Hello to all, I'm new to this community and OpenWRT. Beautiful project!
I just need a little help.
I successfully installed OpenWRT on a TP-Link Archer C6 v2. And works fine.
Now I need to add a public ip subnet assigned to me by my provider. What I need is to assign some public ip to some of my hosts. But I don't find how to. This is the (fake) subnet:
10.0.0.208/29
10.0.0.209 Gateway
10.0.0.215 Broadcast
10.0.0.210~214 Public ip availables for my hosts
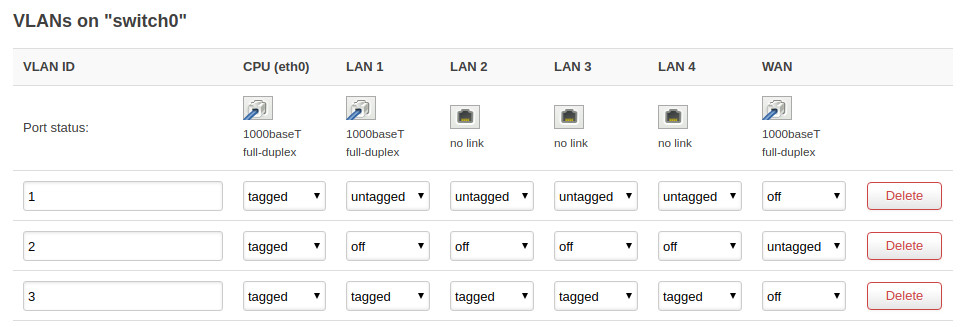
And this is my initial network configuration (all others settings are default).
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd9d:c7e1:b5bb::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.0.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'eth0.2'
option proto 'pppoe'
option username 'myusername'
option password 'mypassword'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
option auto '0'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0t 2 3 4 5'
option vid '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
I search over this forum and all over the whole Internet, but find nothing. Thank you in advance.