I'm trying to do just that and facing 2 problems.
I have a lan interface made of wired connections bridged with 2 wireless networks, a wan for direct internet access over ISP and a PIA_VPN tunnel interface:
/etc/config/network without routes'n'rules
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd45:96a1:e4d6::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth1.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'eth0.2'
option proto 'pppoe'
option password '***'
option ipv6 '0'
option username '***'
option service 'SoftBank'
list dns '1.1.1.1'
list dns '1.0.0.1'
option peerdns '0'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '5 0t'
config interface 'PIA_VPN'
option proto 'none'
option ifname 'tun0'
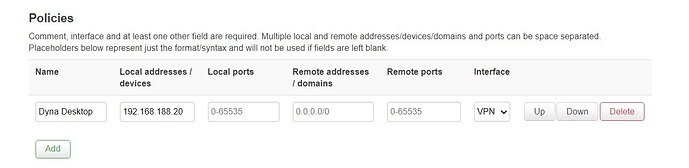
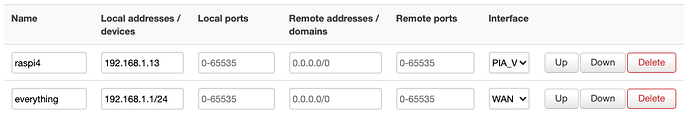
I would like to only route traffic from 192.168.1.13 through VPN.
So, along the lines of the advice linked above, I've added the following to /etc/config/network:
- a separate route to rule all traffic over to the
PIA_VPN interface into a separate table
# in /etc/config/network
config route
option interface 'PIA_VPN'
option target '0.0.0.0'
option netmask '0.0.0.0'
option table '2'
- and a rule to use this table for all traffic originating from
192.168.1.13
config rule
option src '192.168.1.13/32'
option dest '0.0.0.0/0'
option priority '1'
option lookup '2'
The result though is that in the default state of the system (one of the OpenVPN instances is started) any attempt to connect to the outside world from 192.168.1.13 fails on the first hop (the router):
pi@192.168.1.13:~ $ traceroute google.com
traceroute to google.com (172.217.175.78), 30 hops max, 60 byte packets
1 192.168.1.1 (192.168.1.1) 0.748 ms 0.632 ms 0.647 ms
2 * * *
3 * * *
. . .
While from everywhere else on the lan, including the router itself, everything goes, as expected, over through the ISP.
So this is the first problem I'd like to resolve: get that traffic from that one device to propagate over to the VPN tunnel when it's active. Have I messed something up or do I need anything special in the Firewall? Currently there is nothing much:
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'PIA_VPN wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
(/etc/firewall.user is empty)
When I stop the active OpenVPN instance, traffic from 192.168.1.13 successfully flows over where needed through wan.
When I then manually start the OpenVPN instance from LuCI, all traffic from all devices in lan, including the router and 192.168.1.13, starts going to the VPN.
And it is the second problem: if I need to bounce just the OpenVPN connection (it seems to resolve the main issue of the first problem  ), how do I make the router keep respecting the rule and route only traffic from one device into that VPN?
), how do I make the router keep respecting the rule and route only traffic from one device into that VPN?
Any assistance would be much appreciated.
 I only use the gui.
I only use the gui.