Yes but now my device is bricked and i don't know how to bring in Life!
I actually ended up bricking mine because i messet up with flashing the Chinese QSDK before couple of month and now because i tried flashing the stock firmware with MiRepairTool. The router bootlooped!
I had a similar issue. You probably need serial access to unbrick your device:
I managed to exchange my router for a new one at my local store before my USB to TTL arrived from aliexpress, so can't confirm that the instructions above work.
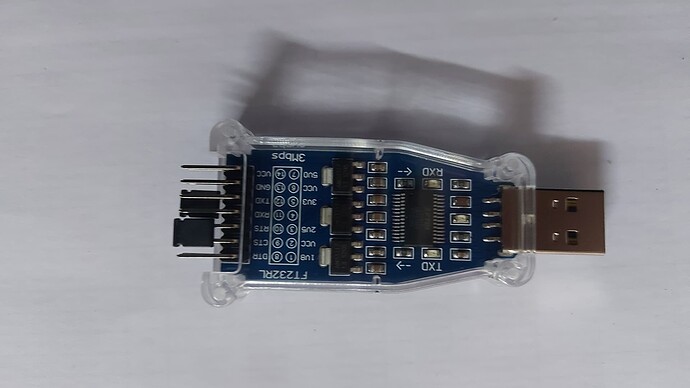
Definitly i'll try to unbrick with uart
I bought this one from AliExpress: https://a.aliexpress.com/_mNJCv7o
Any body know if is the right one?
It will work, just make sure to set it to 1.8V mode
ARMv8 Crypto extensions really boost performance in WolfSSL:
------------------------------------------------------------- -------------------------------------------------------------
wolfSSL version 5.2.0 wolfSSL version 5.2.0
------------------------------------------------------------- -------------------------------------------------------------
wolfCrypt Benchmark (block bytes 1048576, min 1.0 sec each) wolfCrypt Benchmark (block bytes 1048576, min 1.0 sec each)
RNG 35 MB took 1.044 seconds, 33.523 MB/s | RNG 145 MB took 1.027 seconds, 141.200 MB/s
AES-128-CBC-enc 50 MB took 1.027 seconds, 48.675 MB/s | AES-128-CBC-enc 1140 MB took 1.004 seconds, 1135.490 MB/s
AES-128-CBC-dec 45 MB took 1.001 seconds, 44.962 MB/s | AES-128-CBC-dec 1035 MB took 1.003 seconds, 1032.316 MB/s
AES-192-CBC-enc 45 MB took 1.061 seconds, 42.410 MB/s | AES-192-CBC-enc 1000 MB took 1.001 seconds, 999.101 MB/s
AES-192-CBC-dec 40 MB took 1.026 seconds, 38.980 MB/s | AES-192-CBC-dec 955 MB took 1.001 seconds, 953.767 MB/s
AES-256-CBC-enc 40 MB took 1.063 seconds, 37.639 MB/s | AES-256-CBC-enc 910 MB took 1.001 seconds, 908.998 MB/s
AES-256-CBC-dec 35 MB took 1.018 seconds, 34.375 MB/s | AES-256-CBC-dec 890 MB took 1.002 seconds, 888.048 MB/s
AES-128-GCM-enc 30 MB took 1.035 seconds, 28.982 MB/s | AES-128-GCM-enc 720 MB took 1.002 seconds, 718.455 MB/s
AES-128-GCM-dec 30 MB took 1.036 seconds, 28.965 MB/s | AES-128-GCM-dec 330 MB took 1.006 seconds, 328.029 MB/s
AES-192-GCM-enc 30 MB took 1.126 seconds, 26.635 MB/s | AES-192-GCM-enc 665 MB took 1.005 seconds, 661.811 MB/s
AES-192-GCM-dec 30 MB took 1.127 seconds, 26.625 MB/s | AES-192-GCM-dec 320 MB took 1.009 seconds, 317.046 MB/s
AES-256-GCM-enc 25 MB took 1.014 seconds, 24.662 MB/s | AES-256-GCM-enc 615 MB took 1.008 seconds, 610.381 MB/s
AES-256-GCM-dec 25 MB took 1.014 seconds, 24.663 MB/s | AES-256-GCM-dec 305 MB took 1.005 seconds, 303.620 MB/s
GMAC Table 4-bit 74 MB took 1.010 seconds, 73.269 MB/s | GMAC Table 4-bit 532 MB took 1.001 seconds, 531.485 MB/s
AES-128-ECB-enc 49 MB took 1.000 seconds, 49.057 MB/s | AES-128-ECB-enc 345 MB took 1.000 seconds, 345.338 MB/s
AES-128-ECB-dec 46 MB took 1.000 seconds, 45.624 MB/s | AES-128-ECB-dec 354 MB took 1.000 seconds, 353.674 MB/s
AES-192-ECB-enc 43 MB took 1.000 seconds, 42.701 MB/s | AES-192-ECB-enc 312 MB took 1.000 seconds, 312.082 MB/s
AES-192-ECB-dec 39 MB took 1.000 seconds, 39.472 MB/s | AES-192-ECB-dec 320 MB took 1.000 seconds, 319.875 MB/s
AES-256-ECB-enc 38 MB took 1.000 seconds, 37.866 MB/s | AES-256-ECB-enc 288 MB took 1.000 seconds, 288.056 MB/s
AES-256-ECB-dec 35 MB took 1.000 seconds, 34.749 MB/s | AES-256-ECB-dec 295 MB took 1.000 seconds, 295.023 MB/s
AES-128-CTR 50 MB took 1.050 seconds, 47.638 MB/s | AES-128-CTR 1340 MB took 1.000 seconds, 1339.989 MB/s
AES-192-CTR 45 MB took 1.081 seconds, 41.628 MB/s | AES-192-CTR 1255 MB took 1.002 seconds, 1252.179 MB/s
AES-256-CTR 40 MB took 1.081 seconds, 37.011 MB/s | AES-256-CTR 1180 MB took 1.003 seconds, 1176.377 MB/s
AES-CCM-Enc 25 MB took 1.031 seconds, 24.244 MB/s | AES-CCM-Enc 170 MB took 1.013 seconds, 167.869 MB/s
AES-CCM-Dec 25 MB took 1.031 seconds, 24.251 MB/s | AES-CCM-Dec 170 MB took 1.023 seconds, 166.113 MB/s
ARC4 110 MB took 1.024 seconds, 107.438 MB/s | ARC4 110 MB took 1.024 seconds, 107.396 MB/s
CHACHA 125 MB took 1.007 seconds, 124.147 MB/s | CHACHA 460 MB took 1.005 seconds, 457.676 MB/s
CHA-POLY 95 MB took 1.036 seconds, 91.682 MB/s | CHA-POLY 315 MB took 1.006 seconds, 313.103 MB/s
3DES 10 MB took 1.133 seconds, 8.829 MB/s | 3DES 10 MB took 1.184 seconds, 8.443 MB/s
MD5 220 MB took 1.013 seconds, 217.280 MB/s | MD5 220 MB took 1.011 seconds, 217.520 MB/s
POLY1305 390 MB took 1.013 seconds, 385.176 MB/s | POLY1305 965 MB took 1.002 seconds, 962.991 MB/s
SHA 190 MB took 1.001 seconds, 189.800 MB/s | SHA 185 MB took 1.006 seconds, 183.886 MB/s
SHA-224 85 MB took 1.056 seconds, 80.496 MB/s | SHA-224 955 MB took 1.002 seconds, 952.805 MB/s
SHA-256 85 MB took 1.057 seconds, 80.440 MB/s | SHA-256 955 MB took 1.004 seconds, 950.722 MB/s
SHA-384 135 MB took 1.014 seconds, 133.160 MB/s | SHA-384 230 MB took 1.011 seconds, 227.579 MB/s
SHA-512 135 MB took 1.016 seconds, 132.923 MB/s | SHA-512 230 MB took 1.011 seconds, 227.543 MB/s
SHA3-224 135 MB took 1.029 seconds, 131.210 MB/s | SHA3-224 115 MB took 1.015 seconds, 113.259 MB/s
SHA3-256 125 MB took 1.004 seconds, 124.492 MB/s | SHA3-256 110 MB took 1.016 seconds, 108.256 MB/s
SHA3-384 100 MB took 1.032 seconds, 96.881 MB/s | SHA3-384 90 MB took 1.037 seconds, 86.778 MB/s
SHA3-512 70 MB took 1.025 seconds, 68.296 MB/s | SHA3-512 65 MB took 1.029 seconds, 63.139 MB/s
AES-128-CMAC 50 MB took 1.057 seconds, 47.308 MB/s | AES-128-CMAC 275 MB took 1.018 seconds, 270.261 MB/s
AES-256-CMAC 40 MB took 1.087 seconds, 36.804 MB/s | AES-256-CMAC 235 MB took 1.003 seconds, 234.284 MB/s
HMAC-MD5 225 MB took 1.022 seconds, 220.170 MB/s | HMAC-MD5 220 MB took 1.012 seconds, 217.368 MB/s
HMAC-SHA 195 MB took 1.018 seconds, 191.631 MB/s | HMAC-SHA 185 MB took 1.006 seconds, 183.835 MB/s
HMAC-SHA224 85 MB took 1.054 seconds, 80.642 MB/s | HMAC-SHA224 950 MB took 1.001 seconds, 949.352 MB/s
HMAC-SHA256 85 MB took 1.055 seconds, 80.534 MB/s | HMAC-SHA256 950 MB took 1.000 seconds, 949.798 MB/s
HMAC-SHA384 135 MB took 1.011 seconds, 133.526 MB/s | HMAC-SHA384 230 MB took 1.011 seconds, 227.532 MB/s
HMAC-SHA512 135 MB took 1.011 seconds, 133.572 MB/s | HMAC-SHA512 230 MB took 1.011 seconds, 227.492 MB/s
PBKDF2 9 KB took 1.000 seconds, 9.374 KB/s | PBKDF2 48 KB took 1.000 seconds, 48.094 KB/s
RSA 1024 key gen 4 ops took 1.325 sec, avg 331.20 | RSA 1024 key gen 3 ops took 1.051 sec, avg 350.35
RSA 2048 key gen 1 ops took 5.627 sec, avg 5626.7 | RSA 2048 key gen 1 ops took 3.597 sec, avg 3597.4
RSA 2048 public 1100 ops took 1.034 sec, avg 0.940 | RSA 2048 public 1100 ops took 1.030 sec, avg 0.936
RSA 2048 private 100 ops took 5.671 sec, avg 56.705 | RSA 2048 private 100 ops took 5.676 sec, avg 56.760
DH 2048 key gen 93 ops took 1.002 sec, avg 10.778 | DH 2048 key gen 93 ops took 1.003 sec, avg 10.783
DH 2048 agree 100 ops took 2.335 sec, avg 23.348 | DH 2048 agree 100 ops took 2.335 sec, avg 23.351
ECC [ SECP256R1] 256 key gen 191 ops took 1.00 | ECC [ SECP256R1] 256 key gen 191 ops took 1.00
ECDHE [ SECP256R1] 256 agree 200 ops took 1.05 | ECDHE [ SECP256R1] 256 agree 200 ops took 1.05
ECDSA [ SECP256R1] 256 sign 200 ops took 1.07 | ECDSA [ SECP256R1] 256 sign 200 ops took 1.07
ECDSA [ SECP256R1] 256 verify 300 ops took 1.10 | ECDSA [ SECP256R1] 256 verify 300 ops took 1.10
CURVE 25519 key gen 3340 ops took 1.000 sec, avg 0.299 | CURVE 25519 key gen 4818 ops took 1.000 sec, avg 0.208
CURVE 25519 agree 3400 ops took 1.018 sec, avg 0.299 | CURVE 25519 agree 4900 ops took 1.020 sec, avg 0.208
Benchmark complete Benchmark complete
Hi, I'm using mwan3, but on "Status" tab, it shows 2 firewall rows: [Firewall (iptables)] [Firewall (iptables)]. will this cause any problem? thanks
I assume its just a LuCI bug, shouldn't really break anything.
I just figured out that we need to enable ARM CE algos in the kernel as well, no idea why I did not do that before.
Has mwan3 been updated to support nftables yet?
well, I'm not sure.
from here https://github.com/openwrt/packages/issues/16818, it's compatible with firewall4.
but from mwan3 makefile (master branch)
the load balancing function works on your build, I just worry if there is problem.
Can for example Wireguard benefit from this?
Unfortunately not as It uses ChaCha20 and Poly1305 which are not covered by the crypto extensions, only speedup is the NEON optimized version of those which I think is already used.
Those djb crypto algorithms are usually heavily neon optimised, so should already be much better than aes without crypto extensions.
So right numbers come from the tests without ARMv8 CE and the left numbers are from the tests with ARMv8 CE?
Actually, I tested CE with the mbedtls patch [1] instead of wolfssl for the SoC IPQ8074a before. If your
left numbers are from the tests with ARMv8 CE, I would say the patch may need to be optimized.
root@OpenWrt:/# ./benchmark aes_gcm
AES-GCM-128 : 52231 KiB/s, 0 cycles/byte
AES-GCM-192 : 71991 KiB/s, 0 cycles/byte
AES-GCM-256 : 73332 KiB/s, 0 cycles/byte
BTW, have you gotten the numbers in the kernel space?
[1]https://github.com/coolsnowwolf/lede/commit/ef449e470b4eb46cff376efefe35b4c05251d3b1
Edit:
Oh, sorry, typo.
So right numbers come from the tests without ARMv8 CE and the left numbers are from the tests with ARMv8 CE?
should be
So left numbers come from the tests without ARMv8 CE and the right numbers are from the tests with ARMv8 CE?
@robimarko Oh, I just figured out maybe performance difference is caused by the block size. In my test, the block size 1KB while it's 1MB in your test. Would you mind to test 1KB/1500B which is used widely in real world?
Right size is with crypto extensions obviously, you can see huge speedup.
Benchmark tool is packaged so it can be used to test other block sizes, I just wanted to see whether it works
Did you test with https://github.com/wolfSSL/wolfssl/blob/master/wolfcrypt/benchmark/benchmark.c?
Sorry, I can not test it now. I will try later. If using this tool, there is a option "<num".
static const char* bench_Usage_msg1[][18] = {
/* 0 English */
{ "-? <num> Help, print this usage\n 0: English, 1: Japanese\n",
"-csv Print terminal output in csv format\n",
"-base10 Display bytes as power of 10 (eg 1 kB = 1000 Bytes)\n",
"-no_aad No additional authentication data passed.\n",
"-dgst_full Full digest operation performed.\n",
"-rsa_sign Measure RSA sign/verify instead of encrypt/decrypt.\n",
"<keySz> -rsa-sz\n Measure RSA <key size> performance.\n",
"-ffhdhe2048 Measure DH using FFDHE 2048-bit parameters.\n",
"-ffhdhe3072 Measure DH using FFDHE 3072-bit parameters.\n",
"-p256 Measure ECC using P-256 curve.\n",
"-p384 Measure ECC using P-384 curve.\n",
"-p521 Measure ECC using P-521 curve.\n",
"-ecc-all Bench all enabled ECC curves.\n",
"-<alg> Algorithm to benchmark. Available algorithms include:\n",
"-lng <num> Display benchmark result by specified language.\n 0: English, 1: Japanese\n",
"<num> Size of block in bytes\n",
"-threads <num> Number of threads to run\n",
"-print Show benchmark stats summary\n"
},
Here is with 1k and CE:
------------------------------------------------------------------------------
wolfSSL version 5.2.0
------------------------------------------------------------------------------
wolfCrypt Benchmark (block bytes 1024, min 1.0 sec each)
RNG 130 MB took 1.020 seconds, 127.415 MB/s
AES-128-CBC-enc 1240 MB took 1.002 seconds, 1237.468 MB/s
AES-128-CBC-dec 1160 MB took 1.004 seconds, 1155.297 MB/s
AES-192-CBC-enc 1080 MB took 1.004 seconds, 1075.795 MB/s
AES-192-CBC-dec 1045 MB took 1.003 seconds, 1042.300 MB/s
AES-256-CBC-enc 955 MB took 1.003 seconds, 951.845 MB/s
AES-256-CBC-dec 930 MB took 1.005 seconds, 925.652 MB/s
AES-128-GCM-enc 665 MB took 1.001 seconds, 664.050 MB/s
AES-128-GCM-dec 320 MB took 1.011 seconds, 316.418 MB/s
AES-192-GCM-enc 615 MB took 1.007 seconds, 610.471 MB/s
AES-192-GCM-dec 305 MB took 1.003 seconds, 304.165 MB/s
AES-256-GCM-enc 570 MB took 1.005 seconds, 567.241 MB/s
AES-256-GCM-dec 295 MB took 1.007 seconds, 293.081 MB/s
GMAC Table 4-bit 491 MB took 1.000 seconds, 491.346 MB/s
AES-128-ECB-enc 534 MB took 1.000 seconds, 533.725 MB/s
AES-128-ECB-dec 552 MB took 1.000 seconds, 551.778 MB/s
AES-192-ECB-enc 456 MB took 1.000 seconds, 455.481 MB/s
AES-192-ECB-dec 474 MB took 1.000 seconds, 474.105 MB/s
AES-256-ECB-enc 406 MB took 1.000 seconds, 406.052 MB/s
AES-256-ECB-dec 421 MB took 1.000 seconds, 420.781 MB/s
AES-128-CTR 1470 MB took 1.001 seconds, 1468.571 MB/s
AES-192-CTR 1345 MB took 1.000 seconds, 1344.816 MB/s
AES-256-CTR 1240 MB took 1.000 seconds, 1239.632 MB/s
AES-CCM-Enc 165 MB took 1.003 seconds, 164.506 MB/s
AES-CCM-Dec 160 MB took 1.003 seconds, 159.462 MB/s
ARC4 115 MB took 1.040 seconds, 110.546 MB/s
CHACHA 475 MB took 1.011 seconds, 470.051 MB/s
CHA-POLY 240 MB took 1.009 seconds, 237.844 MB/s
3DES 10 MB took 1.181 seconds, 8.466 MB/s
MD5 220 MB took 1.000 seconds, 219.953 MB/s
POLY1305 955 MB took 1.005 seconds, 950.582 MB/s
SHA 190 MB took 1.022 seconds, 185.838 MB/s
SHA-224 980 MB took 1.002 seconds, 978.159 MB/s
SHA-256 980 MB took 1.002 seconds, 978.174 MB/s
SHA-384 230 MB took 1.009 seconds, 227.947 MB/s
SHA-512 230 MB took 1.009 seconds, 227.977 MB/s
SHA3-224 115 MB took 1.034 seconds, 111.251 MB/s
SHA3-256 110 MB took 1.034 seconds, 106.369 MB/s
SHA3-384 90 MB took 1.047 seconds, 85.929 MB/s
SHA3-512 65 MB took 1.034 seconds, 62.886 MB/s
AES-128-CMAC 275 MB took 1.009 seconds, 272.622 MB/s
AES-256-CMAC 240 MB took 1.016 seconds, 236.206 MB/s
HMAC-MD5 220 MB took 1.003 seconds, 219.281 MB/s
HMAC-SHA 190 MB took 1.025 seconds, 185.361 MB/s
HMAC-SHA224 970 MB took 1.004 seconds, 966.277 MB/s
HMAC-SHA256 970 MB took 1.003 seconds, 966.667 MB/s
HMAC-SHA384 230 MB took 1.013 seconds, 227.147 MB/s
HMAC-SHA512 230 MB took 1.013 seconds, 227.128 MB/s
PBKDF2 48 KB took 1.001 seconds, 48.098 KB/s
RSA 1024 key gen 5 ops took 1.079 sec, avg 215.718 ms, 4.636 ops/sec
RSA 2048 key gen 1 ops took 2.472 sec, avg 2471.937 ms, 0.405 ops/sec
RSA 2048 public 1100 ops took 1.030 sec, avg 0.936 ms, 1068.126 ops/sec
RSA 2048 private 100 ops took 5.676 sec, avg 56.762 ms, 17.617 ops/sec
DH 2048 key gen 93 ops took 1.003 sec, avg 10.783 ms, 92.736 ops/sec
DH 2048 agree 100 ops took 2.335 sec, avg 23.355 ms, 42.818 ops/sec
ECC [ SECP256R1] 256 key gen 191 ops took 1.005 sec, avg 5.259 ms, 190.137 ops/sec
ECDHE [ SECP256R1] 256 agree 200 ops took 1.050 sec, avg 5.249 ms, 190.501 ops/sec
ECDSA [ SECP256R1] 256 sign 200 ops took 1.079 sec, avg 5.397 ms, 185.297 ops/sec
ECDSA [ SECP256R1] 256 verify 300 ops took 1.099 sec, avg 3.663 ms, 273.009 ops/sec
CURVE 25519 key gen 4818 ops took 1.000 sec, avg 0.208 ms, 4817.469 ops/sec
CURVE 25519 agree 4900 ops took 1.020 sec, avg 0.208 ms, 4801.991 ops/sec
Benchmark complete
@robimarko when you have a chance could you pull Eneas fix for wolfssl devcrypto compile fix - https://git.openwrt.org/?p=openwrt/openwrt.git;a=commit;h=c18c6e53b9860b248986cea4b6856806a65af73c
thank you