There are enough insecure wireless devices in my network to be concerned about. I have limited opportunity to secure those devices. I am looking forward to know if there are extra measures that can be taken to further protect the rest of the network (the router and wired LAN clients) from the Wireless devices.
What I have already done:
- Wired LAN has its own interface, firewall zone, dhcp server and subnet
- Wireless LAN has its own interface, firewall zone, dhcp server and subnet
- In firewall settings, "Forward" is set to reject for all interfaces
- In firewall settings, "Input" is set to reject for WLAN interface (with DHCP and DNS exceptions)
Is there anything I'm missing?
(WLAN clients are already isolated between themselves but this post focuses upon protecting the rest of the network)
You have 2 diferent VLANs and subnets. That is OK for me.
But with firewall rules I think you need to do:
In INPUT chain: do not accept input connection from wlan vlan
In FORWARD chain: do not allow WLAN hosts to reach the wired LAN hosts
For example, in IP tables:
iptables -I INPUT -s 192.168.1.0/255.255.255.0 -j DROP
iptables -I FORWARD -s 192.168.1.0/255.255.255.0 -d 192.168.0.0/255.255.255.0 -j DROP
With the first rule you do not accept input from that network, with the second rule the network 192.168.1.0/24 (wireless) can not reach 192.168.0.0/24 (wired). Maybe I made a little mistake as I am not a really an expert with iptables but with that concepts can be implemented for sure.
With the forward rule you protect the Wired LAN, and with INPUT chain you protect the access to the router.
Hey there.
Depending on what to expect from your wireless devices, you could split them even further.
There might be a group of devices which should respond to requests from LAN but not actively connect to LAN devices.
Think e.g. a printer.
There's a chance those device don't even require internet access.
There might be a group of devices which has no business in communicating with any other local network device, but must be able to access the internet in order to do something useful.
Think e.g. a FireTV.
You could at first classify your network devices:
- Needs internet access?
- Needs to respond to LAN requests?
- Needs to initialize traffic to LAN?
When you're looking at the LuCI UI, that's basically not only the "forward" checkbox for a firewall zone but the right hand side of the arrow.
If you know what those device should do, you can always disable outgoing traffic in general and only allow specific traffic. You could e.g. only allow HTTPS routing for most of those devices and prevent them from e.g. participate in NTP, DNS, FTP or whatever communication.
Basically disable everything by default and maintain a curated allow list. Be as specific with those allow rules as possible.
Regards,
Stephan.
1 Like
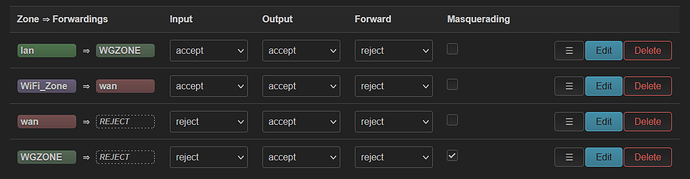
Do I really need to run these commands when I set my firewall like this?
As you can see, the "Forward" column is all REJECT and I have also changed "Input" from WiFi to REJECT after I took this screenshot.
I think that you do not have enough flexibility there to do the configurations I proposed.
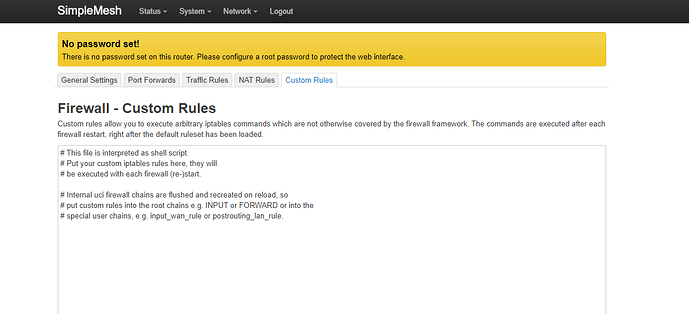
You can go to LUCI, firewall tab and then "custom rules":
Then write there the iptables rules.