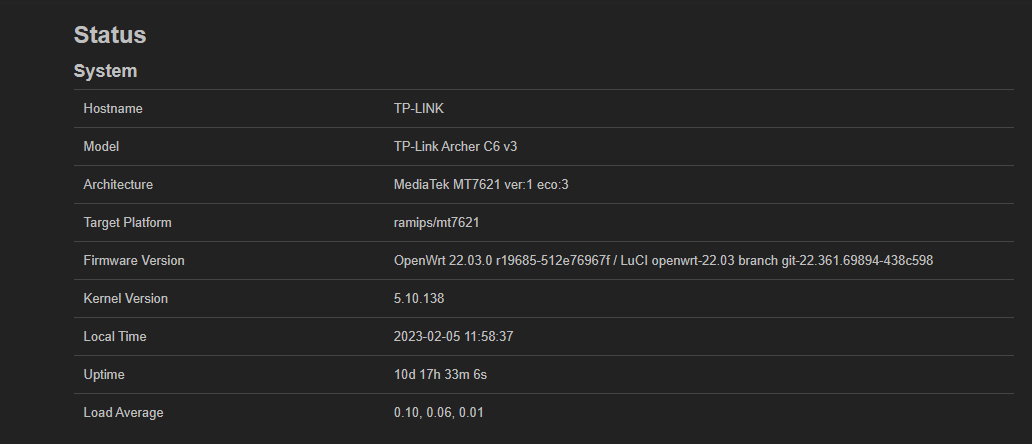
After almost 6 days of uptime with 22.03.0 , the device rebooted suddendly. So the issue is in 22.03.0 also.
Alright, I now join the club of fellow crashers! One device that is under pretty good load since last week has seen rather frequent crashes of wifi that somehow fix themselves after 10 - 15 minutes or, as is the case for some of you, after a reboot of the device.
The latest crash about an hour ago was not preceeded by any error in the logread ( ran -f since 8 a.m. CET); at least not before my ssh connection via wireguard was broken. After reboot on premise the log is lost of course.
I'll try to figure out some debugging measures. The workload in the past few hours should've been the same as yesterday, when no crashes occured. Roughly 12- 15 devices are connected most of the time with traffic ranging from VoIP-/Videocalls, regular websurfing, using streaming services to additional VPN-connections.
This behaviour has occured with v22.03.2, and yesterday and today have been run with v22.03.3.
Can someone confirm that the issue is [not] present on Archer C6U with the current release or master?
I'm considering buying one for the relatives...
well should be the same i think
And then, after 2 days and almost a half hour, I catched the issue from the start (22.03.0 but with 22.03.2 is the same). The RAM memory raised to almost 100 MB of occupation, and after a "wifi" command, the RAM droped down again to normal values (less than 55 MB).
The logs and relevant info i catched while the issue was occuring are:
root@OpenWrt:~# uptime
17:44:13 up 2 days, 28 min, load average: 0.30, 0.38, 0.43
root@OpenWrt:~# ps
PID USER VSZ STAT COMMAND
1 root 1684 S /sbin/procd
2 root 0 SW [kthreadd]
3 root 0 IW< [rcu_gp]
4 root 0 IW< [rcu_par_gp]
6 root 0 IW< [kworker/0:0H-ev]
8 root 0 IW< [mm_percpu_wq]
9 root 0 SW [rcu_tasks_trace]
10 root 0 SW [ksoftirqd/0]
11 root 0 IW [rcu_sched]
12 root 0 SW [migration/0]
13 root 0 SW [cpuhp/0]
14 root 0 SW [cpuhp/1]
15 root 0 SW [migration/1]
16 root 0 SW [ksoftirqd/1]
19 root 0 SW [cpuhp/2]
20 root 0 SW [migration/2]
21 root 0 SW [ksoftirqd/2]
24 root 0 SW [cpuhp/3]
25 root 0 SW [migration/3]
26 root 0 SW [ksoftirqd/3]
29 root 0 IW< [netns]
40 root 0 IW [kworker/3:1-mm_]
178 root 0 SW [oom_reaper]
179 root 0 IW< [writeback]
180 root 0 SW [kcompactd0]
190 root 0 IW< [pencrypt_serial]
192 root 0 IW< [pdecrypt_serial]
193 root 0 IW [kworker/2:1-eve]
207 root 0 IW< [kblockd]
209 root 0 IW< [blkcg_punt_bio]
227 root 0 SW [watchdogd]
240 root 0 IW< [kworker/2:1H-ev]
250 root 0 SW [kswapd0]
251 root 0 IW< [kthrotld]
284 root 0 SW [spi0]
368 root 0 IW< [ipv6_addrconf]
369 root 0 IW< [dsa_ordered]
370 root 0 IW< [kworker/1:1H-kb]
373 root 0 SW [irq/25-mt7530]
425 root 0 IW [kworker/1:4-eve]
427 root 0 IW [kworker/1:6-mm_]
428 root 0 IW< [kworker/3:1H-ev]
431 root 0 IW< [kworker/0:2H-ev]
434 root 0 SW [irq/31-keys]
435 root 0 SW [irq/32-keys]
440 root 0 IW [kworker/3:2-rcu]
452 root 0 IW< [kworker/1:2H-ev]
507 root 0 IW [kworker/2:2-mm_]
536 root 0 SWN [jffs2_gcd_mtd4]
567 root 0 IW< [kworker/2:2H-ev]
585 root 0 IW< [kworker/3:2H]
586 ubus 1368 S /sbin/ubusd
587 root 1000 S /sbin/askfirst /usr/libexec/login.sh
622 root 1116 S /sbin/urngd
720 root 0 IW< [cfg80211]
745 root 0 SW [napi/phy0-7]
746 root 0 SW [napi/phy0-8]
755 root 0 SW [mt76-tx phy0]
760 root 0 SW [napi/phy1-9]
761 root 0 SW [napi/phy1-10]
769 root 0 SW [mt76-tx phy1]
1017 logd 1352 S /sbin/logd -S 64
1101 root 1928 S /sbin/rpcd -s /var/run/ubus/ubus.sock -t 30
1288 root 2664 S {dnsmasq} /sbin/ujail -t 5 -n dnsmasq -u -l -r /bin/ubus -r /etc/TZ -r /etc/dnsmasq.conf -r /etc/ethers -r /etc/group -r /e
1336 dnsmasq 1504 S /usr/sbin/dnsmasq -C /var/etc/dnsmasq.conf.cfg01411c -k -x /var/run/dnsmasq/dnsmasq.cfg01411c.pid
1353 root 1216 S /usr/sbin/dropbear -F -P /var/run/dropbear.1.pid -p 22 -K 300 -T 3
1457 root 2664 S {hostapd} /sbin/ujail -t 5 -n hostapd -U network -G network -C /etc/capabilities/wpad.json -c -- /usr/sbin/hostapd -s -g /v
1458 root 2664 S {wpa_supplicant} /sbin/ujail -t 5 -n wpa_supplicant -U network -G network -C /etc/capabilities/wpad.json -c -- /usr/sbin/wp
1477 network 2544 S /usr/sbin/hostapd -s -g /var/run/hostapd/global
1478 network 2452 S /usr/sbin/wpa_supplicant -n -s -g /var/run/wpa_supplicant/global
1522 root 1992 S /sbin/netifd
1578 root 1540 S /usr/sbin/odhcpd
1704 root 2612 S /usr/sbin/uhttpd -f -h /www -r OpenWrt -x /cgi-bin -l /controller_status_check -L /www/mesh_network/lua/controller_status_c
2019 root 2664 S {ntpd} /sbin/ujail -t 5 -n ntpd -U ntp -G ntp -C /etc/capabilities/ntpd.json -c -u -r /bin/ubus -r /usr/bin/env -r /usr/bin
2045 ntp 1312 S /usr/sbin/ntpd -n -N -S /usr/sbin/ntpd-hotplug -p 0.openwrt.pool.ntp.org -p 1.openwrt.pool.ntp.org -p 2.openwrt.pool.ntp.or
2107 root 1384 S ash /usr/horus_lite/horus_lite.sh
2194 root 1312 S ash /usr/simplemesh/mesh.sh
2257 root 11720 S python3 -B mesh.py
2611 root 1312 S udhcpc -p /var/run/udhcpc-br-lan.pid -s /lib/netifd/dhcp.script -f -t 0 -i br-lan -r 192.168.1.1 -x hostname:OpenWrt -C -R
3729 root 0 IW [kworker/0:0]
26058 root 0 IW [kworker/u8:0-ph]
27083 root 0 IW [kworker/u8:1-ev]
27949 root 0 IW< [kworker/1:0H-ev]
28428 root 1236 R /usr/sbin/dropbear -F -P /var/run/dropbear.1.pid -p 22 -K 300 -T 3 -2 9
28429 root 1316 S -ash
28431 root 0 IW [kworker/u8:2-ev]
28482 root 1312 S sleep 10
28488 root 1320 R ps
30802 root 0 IW [kworker/0:1-eve]
The sum of VSZ is 55188 (55 MB?) so I do not find coincidence with the "free" command or "top" which shows an occupation of 100 MB.
root@OpenWrt:~# free
total used free shared buff/cache available
Mem: 120584 83236 22604 88 14744 5364
Swap: 0 0 0
root@OpenWrt:~# dmesg
[ 21.856078] br-lan: port 5(wan) entered blocking state
[ 21.861383] br-lan: port 5(wan) entered disabled state
[ 21.868340] device wan entered promiscuous mode
[ 23.434243] br-lan: port 6(bss0) entered blocking state
[ 23.439549] br-lan: port 6(bss0) entered disabled state
[ 23.445624] device bss0 entered promiscuous mode
[ 24.910849] br-lan: port 7(bss1) entered blocking state
[ 24.916188] br-lan: port 7(bss1) entered disabled state
[ 24.922161] device bss1 entered promiscuous mode
[ 24.927232] br-lan: port 7(bss1) entered blocking state
[ 24.932751] br-lan: port 7(bss1) entered forwarding state
[ 24.939183] br-lan: port 7(bss1) entered disabled state
[ 25.917626] IPv6: ADDRCONF(NETDEV_CHANGE): bss0: link becomes ready
[ 25.924280] br-lan: port 6(bss0) entered blocking state
[ 25.929506] br-lan: port 6(bss0) entered forwarding state
[ 25.937397] IPv6: ADDRCONF(NETDEV_CHANGE): br-lan: link becomes ready
[ 32.198502] IPv6: ADDRCONF(NETDEV_CHANGE): bss1: link becomes ready
[ 32.205174] br-lan: port 7(bss1) entered blocking state
[ 32.210402] br-lan: port 7(bss1) entered forwarding state
[ 32.257399] br-lan: port 8(bss2) entered blocking state
[ 32.262717] br-lan: port 8(bss2) entered disabled state
[ 32.268456] device bss2 entered promiscuous mode
[ 32.284527] br-lan: port 8(bss2) entered blocking state
[ 32.289828] br-lan: port 8(bss2) entered forwarding state
[ 32.709301] IPv6: ADDRCONF(NETDEV_CHANGE): bss2: link becomes ready
[ 33.445483] mt7530 mdio-bus:1f wan: Link is Up - 1Gbps/Full - flow control rx/tx
[ 33.452960] br-lan: port 5(wan) entered blocking state
[ 33.458102] br-lan: port 5(wan) entered forwarding state
[ 39.637969] IPv6: ADDRCONF(NETDEV_CHANGE): e-1905: link becomes ready
[ 39.646260] br-lan: port 9(p-1905) entered blocking state
[ 39.651797] br-lan: port 9(p-1905) entered disabled state
[ 39.658255] device p-1905 entered promiscuous mode
[ 39.663925] br-lan: port 9(p-1905) entered blocking state
[ 39.669387] br-lan: port 9(p-1905) entered forwarding state
[ 39.680933] br-lan: port 9(p-1905) entered disabled state
[ 39.699252] br-lan: port 9(p-1905) entered blocking state
[ 39.704769] br-lan: port 9(p-1905) entered forwarding state
[ 43.739443] br-lan: port 10(bss2.sta1) entered blocking state
[ 43.745294] br-lan: port 10(bss2.sta1) entered disabled state
[ 43.751911] device bss2.sta1 entered promiscuous mode
[ 43.757318] br-lan: port 10(bss2.sta1) entered blocking state
[ 43.763381] br-lan: port 10(bss2.sta1) entered forwarding state
[ 51.894508] br-lan: port 10(bss2.sta1) entered disabled state
[ 51.992286] device bss2.sta1 left promiscuous mode
[ 51.997162] br-lan: port 10(bss2.sta1) entered disabled state
[ 52.983904] br-lan: port 10(bss2.sta1) entered blocking state
[ 52.989698] br-lan: port 10(bss2.sta1) entered disabled state
[ 52.996447] device bss2.sta1 entered promiscuous mode
[ 53.002199] br-lan: port 10(bss2.sta1) entered blocking state
[ 53.007966] br-lan: port 10(bss2.sta1) entered forwarding state
[ 69.351290] br-lan: port 11(bss2.sta2) entered blocking state
[ 69.357075] br-lan: port 11(bss2.sta2) entered disabled state
[ 69.363358] device bss2.sta2 entered promiscuous mode
[ 69.368810] br-lan: port 11(bss2.sta2) entered blocking state
[ 69.374918] br-lan: port 11(bss2.sta2) entered forwarding state
[ 107.193746] br-lan: port 10(bss2.sta1) entered disabled state
[ 107.251799] device bss2.sta1 left promiscuous mode
[ 107.256620] br-lan: port 10(bss2.sta1) entered disabled state
[ 116.867663] br-lan: port 10(bss2.sta1) entered blocking state
[ 116.873540] br-lan: port 10(bss2.sta1) entered disabled state
[ 116.879821] device bss2.sta1 entered promiscuous mode
[ 116.885560] br-lan: port 10(bss2.sta1) entered blocking state
[ 116.891466] br-lan: port 10(bss2.sta1) entered forwarding state
[ 175.992168] mt7530 mdio-bus:1f wan: Link is Down
[ 175.996918] br-lan: port 5(wan) entered disabled state
[ 184.235756] mt7530 mdio-bus:1f wan: Link is Up - 1Gbps/Full - flow control rx/tx
[ 184.243244] br-lan: port 5(wan) entered blocking state
[ 184.248372] br-lan: port 5(wan) entered forwarding state
[105011.396832] mt7530 mdio-bus:1f lan3: Link is Up - 1Gbps/Full - flow control rx/tx
[105011.404482] br-lan: port 3(lan3) entered blocking state
[105011.409781] br-lan: port 3(lan3) entered forwarding state
[105167.707900] mt7530 mdio-bus:1f lan3: Link is Down
[105167.713229] br-lan: port 3(lan3) entered disabled state
[105284.163644] mt7530 mdio-bus:1f lan3: Link is Up - 1Gbps/Full - flow control rx/tx
[105284.171300] br-lan: port 3(lan3) entered blocking state
[105284.176603] br-lan: port 3(lan3) entered forwarding state
[106805.036466] mt7530 mdio-bus:1f lan3: Link is Down
[106805.042065] br-lan: port 3(lan3) entered disabled state
root@OpenWrt:~# logread
Tue Feb 7 03:39:55 2023 authpriv.info dropbear[26707]: Child connection from 192.168.0.43:60905
Tue Feb 7 03:39:55 2023 authpriv.notice dropbear[26707]: Auth succeeded with blank password for 'root' from 192.168.0.43:60905
Tue Feb 7 03:40:23 2023 authpriv.info dropbear[26707]: Exit (root) from <192.168.0.43:60905>: Error reading: Connection reset by peer
Tue Feb 7 03:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 03:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 04:12:48 2023 daemon.warn dnsmasq[1]: possible DNS-rebind attack detected: dns.msftncsi.com
Tue Feb 7 04:12:48 2023 daemon.warn dnsmasq[679]: possible DNS-rebind attack detected: dns.msftncsi.com
Tue Feb 7 04:12:49 2023 daemon.warn dnsmasq[1]: possible DNS-rebind attack detected: dns.msftncsi.com
Tue Feb 7 04:12:49 2023 daemon.warn dnsmasq[680]: possible DNS-rebind attack detected: dns.msftncsi.com
Tue Feb 7 04:12:49 2023 daemon.warn dnsmasq[1]: possible DNS-rebind attack detected: dns.msftncsi.com
Tue Feb 7 04:12:49 2023 daemon.warn dnsmasq[681]: possible DNS-rebind attack detected: dns.msftncsi.com
Tue Feb 7 04:12:49 2023 daemon.warn dnsmasq[1]: possible DNS-rebind attack detected: dns.msftncsi.com
Tue Feb 7 04:12:49 2023 daemon.warn dnsmasq[682]: possible DNS-rebind attack detected: dns.msftncsi.com
Tue Feb 7 04:12:49 2023 daemon.warn dnsmasq[1]: possible DNS-rebind attack detected: dns.msftncsi.com
Tue Feb 7 04:12:49 2023 daemon.warn dnsmasq[683]: possible DNS-rebind attack detected: dns.msftncsi.com
Tue Feb 7 04:12:49 2023 daemon.warn dnsmasq[1]: possible DNS-rebind attack detected: dns.msftncsi.com
Tue Feb 7 04:12:51 2023 daemon.notice hostapd: bss1: AP-STA-DISCONNECTED 2c:db:07:54:47:7d
Tue Feb 7 04:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 04:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 04:48:55 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 04:48:55 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 05:18:55 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 05:18:55 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 05:48:55 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 05:48:55 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 06:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 06:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 06:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 06:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 07:09:00 2023 daemon.info dnsmasq[1]: read /etc/hosts - 4 addresses
Tue Feb 7 07:09:00 2023 daemon.info dnsmasq[1]: read /tmp/hosts/dhcp.cfg01411c - 0 addresses
Tue Feb 7 07:09:00 2023 daemon.info dnsmasq[1]: read /tmp/hosts/odhcpd - 2 addresses
Tue Feb 7 07:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 07:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 07:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 07:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 08:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 08:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 08:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 08:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 09:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 09:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 09:48:57 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 09:48:57 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 10:18:57 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 10:18:57 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 10:48:57 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 10:48:57 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 11:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 11:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 11:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 11:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 12:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 12:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 12:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 12:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 12:56:41 2023 daemon.info dnsmasq[1]: read /etc/hosts - 4 addresses
Tue Feb 7 12:56:41 2023 daemon.info dnsmasq[1]: read /tmp/hosts/dhcp.cfg01411c - 0 addresses
Tue Feb 7 12:56:41 2023 daemon.info dnsmasq[1]: read /tmp/hosts/odhcpd - 1 addresses
Tue Feb 7 13:18:57 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 13:18:57 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 13:32:02 2023 daemon.info dnsmasq[1]: read /etc/hosts - 4 addresses
Tue Feb 7 13:32:02 2023 daemon.info dnsmasq[1]: read /tmp/hosts/dhcp.cfg01411c - 0 addresses
Tue Feb 7 13:32:02 2023 daemon.info dnsmasq[1]: read /tmp/hosts/odhcpd - 2 addresses
Tue Feb 7 13:36:23 2023 daemon.info hostapd: bss1: STA 2c:db:07:54:47:7d IEEE 802.11: authenticated
Tue Feb 7 13:36:23 2023 daemon.info hostapd: bss1: STA 2c:db:07:54:47:7d IEEE 802.11: associated (aid 1)
Tue Feb 7 13:36:23 2023 daemon.notice hostapd: bss1: STA-OPMODE-SMPS-MODE-CHANGED 2c:db:07:54:47:7d off
Tue Feb 7 13:36:23 2023 daemon.notice hostapd: bss1: AP-STA-CONNECTED 2c:db:07:54:47:7d
Tue Feb 7 13:36:23 2023 daemon.info hostapd: bss1: STA 2c:db:07:54:47:7d RADIUS: starting accounting session EC02B420B72BA50A
Tue Feb 7 13:36:23 2023 daemon.info hostapd: bss1: STA 2c:db:07:54:47:7d WPA: pairwise key handshake completed (RSN)
Tue Feb 7 13:36:23 2023 daemon.notice hostapd: bss1: EAPOL-4WAY-HS-COMPLETED 2c:db:07:54:47:7d
Tue Feb 7 13:36:24 2023 daemon.info dnsmasq[1]: read /etc/hosts - 4 addresses
Tue Feb 7 13:36:24 2023 daemon.info dnsmasq[1]: read /tmp/hosts/dhcp.cfg01411c - 0 addresses
Tue Feb 7 13:36:24 2023 daemon.info dnsmasq[1]: read /tmp/hosts/odhcpd - 3 addresses
Tue Feb 7 13:48:57 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 13:48:57 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 13:49:04 2023 daemon.info hostapd: bss1: STA 2c:db:07:54:47:7d IEEE 802.11: disconnected due to excessive missing ACKs
Tue Feb 7 13:49:04 2023 daemon.notice hostapd: bss1: AP-STA-DISCONNECTED 2c:db:07:54:47:7d
Tue Feb 7 13:49:05 2023 daemon.info hostapd: bss1: STA 2c:db:07:54:47:7d IEEE 802.11: authenticated
Tue Feb 7 13:49:05 2023 daemon.info hostapd: bss1: STA 2c:db:07:54:47:7d IEEE 802.11: associated (aid 1)
Tue Feb 7 13:49:05 2023 daemon.notice hostapd: bss1: STA-OPMODE-SMPS-MODE-CHANGED 2c:db:07:54:47:7d off
Tue Feb 7 13:49:05 2023 daemon.notice hostapd: bss1: AP-STA-CONNECTED 2c:db:07:54:47:7d
Tue Feb 7 13:49:05 2023 daemon.info hostapd: bss1: STA 2c:db:07:54:47:7d RADIUS: starting accounting session EC02B420B72BA50A
Tue Feb 7 13:49:05 2023 daemon.info hostapd: bss1: STA 2c:db:07:54:47:7d WPA: pairwise key handshake completed (RSN)
Tue Feb 7 13:49:05 2023 daemon.notice hostapd: bss1: EAPOL-4WAY-HS-COMPLETED 2c:db:07:54:47:7d
Tue Feb 7 14:18:57 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 14:18:57 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 14:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 14:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 15:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 15:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 15:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 15:48:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 16:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 16:18:56 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 16:48:57 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 16:48:57 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 17:15:59 2023 daemon.info hostapd: bss1: STA 2c:db:07:54:47:7d WPA: group key handshake completed (RSN)
Tue Feb 7 17:16:00 2023 daemon.info hostapd: bss2: STA 00:31:92:04:14:e2 WPA: group key handshake completed (RSN)
Tue Feb 7 17:16:00 2023 daemon.info hostapd: bss2: STA 60:a4:b7:7c:6c:8e WPA: group key handshake completed (RSN)
Tue Feb 7 17:18:57 2023 daemon.notice netifd: lan (2611): udhcpc: sending renew to server 192.168.0.1
Tue Feb 7 17:18:57 2023 daemon.notice netifd: lan (2611): udhcpc: lease of 192.168.0.70 obtained from 192.168.0.1, lease time 3600
Tue Feb 7 17:32:53 2023 daemon.notice hostapd: bss1: AP-STA-DISCONNECTED 2c:db:07:54:47:7d
Tue Feb 7 17:32:54 2023 daemon.info dnsmasq[1]: read /etc/hosts - 4 addresses
Tue Feb 7 17:32:54 2023 daemon.info dnsmasq[1]: read /tmp/hosts/dhcp.cfg01411c - 0 addresses
Tue Feb 7 17:32:54 2023 daemon.info dnsmasq[1]: read /tmp/hosts/odhcpd - 2 addresses
Tue Feb 7 17:34:34 2023 daemon.info dnsmasq[1]: read /etc/hosts - 4 addresses
Tue Feb 7 17:34:34 2023 daemon.info dnsmasq[1]: read /tmp/hosts/dhcp.cfg01411c - 0 addresses
Tue Feb 7 17:34:34 2023 daemon.info dnsmasq[1]: read /tmp/hosts/odhcpd - 3 addresses
Tue Feb 7 17:42:10 2023 authpriv.info dropbear[28428]: Child connection from 192.168.0.43:55858
Tue Feb 7 17:42:10 2023 authpriv.notice dropbear[28428]: Auth succeeded with blank password for 'root' from 192.168.0.43:55858
After the "wifi" command, all seems to be working normally:
Mem: 50692K used, 69892K free, 88K shrd, 0K buff, 10976K cached
CPU: 2% usr 2% sys 0% nic 95% idle 0% io 0% irq 0% sirq
Load average: 0.31 0.33 0.40 2/107 30236
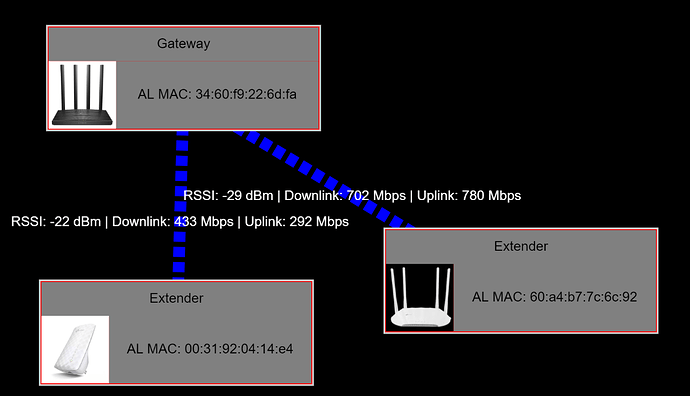
To give more context, I have the following topology, which the Archer C6v3 as main AP, and both extenders connected via MultiAP WDS:
I also have something like a "periodic inform" daemon on each device, so I can track which devices are online. When this issue occurs, the extenders lose their connectivity. This can be seen in this graph in the instant where two devices (the extenders in the previous image) have been lost due to the issue in the WDS connection and the quick recover after the "wifi" command in the C6:
Undoubtedly the issue is related to WiFi, but I don't find who is filling up the ram and why
Basic question. Can anyone recommend a router model that works stably on Openwrt for more than 10 days or more without crashing?. I need something stable for my clients. I don't want to waste my time testing forever.
Yeeaaah, I have uptime over 30 days as only one client is connected to the router: a central heating stove. Same router with 10 users online kaputt/amen/crash after 3 days
Out of interest, has anyone tried building a 21.02.x image for the C6 v3? There was a patch for support (basically copying the config for the A6 v3) but it didn’t get merged in time. It shouldn’t be too hard to build and it may not have the issues we’re seeing in 22.03.x
See GitHub PR and the support patch
For hardware recommendations please open a new topic in the Hardware Questions and Recommendations category of this forum.
Please see https://openwrt.org/faq/which_router_should_i_buy before asking for recommendations. This way you will get better recommendations and come to a quicker solution.
Thanks! ![]()
While I am still on the lookout for the actual cause, I have implemented a script via cronjob that restarts the wifi in case of excessive memory consumption. Under (somewhat) regular usage, the device seems to use around 30000K to 35000K when checking via free. I took the data you posted, with 83236K used as indicator for memory consumption level before crash/wifi restart command.
To be on the safe side for now, and while I am waiting for user reports over the next days and week, I have set the threshold to 75000k. Time will tell if that is sufficient or too low.
Here is the short script I wrote, it is running via cronjob every 10 minutes:
#!/bin/ash
#Due to currently unknown issues, MT7621 targets experience infrequent complete memory consumption.
#This leads to wifi and device crashing. This is possibly related to wifi driver issues under v22.03 releases 0 to 3.
#Workaround test is implementing a free memory check that issues a wifi down & wifi up command in case of apparent memory consumption close to max.
usedmem=$(free | grep "Mem" | cut -d' ' -f17)
freemem=$(free | grep "Mem" | cut -d' ' -f24)
#Archer C6v3 runs with 128MB RAM.
#Standard memory consumption fluctuates around 30MB.
if [ $usedmem -gt 75000 ]; then
wifi
echo "WARNING: Wifi restart due to excessive memory consumption"
fi
Hopefully there opens up an explanation for the issues somewhat soon. Workarounds in cases like these are never satisfying.
How to install the script? I use Wi-Fi Scheduler with a one minute radio off setting everynight at 2 am, I managed to get almost 23 days of uptime but today we had a power outage and I can't show the router page with the uptime.
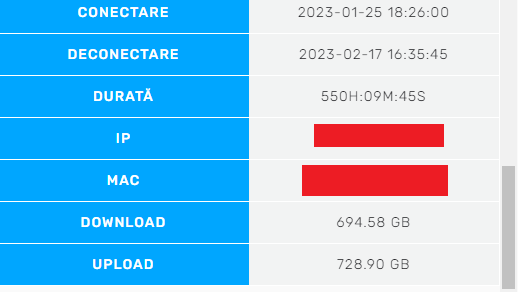
Here's a screenshot from my ISP log page, first says "Connection date", second "Disconnect date" and the third is "Total Uptime" of PPPoE session, total 550 hours and 9 minutes of PPPoE uptime.
I guess you need to do it via CLI after login onto the router via ssh. If you are not familiar with that route, you'll find the necessary information here: https://openwrt.org/docs/guide-user/base-system/user.beginner.cli
After loging in, I created a file with vi /usr/sbin/memorycheck.sh and pasted my script into it. Then I made the file executable with chmod +x /usr/sbin/memorycheck.sh. Finally I created a cronjob that executes the script every 10 minutes with crontab -e and adding a new line with */10 * * * * /usr/sbin/memorycheck.sh
To stop the "cron.err" message to spam in systemlog every 10 minutes I changed in /etc/config/system the value of cronloglevel to 9, default is 8, that in case anyone don't know how to get rid of it.
TP-LINK has released patches for Archer C6 v3.20, you can see that there is a problem.
I noticed that the problem is with the WAN input autonegotiation does not work properly.
I'll check if they fixed it in the new patch.
Openwrt no longer installs at all until this is fixed.
Archer C6(EU)_V3.2_220923 original tplink
Charge
Date of publication: 2023-01-10 Language: multilingual File size: 14.87 MB
Modifications and bug fixes:
- Fixed some dial-up bugs;
- Fixed some bugs related to wireless connectivity;
- Fix the bug that the website does not show wireless clients in AP mode;
- Fix the error that the computer in the LAN cannot access the device via the DDNS domain name when enabling DynDNS and remote control;
- IPTV and QoS mutual restriction removed;
- Optimized smart linking function.
Good to know, I will refrain from upgrading stock firmware before flashing new devices then. Thank you for the headsup.
From his ranting all over the place about his routers crashing it's not clear what he means with "OpenWrt no longer installs"
Yet we saw no bug report about his crashy routers.
I've been running this script for a while. I am still getting crashes, but not as regularly.