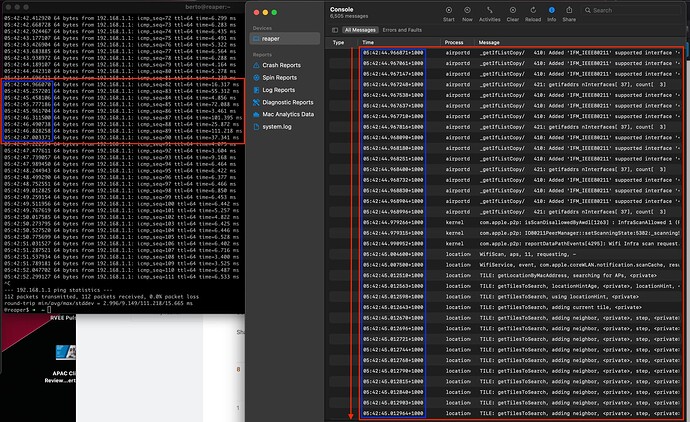
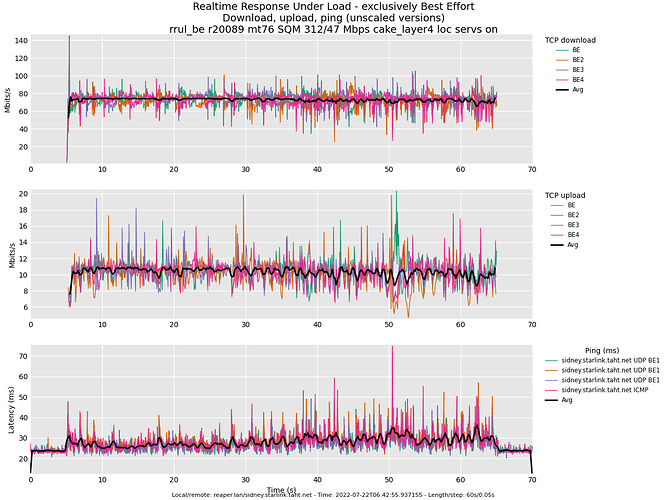
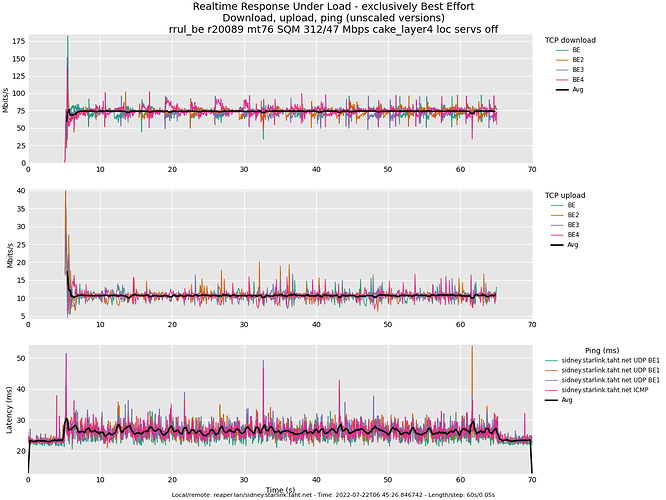
Follow-up question. I gather that attention was recently afforded to multicast data. What about traffic like this:
root@OpenWrt:~# tcpdump -vpni br-guest
tcpdump: listening on br-guest, link-type EN10MB (Ethernet), capture size 262144 bytes
22:06:08.043450 IP (tos 0x0, ttl 255, id 53539, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.192.49154 > 255.255.255.255.6666: UDP, length 175
22:06:08.514987 IP (tos 0x0, ttl 255, id 53529, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.191.49154 > 255.255.255.255.6666: UDP, length 175
22:06:08.529170 IP (tos 0x0, ttl 255, id 53525, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.156.49154 > 255.255.255.255.6666: UDP, length 175
22:06:09.398553 IP (tos 0x0, ttl 255, id 34152, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.109.49154 > 255.255.255.255.6667: UDP, length 188
22:06:09.846746 IP (tos 0x0, ttl 255, id 34157, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.200.49154 > 255.255.255.255.6667: UDP, length 188
22:06:10.085035 IP (tos 0x0, ttl 255, id 34150, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.134.49154 > 255.255.255.255.6667: UDP, length 188
22:06:10.085365 IP (tos 0x0, ttl 255, id 34150, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.134.49154 > 255.255.255.255.6667: UDP, length 188
22:06:10.269147 IP (tos 0x0, ttl 255, id 52923, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.179.49155 > 255.255.255.255.6667: UDP, length 188
22:06:10.527005 IP (tos 0x0, ttl 255, id 53528, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.119.49154 > 255.255.255.255.6666: UDP, length 175
22:06:10.564785 IP (tos 0x0, ttl 255, id 34171, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.128.49154 > 255.255.255.255.6667: UDP, length 188
22:06:11.043718 IP (tos 0x0, ttl 255, id 53540, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.192.49154 > 255.255.255.255.6666: UDP, length 175
22:06:11.513351 IP (tos 0x0, ttl 255, id 53530, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.191.49154 > 255.255.255.255.6666: UDP, length 175
22:06:11.530135 IP (tos 0x0, ttl 255, id 53526, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.156.49154 > 255.255.255.255.6666: UDP, length 175
22:06:12.074089 IP (tos 0x0, ttl 255, id 47449, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.118.49154 > 255.255.255.255.6667: UDP, length 188
22:06:12.102683 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.2.179 tell 192.168.2.179, length 28
22:06:12.374825 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.2.109 tell 192.168.2.109, length 28
22:06:12.776482 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.2.134 tell 192.168.2.134, length 28
22:06:12.903406 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.2.200 tell 192.168.2.200, length 28
22:06:13.520926 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.2.128 tell 192.168.2.128, length 28
22:06:13.529649 IP (tos 0x0, ttl 255, id 53529, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.119.49154 > 255.255.255.255.6666: UDP, length 175
22:06:14.042985 IP (tos 0x0, ttl 255, id 53541, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.192.49154 > 255.255.255.255.6666: UDP, length 175
22:06:14.395631 IP (tos 0x0, ttl 255, id 34153, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.109.49154 > 255.255.255.255.6667: UDP, length 188
22:06:14.486113 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.2.118 tell 192.168.2.118, length 28
22:06:14.514464 IP (tos 0x0, ttl 255, id 53531, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.191.49154 > 255.255.255.255.6666: UDP, length 175
22:06:14.524313 IP (tos 0x0, ttl 255, id 53527, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.156.49154 > 255.255.255.255.6666: UDP, length 175
22:06:14.846485 IP (tos 0x0, ttl 255, id 34158, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.200.49154 > 255.255.255.255.6667: UDP, length 188
22:06:15.085166 IP (tos 0x0, ttl 255, id 34151, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.134.49154 > 255.255.255.255.6667: UDP, length 188
22:06:15.270983 IP (tos 0x0, ttl 255, id 52924, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.179.49155 > 255.255.255.255.6667: UDP, length 188
22:06:15.564898 IP (tos 0x0, ttl 255, id 34172, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.128.49154 > 255.255.255.255.6667: UDP, length 188
22:06:16.527908 IP (tos 0x0, ttl 255, id 53530, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.119.49154 > 255.255.255.255.6666: UDP, length 175
22:06:17.043297 IP (tos 0x0, ttl 255, id 53542, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.192.49154 > 255.255.255.255.6666: UDP, length 175
22:06:17.073189 IP (tos 0x0, ttl 255, id 47450, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.118.49154 > 255.255.255.255.6667: UDP, length 188
22:06:17.514675 IP (tos 0x0, ttl 255, id 53532, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.191.49154 > 255.255.255.255.6666: UDP, length 175
22:06:17.528499 IP (tos 0x0, ttl 255, id 53528, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.156.49154 > 255.255.255.255.6666: UDP, length 175
22:06:19.399187 IP (tos 0x0, ttl 255, id 34154, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.109.49154 > 255.255.255.255.6667: UDP, length 188
22:06:19.528582 IP (tos 0x0, ttl 255, id 53531, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.119.49154 > 255.255.255.255.6666: UDP, length 175
22:06:19.848940 IP (tos 0x0, ttl 255, id 34159, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.200.49154 > 255.255.255.255.6667: UDP, length 188
22:06:20.048174 IP (tos 0x0, ttl 255, id 53543, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.192.49154 > 255.255.255.255.6666: UDP, length 175
22:06:20.085719 IP (tos 0x0, ttl 255, id 34152, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.134.49154 > 255.255.255.255.6667: UDP, length 188
22:06:20.269806 IP (tos 0x0, ttl 255, id 52925, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.179.49155 > 255.255.255.255.6667: UDP, length 188
22:06:20.510184 IP (tos 0x0, ttl 255, id 53533, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.191.49154 > 255.255.255.255.6666: UDP, length 175
22:06:20.525346 IP (tos 0x0, ttl 255, id 53529, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.156.49154 > 255.255.255.255.6666: UDP, length 175
22:06:20.562477 IP (tos 0x0, ttl 255, id 34173, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.128.49154 > 255.255.255.255.6667: UDP, length 188
22:06:22.073323 IP (tos 0x0, ttl 255, id 47451, offset 0, flags [none], proto UDP (17), length 216)
192.168.2.118.49154 > 255.255.255.255.6667: UDP, length 188
22:06:22.099811 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.2.179 tell 192.168.2.179, length 28
22:06:22.375276 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.2.109 tell 192.168.2.109, length 28
22:06:22.523823 IP (tos 0x0, ttl 255, id 53532, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.119.49154 > 255.255.255.255.6666: UDP, length 175
22:06:22.771964 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.2.134 tell 192.168.2.134, length 28
22:06:22.905432 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.2.200 tell 192.168.2.200, length 28
22:06:23.043737 IP (tos 0x0, ttl 255, id 53544, offset 0, flags [none], proto UDP (17), length 203)
192.168.2.192.49154 > 255.255.255.255.6666: UDP, length 175
Could such IoT device traffic be the cause of lag on 2.4Ghz?