwan '1'
option ban_logforwardlan '0'
option ban_autoallowlist '1'
option ban_autoblocklist '1'
option ban_allowlistonly '0'
list ban_feed 'adaway'
list ban_feed 'adguard'
option ban_fetchcmd 'curl'
option ban_protov4 '1'
list ban_ifv4 'ff'
list ban_dev 'ff'
what error I did?
That's an interesting point! To be totally honest, I thought this conversion would happen automatically after upgrading to 22.03 with a sysupgrade. I didn't do anything in specific after that, but I do see that all the relevant packages seem to be installed (such as firewall4 and kmod-nft-core).
What else is necessary to switch from iptables to nft?
It's probably because an IP used by brew.sh is in one of the those ad block list. In my opinion, it's better to use Domain blocking for Ads related rather than IP blocking as some of the IP's used by Ads Servers are common CDNs used also by a lot of non-ad systems.
It's better to use adblock for that purpose. Adblock was also developed by dibdot, the same person who developed banIP.
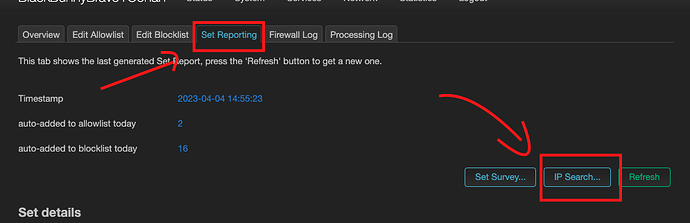
You can check by doing a nslookup formulae.brew.sh to get the IP, and in the Set Report click the IP Search and check which of the two ad blocking list has them included.
My main router uses the snapshot builds (own image builds) but the only exception is its still using the old iptables since I was still using the older banIP (pre nft version) and all FW4 related was removed from that build.
Then I tried updating to my new test build for the main router which uses NFT (a couple of hours ago) as based on my test router and a test network (VM based) everything is working fine. I was supposed to do everything from scratch but since re-doing everything will take me at least 1-2hours (and being lazy), I just did a sysupgrade with settings intact. And I think this was the root cause of the problem. So I switched back to my original image with no NFT and older banip for the time being.
By the way, my main router and test router are totally different brand/models but the issue I think is really a conflict from the IPTABLES based config to the NFT set. And I think doing a fresh install and setup (everything from scratch) will fix the issue.
I can´t make banip nftables block IPs as the iptables version did.
What can I be doing wrong?
config banip 'global'
option ban_enabled '1'
option ban_debug '0'
option ban_autodetect '1'
list ban_logterm 'Exit before auth from'
list ban_logterm 'luci: failed login'
list ban_logterm 'error: maximum authentication attempts exceeded'
list ban_logterm 'sshd.*Connection closed by.*\[preauth\]'
list ban_logterm 'SecurityEvent=\"ChallengeResponseFailed\".*RemoteAddress='
option ban_fetchcmd 'uclient-fetch'
option ban_protov4 '1'
option ban_deduplicate '1'
option ban_loginput '1'
option ban_logforwardwan '1'
option ban_logforwardlan '1'
option ban_autoallowlist '1'
option ban_autoblocklist '1'
option ban_allowlistonly '0'
option ban_triggeraction 'start'
list ban_trigger 'wan'
list ban_trigger 'VPN'
list ban_ifv4 'wan'
list ban_ifv4 'VPN'
list ban_dev 'wan'
list ban_dev 'VPN'
Thanks ![]()
And what's the problem? What's in your blocklist? What's your testcase? ![]()
Hello. The problem is that nothing of what I put in blocklist it´s been blocked.
I tryed with :
3.229.136.98 # 'peru.travel' added on 2023-04-04 22:43:22
81.92.228.153 # 'euronews.com' added on 2023-04-05 08:10:57
but I still can access to that pages ok.
Thanks ![]()
Please provide the output of /etc/init.d/banip search 3.229.136.98
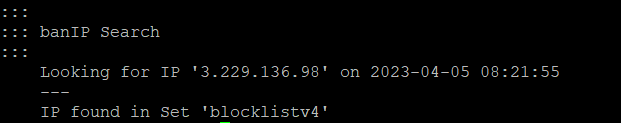
OK, thanks and a ping to this address is still working?
no, it doesn´t. but web page still working
Than the web page communicate with other addresses ... ![]()
ohh, I undertand.
Thanks for answering ![]()