(edit) just re-read and realise you are trying this directly from OpenWrt. You are correct. As it uses a separate upstream it will not know about dnsmasq.
Easiest option here is to edit /etc/hosts and insert your entry in there.
192.168.1.3 apesc
(edit - this fixes for downstream clients not for the router itself)
Two ways to solve this for downstream clients.
https://openwrt.org/docs/guide-user/services/dns/adguard-home#lan_domain_interception follow this and add in to your upstream. This will intercept any local lookup request and pass it to dnsmasq.
The other way is a DNS Re-Write.
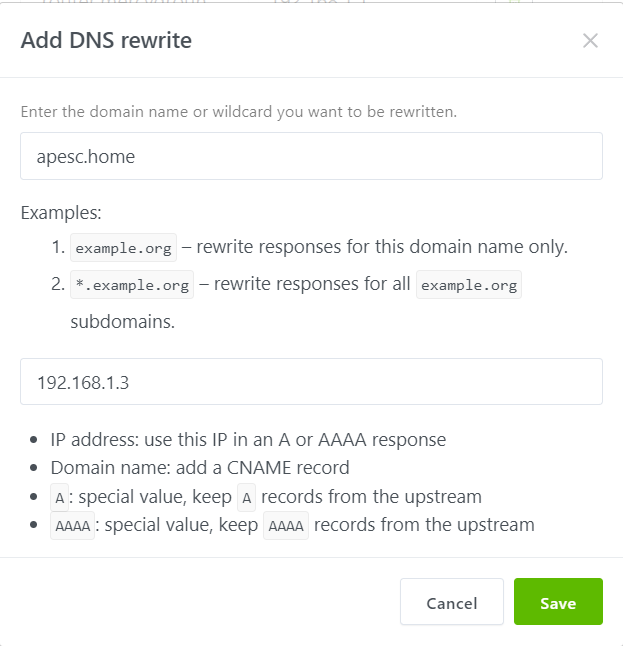
On the AGH web interface go to Filters > DNS Re-write.
Click Add
Fill in like this and any requests for that address will reply 192.168.1.3