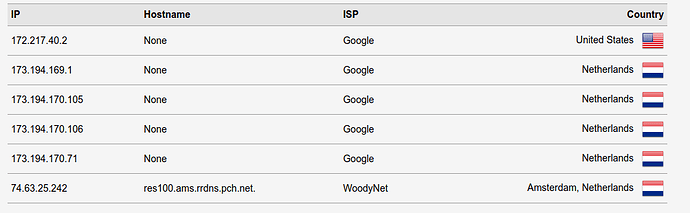
Hello dear OpenWRT forum members!
I followed this official user guide to the letter and added the Quad9 servers instead of the Google and Cloudflare servers. After completing the guide the resolution went via WoodyNet which is right for Quad9. Unfortunately after a reboot of the router (Nighthawk R7800 with master build from @hnyman ) the resolution shown by dnsleaktest.com is done via Google servers.
After following the troubleshooting section of the guide I get these outputs from the commands:
root@OpenWrt:~# /etc/init.d/log restart; /etc/init.d/dnsmasq restart; /etc/init.d/stubby restart
udhcpc: started, v1.31.1
udhcpc: sending discover
udhcpc: no lease, failing
After doing this the one WoodyNet server also vanished from the dnsleak list.
Thu May 28 10:46:08 2020 daemon.info dnsmasq[2299]: exiting on receipt of SIGTERM
Thu May 28 10:46:08 2020 user.notice dnsmasq: DNS rebinding protection is active, will discard upstream RFC1918 responses!
Thu May 28 10:46:08 2020 user.notice dnsmasq: Allowing 127.0.0.0/8 responses
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: Connected to system UBus
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: started, version 2.81 cachesize 1000
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: DNS service limited to local subnets
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: compile time options: IPv6 GNU-getopt no-DBus UBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP no-conntrack no-ipset no-auth no-DNSSEC no-ID loop-detect inotify dumpfile
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: UBus support enabled: connected to system bus
Thu May 28 10:46:12 2020 daemon.info dnsmasq-dhcp[3646]: DHCP, IP range 192.168.2.100 -- 192.168.2.249, lease time 12h
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: using only locally-known addresses for domain test
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: using only locally-known addresses for domain onion
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: using only locally-known addresses for domain localhost
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: using only locally-known addresses for domain local
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: using only locally-known addresses for domain invalid
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: using only locally-known addresses for domain bind
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: using nameserver 127.0.0.1#5054
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: using nameserver 127.0.0.1#5053
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: using only locally-known addresses for domain openwrt.pool.ntp.org
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: using nameserver 10.10.10.254#53 for domain openwrt.pool.ntp.org
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: using nameserver ::1#5453
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: using nameserver 127.0.0.1#5453
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: using only locally-known addresses for domain lan
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: read /etc/hosts - 4 addresses
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: read /tmp/hosts/odhcpd - 1 addresses
Thu May 28 10:46:12 2020 daemon.info dnsmasq[3646]: read /tmp/hosts/dhcp.cfg01411c - 2 addresses
Thu May 28 10:46:12 2020 daemon.info dnsmasq-dhcp[3646]: read /etc/ethers - 0 addresses
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 3646/dnsmasq
tcp 0 0 192.168.2.1:53 0.0.0.0:* LISTEN 3646/dnsmasq
tcp 0 0 10.10.10.18:53 0.0.0.0:* LISTEN 3646/dnsmasq
tcp 0 0 ::1:53 :::* LISTEN 3646/dnsmasq
tcp 0 0 fe80::3e37:86ff:fe29:1909:53 :::* LISTEN 3646/dnsmasq
tcp 0 0 fe80::3e37:86ff:fe29:1908:53 :::* LISTEN 3646/dnsmasq
tcp 0 0 fd22:bdcd:a38d::1:53 :::* LISTEN 3646/dnsmasq
tcp 0 0 fe80::3e37:86ff:fe29:1908:53 :::* LISTEN 3646/dnsmasq
tcp 0 0 fe80::3e37:86ff:fe29:1909:53 :::* LISTEN 3646/dnsmasq
tcp 0 0 fe80::3e37:86ff:fe29:190a:53 :::* LISTEN 3646/dnsmasq
tcp 0 0 fe80::3e37:86ff:fe29:190b:53 :::* LISTEN 3646/dnsmasq
udp 0 0 127.0.0.1:53 0.0.0.0:* 3646/dnsmasq
udp 0 0 192.168.2.1:53 0.0.0.0:* 3646/dnsmasq
udp 0 0 10.10.10.18:53 0.0.0.0:* 3646/dnsmasq
udp 0 0 0.0.0.0:67 0.0.0.0:* 3646/dnsmasq
udp 0 0 ::1:53 :::* 3646/dnsmasq
udp 0 0 fe80::3e37:86ff:fe29:1909:53 :::* 3646/dnsmasq
udp 0 0 fe80::3e37:86ff:fe29:1908:53 :::* 3646/dnsmasq
udp 0 0 fd22:bdcd:a38d::1:53 :::* 3646/dnsmasq
udp 0 0 fe80::3e37:86ff:fe29:1908:53 :::* 3646/dnsmasq
udp 0 0 fe80::3e37:86ff:fe29:1909:53 :::* 3646/dnsmasq
udp 0 0 fe80::3e37:86ff:fe29:190a:53 :::* 3646/dnsmasq
udp 0 0 fe80::3e37:86ff:fe29:190b:53 :::* 3646/dnsmasq
Thu May 28 10:46:12 2020 daemon.err stubby[3701]: [08:46:12.404248] STUBBY: Read config from file /var/etc/stubby/stubby.yml
Thu May 28 10:46:12 2020 daemon.err stubby[3701]: [08:46:12.404744] STUBBY: DNSSEC Validation is OFF
Thu May 28 10:46:12 2020 daemon.err stubby[3701]: [08:46:12.404773] STUBBY: Transport list is:
Thu May 28 10:46:12 2020 daemon.err stubby[3701]: [08:46:12.404792] STUBBY: - TLS
Thu May 28 10:46:12 2020 daemon.err stubby[3701]: [08:46:12.404813] STUBBY: Privacy Usage Profile is Strict (Authentication required)
Thu May 28 10:46:12 2020 daemon.err stubby[3701]: [08:46:12.404834] STUBBY: (NOTE a Strict Profile only applies when TLS is the ONLY transport!!)
Thu May 28 10:46:12 2020 daemon.err stubby[3701]: [08:46:12.404855] STUBBY: Starting DAEMON....
tcp 0 0 127.0.0.1:5453 0.0.0.0:* LISTEN 3701/stubby
tcp 0 0 ::1:5453 :::* LISTEN 3701/stubby
udp 0 0 127.0.0.1:5453 0.0.0.0:* 3701/stubby
udp 0 0 ::1:5453 :::* 3701/stubby
root@OpenWrt:~# pgrep -f -a dnsmasq; pgrep -f -a stubby
3646 /usr/sbin/dnsmasq -C /var/etc/dnsmasq.conf.cfg01411c -k -x /var/run/dnsmasq/dnsmasq.cfg01411c.pid
3701 /usr/sbin/stubby -C /var/etc/stubby/stubby.yml
root@OpenWrt:~# uci show dhcp; uci show stubby
dhcp.@dnsmasq[0]=dnsmasq
dhcp.@dnsmasq[0].domainneeded='1'
dhcp.@dnsmasq[0].boguspriv='1'
dhcp.@dnsmasq[0].filterwin2k='0'
dhcp.@dnsmasq[0].localise_queries='1'
dhcp.@dnsmasq[0].rebind_protection='1'
dhcp.@dnsmasq[0].rebind_localhost='1'
dhcp.@dnsmasq[0].local='/lan/'
dhcp.@dnsmasq[0].domain='lan'
dhcp.@dnsmasq[0].expandhosts='1'
dhcp.@dnsmasq[0].nonegcache='0'
dhcp.@dnsmasq[0].cachesize='1000'
dhcp.@dnsmasq[0].authoritative='1'
dhcp.@dnsmasq[0].readethers='1'
dhcp.@dnsmasq[0].leasefile='/tmp/dhcp.leases'
dhcp.@dnsmasq[0].resolvfile='/tmp/resolv.conf.d/resolv.conf.auto'
dhcp.@dnsmasq[0].nonwildcard='1'
dhcp.@dnsmasq[0].localservice='1'
dhcp.@dnsmasq[0].noresolv='1'
dhcp.@dnsmasq[0].doh_backup_noresolv='-1'
dhcp.@dnsmasq[0].doh_backup_server='127.0.0.1#5053' '127.0.0.1#5054'
dhcp.@dnsmasq[0].server='127.0.0.1#5453' '0::1#5453' '/openwrt.pool.ntp.org/10.10.10.254' '/openwrt.pool.ntp.org/' '127.0.0.1#5053' '127.0.0.1#5054'
dhcp.@dnsmasq[0].localuse='1'
dhcp.lan=dhcp
dhcp.lan.interface='lan'
dhcp.lan.start='100'
dhcp.lan.limit='150'
dhcp.lan.leasetime='12h'
dhcp.lan.dhcpv6='server'
dhcp.lan.ra='server'
dhcp.lan.ra_slaac='1'
dhcp.lan.ra_flags='managed-config' 'other-config'
dhcp.wan=dhcp
dhcp.wan.interface='wan'
dhcp.wan.ignore='1'
dhcp.odhcpd=odhcpd
dhcp.odhcpd.maindhcp='0'
dhcp.odhcpd.leasefile='/tmp/hosts/odhcpd'
dhcp.odhcpd.leasetrigger='/usr/sbin/odhcpd-update'
dhcp.odhcpd.loglevel='4'
stubby.global=stubby
stubby.global.manual='0'
stubby.global.trigger='wan'
stubby.global.dns_transport='GETDNS_TRANSPORT_TLS'
stubby.global.tls_authentication='1'
stubby.global.tls_query_padding_blocksize='128'
stubby.global.appdata_dir='/var/lib/stubby'
stubby.global.edns_client_subnet_private='1'
stubby.global.idle_timeout='10000'
stubby.global.round_robin_upstreams='1'
stubby.global.listen_address='127.0.0.1@5453' '0::1@5453'
stubby.dns6a=resolver
stubby.dns6a.address='2620:fe::fe'
stubby.dns6a.tls_auth_name='dns.quad9.net'
stubby.dns6b=resolver
stubby.dns6b.address='2620:fe::9'
stubby.dns6b.tls_auth_name='dns.quad9.net'
stubby.dnsa=resolver
stubby.dnsa.address='9.9.9.9'
stubby.dnsa.tls_auth_name='dns.quad9.net'
stubby.dnsb=resolver
stubby.dnsb.address='149.112.112.112'
stubby.dnsb.tls_auth_name='dns.quad9.net'
As well as the content of my stubby.yml
# Note: by default on OpenWRT stubby configuration is handled via
# the UCI system and the file /etc/config/stubby. If you want to
# use this file to configure stubby, then set "option manual '1'"
# in /etc/config/stubby.
resolution_type: GETDNS_RESOLUTION_STUB
round_robin_upstreams: 1
appdata_dir: "/var/lib/stubby"
tls_authentication: GETDNS_AUTHENTICATION_REQUIRED
tls_query_padding_blocksize: 128
edns_client_subnet_private: 1
idle_timeout: 10000
listen_addresses:
- 127.0.0.1@5453
- 0::1@5453
dns_transport_list:
- GETDNS_TRANSPORT_TLS
upstream_recursive_servers:
- address_data: 2606:4700:4700::1111
tls_auth_name: "cloudflare-dns.com"
- address_data: 2606:4700:4700::1001
tls_auth_name: "cloudflare-dns.com"
- address_data: 1.1.1.1
tls_auth_name: "cloudflare-dns.com"
- address_data: 1.0.0.1
tls_auth_name: "cloudflare-dns.com"
In which you see that the Cloudflare servers are set instead of the specified Quad9 servers as can be seen in the output of
uci show dhcp; uci show stubby
just one box above it.
Could one of you shed some light on this?
EDIT: After executing this part again
uci -q delete dhcp.@dnsmasq[0].server
uci get stubby.global.listen_address \
| sed -e "s/\s/\n/g;s/@/#/g" \
| while read -r STUBBY_SERV
do
uci add_list dhcp.@dnsmasq[0].server="${STUBBY_SERV}"
done
the WoodyNet server are again the only ones used. After a reboot the Google servers are used again. The stubby.yml was unchanged and still pointing to Cloudflare, which adds to my confusion.