I am ready to give up wi-fi, since it works badly on Asus RT-N66U.
I'm trying to create a stable connection via VPN.
all traffic must pass through vpn, without exceptions and leaks.
All I could achieve is NOT a stable connection.
after connecting vpn, the connection is constantly disappearing. (every 6-10 minutes)
triggered daemon.err openvpn [1071]: Connection reset, restarting [0]
connection is restored, then disappears again
triggered daemon.err openvpn [1071]: Connection reset, restarting [0]
connection is restored, then disappears again
triggered daemon.err openvpn [1071]: Connection reset, restarting [0]
connection is restored, then disappears again
.....
I do not know what the reason is!?
I have system and kernel logs, I can upload them.
I can lay out the settings in the UCI format from the configuration files:
/etc/config/firewall
/etc/config/network
/etc/config/...
/etc/config/.
I use config in /etc/config/openvpn
config openvpn "custom_config"
option enabled "1"
option config "./etc/openvpn/my-vpn.conf"
in kernel log, the following is entering me into a stupor:
[ 78.484948] random: crng init done
[ 78.488484] random: 3 urandom warning(s) missed due to ratelimiting
similar lines are present in the system log:
06:16:52 kern.notice kernel: [ 78.484948] random: crng init done
06:16:52 kern.notice kernel: [ 78.488484] random: 3 urandom warning(s) missed due to ratelimiting
I tried different configurations of the client .conf files of openvpn
configurations work fully and stably with the existing lte modem
stability disappears only when moving .conf + usb modem to the router
I am using the openWRT build 18.06.2
I also tried 17.01.6 and 15.05.1
I tried DD-WRT, Tomato, Asuswrt-Merlin. they do not suit me. and do not satisfy
I do not know whether this configuration of the firewall can affect the stability of the VPN connection
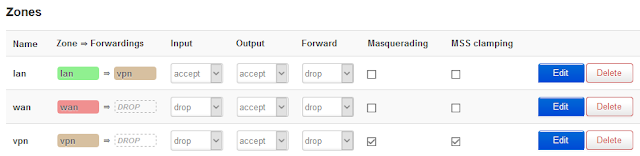
I am interested in all possible and most universal ways of the so-called Kill-Switch
if the above firewall configuration adversely affects performance
I would be grateful for giving various examples that implement guaranteed blocking of traffic past vpn
in other words, my problem can be described as:
I get the following logs from daemon.notice openvpn:
Initialization Sequence Completed
5-10 minute good connect
Connection reset, restarting
...
..
.
Initialization Sequence Completed
6-12 minute good connect
Connection reset, restarting
...
..
.
Initialization Sequence Completed
5-10 minute good connect
Connection reset, restarting
...
..
.
Initialization Sequence Completed
7-9 minute good connect
Connection reset, restarting
...
..
.
Initialization Sequence Completed
