Hey Guys,
Please help me how to configuration firewall on GL.inet Mt300N-v2,OpenWrt 18.06.1 r7258-5eb055306f
trendy
April 26, 2019, 10:23am
4
Is the cacti server located in LAN or WAN?
thanx for reply,
heres ss for interfaces
Please post here the output of the following command, all in one linecat /etc/config/network; cat /etc/config/firewall; ip -4 addr ; ip -4 ro ; ip -4 ru
cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd34:7161:a76c::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option hostname 'GL-MT300N-V2-b67'
option ipaddr '172.16.32.1'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
option hostname 'GL-MT300N-V2-b67'
option metric '10'
config device 'wan_dev'
option name 'eth0.2'
option macaddr 'e4:95:6e:46:6b:67'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0 6t'
config interface 'tap0'
option proto 'none'
option ifname 'tap0'
option auto '1'
config interface 'tap1'
option ifname 'tap1'
option proto 'none'
option auto '1'
My ip route is
172.16.0.0/20 via 172.16.254.1 dev tap0 proto zebra metric 20
172.16.16.0/20 via 172.16.254.4 dev tap0 proto zebra metric 20
172.16.32.0/24 dev br-lan proto kernel scope link src 172.16.32.1
172.16.48.0/24 via 172.16.254.7 dev tap0 proto zebra metric 20
172.16.60.0/24 via 172.16.254.2 dev tap0 proto zebra metric 20
172.16.64.0/24 via 172.16.254.5 dev tap0 proto zebra metric 20
172.16.72.0/24 via 172.16.254.6 dev tap0 proto zebra metric 20
172.16.252.0/25 dev tap1 proto kernel scope link src 172.16.252.7
172.16.252.128/25 via 172.16.252.1 dev tap1
172.16.253.0/24 via 172.16.252.1 dev tap1
172.16.254.0/25 dev tap0 proto kernel scope link src 172.16.254.3
192.168.32.0/24 dev eth0.2 proto static scope link metric 10
192.168.87.0/24 via 172.16.254.1 dev tap0 proto zebra metric 20
The cacti server is 172.16.0.2 and can communicate both of them.
You forgot to post the rest of the configurations I asked you.
2 Likes
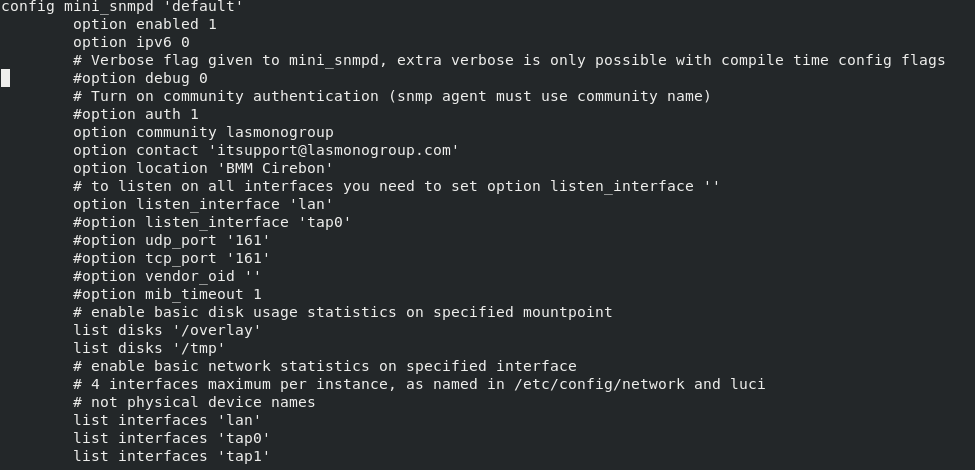
Tryfebri:
mini_snmp
This package is actually larger now; and doesn't do 64-bit counters.
root@GL-MT300N-V2:~# cat /etc/config/network; cat /etc/config/firewall; ip -4 addr ; ip -4 ro ; ip -4 ru
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd34:7161:a76c::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option hostname 'GL-MT300N-V2-b67'
option ipaddr '172.16.32.1'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
option hostname 'GL-MT300N-V2-b67'
option metric '10'
config device 'wan_dev'
option name 'eth0.2'
option macaddr 'e4:95:6e:46:6b:67'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0 6t'
config interface 'tap0'
option proto 'none'
option ifname 'tap0'
option auto '1'
config interface 'tap1'
option ifname 'tap1'
option proto 'none'
option auto '1'
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
option reload '1'
config include 'glfw'
option type 'script'
option path '/usr/bin/glfw.sh'
option reload '1'
config include 'glqos'
option type 'script'
option path '/usr/sbin/glqos.sh'
option reload '1'
config include 'mwan3'
option type 'script'
option path '/var/etc/mwan3.include'
option reload '1'
config rule 'glservice_rule'
option name 'glservice'
option dest_port '83'
option proto 'tcp udp'
option src 'wan'
option target 'ACCEPT'
option enabled '0'
config zone
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
option name 'VPN'
option network 'tap0 tap1'
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
5: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 172.16.32.1/24 brd 172.16.32.255 scope global br-lan
valid_lft forever preferred_lft forever
7: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.32.196/24 brd 192.168.32.255 scope global eth0.2
valid_lft forever preferred_lft forever
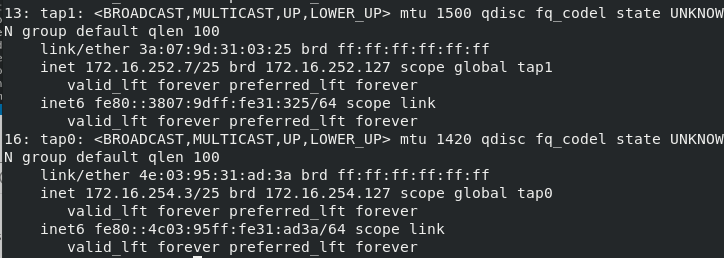
13: tap1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 100
inet 172.16.252.7/25 brd 172.16.252.127 scope global tap1
valid_lft forever preferred_lft forever
14: tap0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1420 qdisc fq_codel state UNKNOWN group default qlen 100
inet 172.16.254.3/25 brd 172.16.254.127 scope global tap0
valid_lft forever preferred_lft forever
default via 192.168.32.1 dev eth0.2 proto static src 192.168.32.196 metric 10
172.16.0.0/20 via 172.16.254.1 dev tap0 proto zebra metric 20
172.16.16.0/20 via 172.16.254.4 dev tap0 proto zebra metric 20
172.16.32.0/24 dev br-lan proto kernel scope link src 172.16.32.1
172.16.48.0/24 via 172.16.254.7 dev tap0 proto zebra metric 20
172.16.60.0/24 via 172.16.254.2 dev tap0 proto zebra metric 20
172.16.64.0/24 via 172.16.254.5 dev tap0 proto zebra metric 20
172.16.72.0/24 via 172.16.254.6 dev tap0 proto zebra metric 20
172.16.252.0/25 dev tap1 proto kernel scope link src 172.16.252.7
172.16.252.128/25 via 172.16.252.1 dev tap1
172.16.253.0/24 via 172.16.252.1 dev tap1
172.16.254.0/25 dev tap0 proto kernel scope link src 172.16.254.3
192.168.32.0/24 dev eth0.2 proto static scope link metric 10
192.168.87.0/24 via 172.16.254.1 dev tap0 proto zebra metric 20
0: from all lookup local
1001: from all iif eth0.2 lookup main
2001: from all fwmark 0x100/0x3f00 lookup 1
2061: from all fwmark 0x3d00/0x3f00 blackhole
2062: from all fwmark 0x3e00/0x3f00 unreachable
32766: from all lookup main
32767: from all lookup default
trendy
May 8, 2019, 10:38am
11
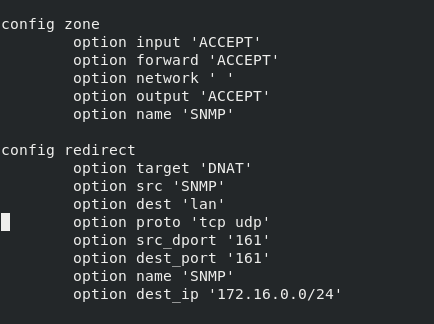
According to your configuration snmpd listens to lan interface.
In firewall there is no rule to allow the snmp from VPN zone (better use small letters) to LAN IP of the router.
1 Like