TP-Link APs allow to filter traffic so that you can create an SSID like "OnlyLocal". Then you can set up that only access to local subnet is allowed. Clients in "OnlyLocal" get the same IP/are on the same subnet like clients in "FullAccess".
Is that possible with OpenWRT? I guess so. Can you point my to the right documentation?
In general, not on any device (traffic addressed for the same subnet does not need to pass the routing/firewall engine of the Kernel and never reaches it).
But...if you place these devices on different VLANs and bridge them for example...there may be some bridge filtering you could implement. I'm not too familiar with that - I'm sure others will chime in.
Do you have some use case where you need only broadcast packets or something?
Otherwise, I don't see why you don't setup another interface/network/IP range/SSID/etc. and only permit Firewall default forwarding to FullAccess? ![]()
Found out how this is possible.
You need to install
opkg update
opkg install kmod-br-netfilter iptables-mod-physdev
This module is responsible for availability of -m physdev in iptables
This module forwards Layer 2 packets to Layer 3 so iptables/netfilter can handle.
You have to enable this behavior:
#runtime
sysctl -w net.bridge.bridge-nf-call-iptables=1
#make changes permanent
cat << EOF >> /etc/sysctl.conf
net.bridge.bridge-nf-call-iptables=1
EOF
Give the interface the SSID "OnlyLocal" runs on a name. This makes it much easier transferring the rule to another device.
a) Webinterface
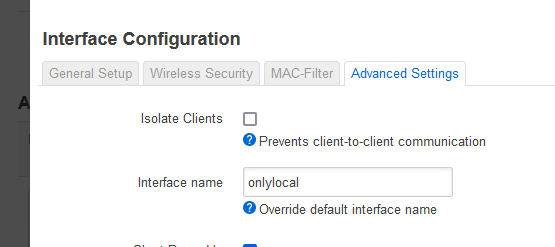
or
b) /etc/config/wireless
config wifi-iface 'OnlyLocal'
option device 'radio0'
option mode 'ap'
option ssid 'OnlyLocal'
option encryption 'sae-mixed'
option max_inactivity '3600'
option key 'uN5fSfBuHrtLCVK1ydx1'
option ieee80211r '1'
option mobility_domain '1111'
option ft_over_ds '0'
option ft_psk_generate_local '1'
option network 'lan'
option ifname 'onlylocal'
Important is the last line, not the first with config wifi-iface
Now set a custom rule
iptables -I FORWARD ! -d 192.168.1.1/24 -m physdev --physdev-in onlylocal -m comment --comment "Only Local" -j REJECT
iptables -I FORWARD -d 255.255.255.255 -m physdev --physdev-in oertlich -m comment --comment "Broadcast / DHCP" -j ACCEPT
Done. Now devices in SSID OnlyLocal can only access local network.
Note:
If you're using tagged VLANs according to IEEE 802.1Q and as soon as you set sysctl -w net.bridge.bridge-nf-call-iptables=1 you need two special rules, because OpenWRTs default FORWARD policy is to drop and none of the predefined policies will match. So your SSIDs configured to a VLAN won't work anymore.
When using a VLAN19 like described there Use SSID in specific VLAN - Wifi connection can not be established - #15 by VLANMaster you need these settings:
iptables -I FORWARD -m physdev --physdev-in eth0.19 -m comment --comment "VLAN19" -j ACCEPT
iptables -I FORWARD -m physdev --physdev-out eth0.19 -m comment --comment "VLAN19" -j ACCEPT
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.
