i know that, after the hack, but i'm really mad with this devices, i'm try that to get root access for a different device.
hope i can get the wireless source or something nice
Try this firmware that i have.
to access the web login you need to
Static your IP address to 10.0.31.1 and subnet mask to 255.255.224.0
the password of this is pogs1233
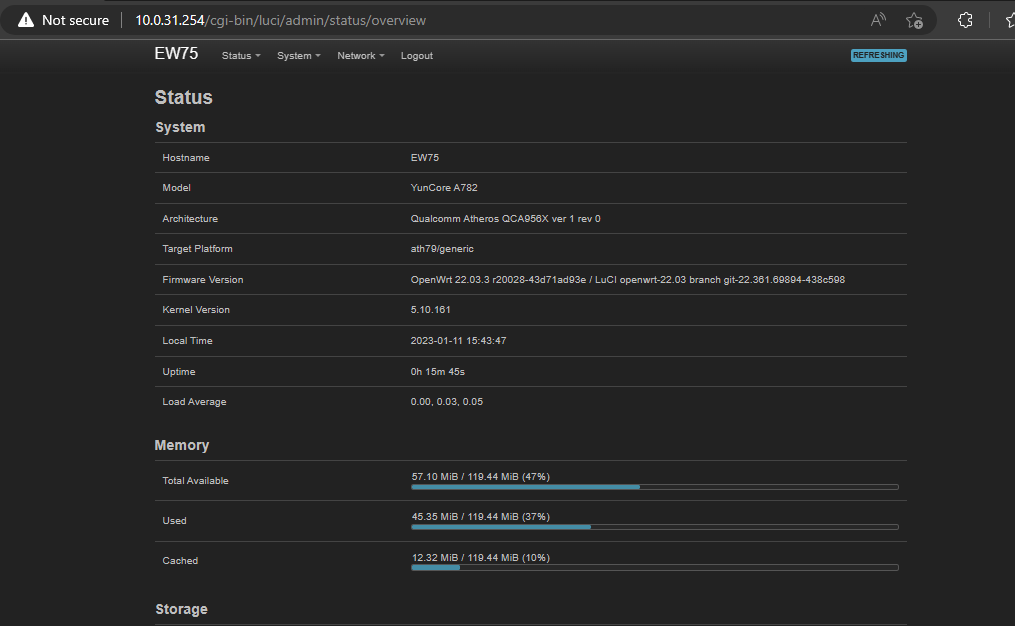
I was able to boot up my new EW75 with the recent OpenWRT version that I have used before. and this is the SYSTEM LOG:
Wed Jan 11 15:25:29 2023 daemon.notice procd: /etc/rc.d/S96led: setting up led 2Ghz
Wed Jan 11 15:25:29 2023 daemon.notice procd: /etc/rc.d/S96led: setting up led 5Ghz
Wed Jan 11 15:25:29 2023 daemon.notice procd: /etc/rc.d/S96led: setting up led 1
Wed Jan 11 15:25:29 2023 daemon.notice procd: /etc/rc.d/S96led: setting up led 2
Wed Jan 11 15:25:30 2023 kern.info kernel: [ 80.648781] br-lan: port 1(eth0) entered blocking state
Wed Jan 11 15:25:30 2023 kern.info kernel: [ 80.654190] br-lan: port 1(eth0) entered disabled state
Wed Jan 11 15:25:30 2023 kern.info kernel: [ 80.659913] device eth0 entered promiscuous mode
Wed Jan 11 15:25:30 2023 daemon.notice netifd: Interface 'lan' is enabled
Wed Jan 11 15:25:30 2023 daemon.notice netifd: Interface 'lan' is setting up now
Wed Jan 11 15:25:30 2023 daemon.notice netifd: Interface 'lan' is now up
Wed Jan 11 15:25:30 2023 daemon.notice netifd: Interface 'loopback' is enabled
Wed Jan 11 15:25:30 2023 daemon.notice netifd: Interface 'loopback' is setting up now
Wed Jan 11 15:25:30 2023 daemon.notice netifd: Interface 'loopback' is now up
Wed Jan 11 15:25:30 2023 daemon.info procd: - init complete -
Wed Jan 11 15:25:30 2023 daemon.notice netifd: Network device 'lo' link is up
Wed Jan 11 15:25:30 2023 daemon.notice netifd: Interface 'loopback' has link connectivity
Wed Jan 11 15:25:31 2023 daemon.info urandom_seed[2210]: Seed saved (/etc/urandom.seed)
Wed Jan 11 15:25:32 2023 kern.info kernel: [ 82.739893] eth0: link up (100Mbps/Full duplex)
Wed Jan 11 15:25:32 2023 kern.info kernel: [ 82.744618] br-lan: port 1(eth0) entered blocking state
Wed Jan 11 15:25:32 2023 kern.info kernel: [ 82.750060] br-lan: port 1(eth0) entered forwarding state
Wed Jan 11 15:25:32 2023 daemon.notice netifd: Network device 'eth0' link is up
Wed Jan 11 15:25:32 2023 daemon.notice netifd: bridge 'br-lan' link is up
Wed Jan 11 15:25:32 2023 daemon.notice netifd: Interface 'lan' has link connectivity
Wed Jan 11 15:25:34 2023 daemon.notice hostapd: Configuration file: /var/run/hostapd-phy1.conf (phy 2Ghz) --> new PHY
Wed Jan 11 15:25:34 2023 kern.info kernel: [ 84.582112] br-lan: port 2(2Ghz) entered blocking state
Wed Jan 11 15:25:34 2023 kern.info kernel: [ 84.587522] br-lan: port 2(2Ghz) entered disabled state
Wed Jan 11 15:25:34 2023 kern.info kernel: [ 84.593256] device 2Ghz entered promiscuous mode
Wed Jan 11 15:25:34 2023 daemon.notice hostapd: 2Ghz: interface state UNINITIALIZED->COUNTRY_UPDATE
Wed Jan 11 15:25:34 2023 kern.info kernel: [ 84.747933] IPv6: ADDRCONF(NETDEV_CHANGE): 2Ghz: link becomes ready
Wed Jan 11 15:25:34 2023 kern.info kernel: [ 84.754640] br-lan: port 2(2Ghz) entered blocking state
Wed Jan 11 15:25:34 2023 kern.info kernel: [ 84.760087] br-lan: port 2(2Ghz) entered forwarding state
Wed Jan 11 15:25:34 2023 daemon.notice hostapd: 2Ghz: interface state COUNTRY_UPDATE->ENABLED
Wed Jan 11 15:25:34 2023 daemon.notice hostapd: 2Ghz: AP-ENABLED
Wed Jan 11 15:25:34 2023 daemon.notice hostapd: Configuration file: /var/run/hostapd-phy0.conf (phy 5Ghz) --> new PHY
Wed Jan 11 15:25:36 2023 daemon.notice netifd: Wireless device 'radio1' is now up
Wed Jan 11 15:25:37 2023 kern.warn kernel: [ 87.385972] ath10k_pci 0000:00:00.0: 10.4 wmi init: vdevs: 16 peers: 48 tid: 96
Wed Jan 11 15:25:37 2023 kern.warn kernel: [ 87.393780] ath10k_pci 0000:00:00.0: msdu-desc: 2500 skid: 32
Wed Jan 11 15:25:37 2023 kern.info kernel: [ 87.445386] ath10k_pci 0000:00:00.0: wmi print 'P 48/48 V 16 K 144 PH 176 T 186 msdu-desc: 2500 sw-crypt: 0 ct-sta: 0'
Wed Jan 11 15:25:37 2023 kern.info kernel: [ 87.456735] ath10k_pci 0000:00:00.0: wmi print 'free: 114572 iram: 12644 sram: 29508'
Wed Jan 11 15:25:37 2023 kern.info kernel: [ 87.775345] ath10k_pci 0000:00:00.0: rts threshold -1
Wed Jan 11 15:25:37 2023 kern.warn kernel: [ 87.780919] ath10k_pci 0000:00:00.0: Firmware lacks feature flag indicating a retry limit of > 2 is OK, requested limit: 4
Wed Jan 11 15:25:37 2023 daemon.notice netifd: Network device '2Ghz' link is up
Wed Jan 11 15:25:37 2023 kern.info kernel: [ 87.807483] br-lan: port 3(5Ghz) entered blocking state
Wed Jan 11 15:25:37 2023 kern.info kernel: [ 87.813006] br-lan: port 3(5Ghz) entered disabled state
Wed Jan 11 15:25:37 2023 kern.info kernel: [ 87.819038] device 5Ghz entered promiscuous mode
Wed Jan 11 15:25:37 2023 daemon.notice hostapd: 5Ghz: interface state UNINITIALIZED->COUNTRY_UPDATE
Wed Jan 11 15:25:37 2023 daemon.notice hostapd: 5Ghz: interface state COUNTRY_UPDATE->HT_SCAN
Wed Jan 11 15:25:38 2023 kern.info kernel: [ 88.373170] IPv6: ADDRCONF(NETDEV_CHANGE): 5Ghz: link becomes ready
Wed Jan 11 15:25:38 2023 kern.info kernel: [ 88.379924] br-lan: port 3(5Ghz) entered blocking state
Wed Jan 11 15:25:38 2023 kern.info kernel: [ 88.385350] br-lan: port 3(5Ghz) entered forwarding state
Wed Jan 11 15:25:38 2023 kern.info kernel: [ 88.391093] ath10k_pci 0000:00:00.0: NOTE: Firmware DBGLOG output disabled in debug_mask: 0x10000000
Wed Jan 11 15:25:38 2023 daemon.notice hostapd: 5Ghz: interface state HT_SCAN->ENABLED
Wed Jan 11 15:25:38 2023 daemon.notice hostapd: 5Ghz: AP-ENABLED
Wed Jan 11 15:25:38 2023 daemon.notice netifd: Wireless device 'radio0' is now up
Wed Jan 11 15:25:38 2023 daemon.notice netifd: Network device '5Ghz' link is up
Wed Jan 11 15:25:48 2023 user.info : luci: failed login on / for root from 10.0.31.1
Wed Jan 11 15:25:51 2023 user.info : luci: accepted login on / for root from 10.0.31.1
Full System Log Link: EW75 System Log
KERNEL LOG
[ 54.897177] ath10k 5.15 driver, optimized for CT firmware, probing pci device: 0x56.
[ 54.906945] ath10k_pci 0000:00:00.0: enabling device (0000 -> 0002)
[ 54.913738] ath10k_pci 0000:00:00.0: pci irq legacy oper_irq_mode 1 irq_mode 0 reset_mode 0
[ 57.769111] ath10k_pci 0000:00:00.0: qca9888 hw2.0 target 0x01000000 chip_id 0x00000000 sub 0000:0000
[ 57.778668] ath10k_pci 0000:00:00.0: kconfig debug 0 debugfs 1 tracing 0 dfs 1 testmode 0
[ 57.797842] ath10k_pci 0000:00:00.0: firmware ver 10.4b-ct-9888-fW-13-5ae337bb1 api 5 features mfp,peer-flow-ctrl,txstatus-noack,wmi-10.x-CT,ratemask-CT,regdump-CT,txrate-CT,flush-all-CT,pingpong-CT,ch-regs-CT,nop-CT,set-special-CT,tx-rc-CT,cust-stats-CT,txrate2-CT,beacon-cb-CT,wmi-block-ack-CT,wmi-bcn-rc-CT crc32 59e741e7
[ 58.131145] ath10k_pci 0000:00:00.0: Loading BDF type 0
[ 58.141877] ath10k_pci 0000:00:00.0: board_file api 2 bmi_id 0:16 crc32 f228337a
[ 59.903364] ath10k_pci 0000:00:00.0: 10.4 wmi init: vdevs: 16 peers: 48 tid: 96
[ 59.911151] ath10k_pci 0000:00:00.0: msdu-desc: 2500 skid: 32
[ 59.962489] ath10k_pci 0000:00:00.0: wmi print 'P 48/48 V 16 K 144 PH 176 T 186 msdu-desc: 2500 sw-crypt: 0 ct-sta: 0'
[ 59.973807] ath10k_pci 0000:00:00.0: wmi print 'free: 114572 iram: 12644 sram: 29508'
[ 60.212997] ath10k_pci 0000:00:00.0: htt-ver 2.2 wmi-op 6 htt-op 4 cal pre-cal-file max-sta 32 raw 0 hwcrypto 1
[ 60.321471] ath: EEPROM regdomain: 0x0
[ 60.321482] ath: EEPROM indicates default country code should be used
[ 60.321486] ath: doing EEPROM country->regdmn map search
[ 60.321499] ath: country maps to regdmn code: 0x3a
[ 60.321505] ath: Country alpha2 being used: US
[ 60.321509] ath: Regpair used: 0x3a
[ 60.424970] ath: EEPROM regdomain: 0x0
[ 60.424983] ath: EEPROM indicates default country code should be used
[ 60.424988] ath: doing EEPROM country->regdmn map search
[ 60.425002] ath: country maps to regdmn code: 0x3a
[ 60.425008] ath: Country alpha2 being used: US
[ 60.425012] ath: Regpair used: 0x3a
[ 60.435839] ieee80211 phy1: Selected rate control algorithm 'minstrel_ht'
[ 60.437693] ieee80211 phy1: Atheros AR9561 Rev:0 mem=0xb8100000, irq=2
[ 60.478692] kmodloader: done loading kernel modules from /etc/modules.d/*
[ 80.648781] br-lan: port 1(eth0) entered blocking state
[ 80.654190] br-lan: port 1(eth0) entered disabled state
[ 80.659913] device eth0 entered promiscuous mode
[ 82.739893] eth0: link up (100Mbps/Full duplex)
[ 82.744618] br-lan: port 1(eth0) entered blocking state
[ 82.750060] br-lan: port 1(eth0) entered forwarding state
[ 84.582112] br-lan: port 2(2Ghz) entered blocking state
[ 84.587522] br-lan: port 2(2Ghz) entered disabled state
[ 84.593256] device 2Ghz entered promiscuous mode
[ 84.747933] IPv6: ADDRCONF(NETDEV_CHANGE): 2Ghz: link becomes ready
[ 84.754640] br-lan: port 2(2Ghz) entered blocking state
[ 84.760087] br-lan: port 2(2Ghz) entered forwarding state
[ 87.385972] ath10k_pci 0000:00:00.0: 10.4 wmi init: vdevs: 16 peers: 48 tid: 96
[ 87.393780] ath10k_pci 0000:00:00.0: msdu-desc: 2500 skid: 32
[ 87.445386] ath10k_pci 0000:00:00.0: wmi print 'P 48/48 V 16 K 144 PH 176 T 186 msdu-desc: 2500 sw-crypt: 0 ct-sta: 0'
[ 87.456735] ath10k_pci 0000:00:00.0: wmi print 'free: 114572 iram: 12644 sram: 29508'
[ 87.775345] ath10k_pci 0000:00:00.0: rts threshold -1
[ 87.780919] ath10k_pci 0000:00:00.0: Firmware lacks feature flag indicating a retry limit of > 2 is OK, requested limit: 4
[ 87.807483] br-lan: port 3(5Ghz) entered blocking state
[ 87.813006] br-lan: port 3(5Ghz) entered disabled state
[ 87.819038] device 5Ghz entered promiscuous mode
[ 88.373170] IPv6: ADDRCONF(NETDEV_CHANGE): 5Ghz: link becomes ready
[ 88.379924] br-lan: port 3(5Ghz) entered blocking state
[ 88.385350] br-lan: port 3(5Ghz) entered forwarding state
[ 88.391093] ath10k_pci 0000:00:00.0: NOTE: Firmware DBGLOG output disabled in debug_mask: 0x10000000
Full Kernel Log : EW75 Kernel Log
in my observation, you cannot install the new version 22.03.3 directly. you need to install the firmware that I have configured so that it will boot up.
to access the web interface you need to change your IP and subnet mask to
IP: 10.0.31.1
SUBNET: 255.255.224.0
web: 10.0.31.254
Password: pogs1233
please let me know your thoughts about this @dsouza
And please add this device @pepe2k , @hauke . God Bless you devs.
Thank you @reydeyes!
Would you please share your .config file you used for this build as well as any other change you've made?
This would facilitate others (such myself) to do our own builds, as well as will provide more information to devs so they can add official support to this device.
Thank you.
Well, I believe I just destroyed my CF-EW75. I tried to connect it to a POE 802.3af source, and it did not work. Now when I connect it to the supplied POE power brick, it does not turn on anymore.
This unit was so bad with stock firmware that I was not using it. Now then I can literally throw it away.