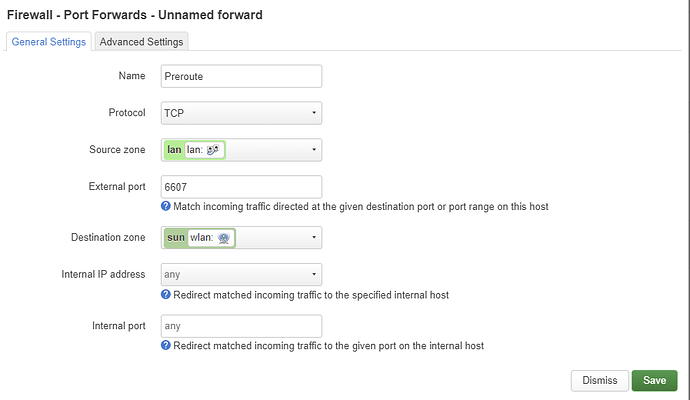
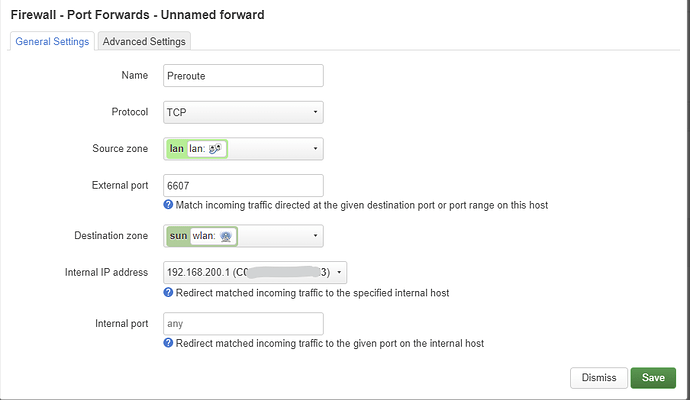
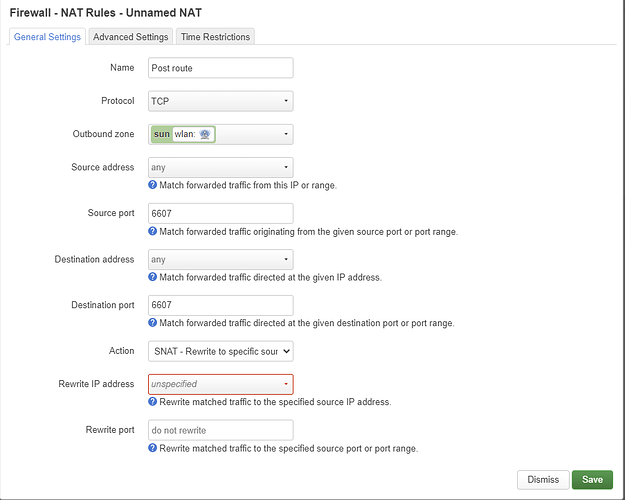
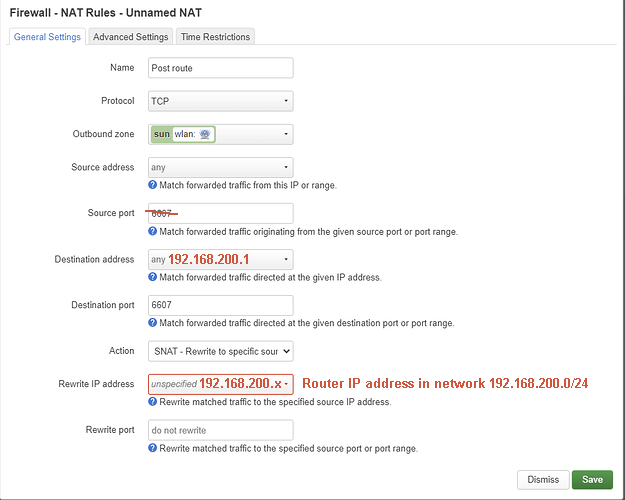
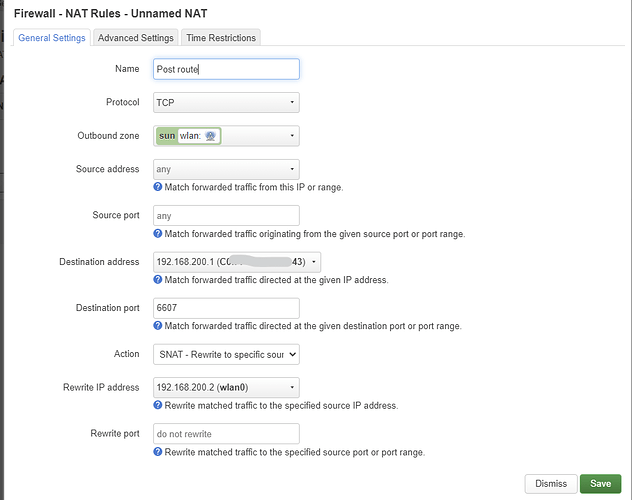
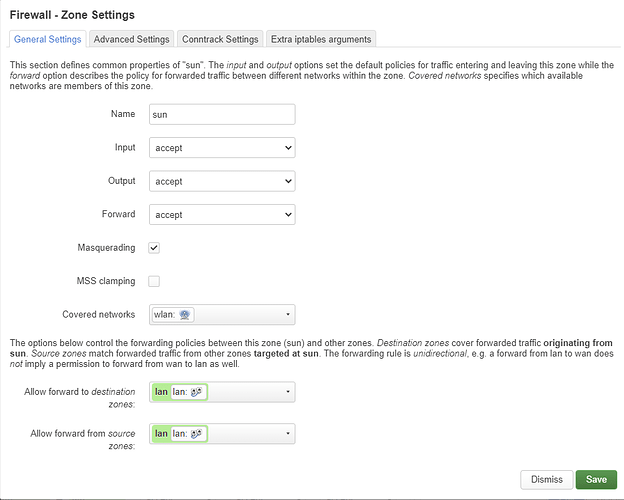
Swap the source and destination zones. The internal IP address must be 192.168.200.1.
Check the rule running
iptables -t nat -nvL zone_lan_prerouting
KOA
June 26, 2022, 2:49pm
7
is this correct for the first rule now?
will the second rule will be required or not? https://openwrt.org/docs/guide-user/network/routedclient#using_masquerade
The internal IP address is missing.
EDIT:
Disable NAT Loopback in the first rule and enable MASQUERADING on the sun zone.
trendy
June 26, 2022, 7:43pm
9
I think it would be better with a SNAT rule.
1 Like
KOA
June 27, 2022, 5:14am
11
Is this correct?
and for second rules, if we follow SNAT
and in case of MASQUERADING
I am doing it write or anything wrong?
If I understood the situation correctly, the router is connected to the inverter as a DHCP client via a wireless connection in sta mode.
The router's IP address may change and the SNAT rule will need to be updated.
I don't think it's worth the effort, especially if the inverter is the only one device in the "sun" zone/network and the benefits of SNATing (or more precise masquerading) are questionable...
1 Like
KOA
June 27, 2022, 6:24am
14
OpenWRT router is the only device connected to the inverter and vice versa is true. The inverter only allows one connection at a time.
KOA
June 27, 2022, 6:40am
15
For the second rule with SNAT.
or should I follow masquerading?
and for the first rule
and NAT loopback disabled for the first rule.
You can use the SNAT rule. The rest seems to be correct, but to be sure please SSH into the router and post the output of the following commands:
iptables -t nat -nvL zone_lan_prerouting; iptables -t nat -nvL zone_sun_postrouting
I assume you used lowercase letters for the name of the "sun" zone. If not, update the second command accordingly.
KOA
June 27, 2022, 7:32am
17
output
root@OpenWrt:~# iptables -t nat -nvL zone_lan_prerouting; iptables -t nat -nvL zone_sun_postrouting
iptables: No chain/target/match by that name.
iptables: No chain/target/match by that name.
edit:
iptables-save -c nat
Redact only the public IPs (if any)
KOA
June 27, 2022, 7:38am
19
strange
root@OpenWrt:~# iptables-save -c nat
Unknown arguments found on commandline
root@OpenWrt:~# iptables-save -c nat
Unknown arguments found on commandline
root@OpenWrt:~#
KOA
June 27, 2022, 7:41am
21
output for this command
root@OpenWrt:~# iptables-save -t nat -c
# Generated by iptables-save v1.8.7 on Mon Jun 27 12:40:16 2022
*nat
:PREROUTING ACCEPT [4382:797175]
:INPUT ACCEPT [52:6894]
:OUTPUT ACCEPT [1084:82382]
:POSTROUTING ACCEPT [1088:82686]
:ts-postrouting - [0:0]
[1088:82686] -A POSTROUTING -j ts-postrouting
[0:0] -A ts-postrouting -m mark --mark 0x40000 -j MASQUERADE
COMMIT
# Completed on Mon Jun 27 12:40:16 2022
Something is wrong here. All default chains are missing. Did you install iptables additionally?
ubus call system board; nft list chain inet fw4 forward
KOA
June 27, 2022, 7:52am
23
# Completed on Mon Jun 27 12:40:16 2022
root@OpenWrt:~# ubus call system board; nft list chain inet fw4 forward
{
"kernel": "5.4.188",
"hostname": "OpenWrt",
"system": "Qualcomm Atheros QCA956X ver 1 rev 0",
"model": "Netgear WNDR4300 v2",
"board_name": "netgear,wndr4300-v2",
"release": {
"distribution": "OpenWrt",
"version": "21.02.3",
"revision": "r16554-1d4dea6d4f",
"target": "ath79/nand",
"description": "OpenWrt 21.02.3 r16554-1d4dea6d4f"
}
}
-ash: nft: not found
N I didn't install iptables. Only installed fping opkg.
/etc/init.d/firewall status; /etc/init.d/firewall restart; iptables-save -t nat -c
1 Like
KOA
June 27, 2022, 8:07am
25
root@OpenWrt:~# /etc/init.d/firewall status; /etc/init.d/firewall restart; iptables-save -t nat -c
inactive
Warning: Unable to locate ipset utility, disabling ipset support
Warning: Section @zone[1] (wan) cannot resolve device of network 'wwan'
* Flushing IPv4 filter table
* Flushing IPv4 nat table
* Flushing IPv4 mangle table
* Flushing IPv6 filter table
* Flushing IPv6 mangle table
* Flushing conntrack table ...
* Populating IPv4 filter table
* Rule 'Allow-DHCP-Renew'
* Rule 'Allow-Ping'
* Rule 'Allow-IGMP'
* Rule 'Allow-IPSec-ESP'
* Rule 'Allow-ISAKMP'
* Redirect 'Pre route'
* Forward 'lan' -> 'wan'
* Forward 'lan' -> 'sun'
* Forward 'sun' -> 'lan'
* Zone 'lan'
* Zone 'wan'
* Zone 'sun'
* Populating IPv4 nat table
* Redirect 'Pre route'
* NAT 'Post route'
* Zone 'lan'
* Zone 'wan'
* Zone 'sun'
* Populating IPv4 mangle table
* Zone 'lan'
* Zone 'wan'
* Zone 'sun'
* Populating IPv6 filter table
* Rule 'Allow-DHCPv6'
* Rule 'Allow-MLD'
* Rule 'Allow-ICMPv6-Input'
* Rule 'Allow-ICMPv6-Forward'
* Rule 'Allow-IPSec-ESP'
* Rule 'Allow-ISAKMP'
* Forward 'lan' -> 'wan'
* Forward 'lan' -> 'sun'
* Forward 'sun' -> 'lan'
* Zone 'lan'
* Zone 'wan'
* Zone 'sun'
* Populating IPv6 mangle table
* Zone 'lan'
* Zone 'wan'
* Zone 'sun'
* Flushing conntrack table ...
* Set tcp_ecn to off
* Set tcp_syncookies to on
* Set tcp_window_scaling to on
* Running script '/etc/firewall.user'
# Generated by iptables-save v1.8.7 on Mon Jun 27 13:05:50 2022
*nat
:PREROUTING ACCEPT [9:536]
:INPUT ACCEPT [3:176]
:OUTPUT ACCEPT [1:100]
:POSTROUTING ACCEPT [1:100]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_sun_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_sun_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_sun_postrouting - [0:0]
:zone_sun_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[7:438] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[7:438] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[0:0] -A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_wan_prerouting
[0:0] -A PREROUTING -i wlan0 -m comment --comment "!fw3" -j zone_sun_prerouting
[1:100] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[1:100] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[0:0] -A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A POSTROUTING -o wlan0 -m comment --comment "!fw3" -j zone_sun_postrouting
[1:100] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[7:438] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[0:0] -A zone_lan_prerouting -p tcp -m tcp --dport 6607 -m comment --comment "!fw3: Pre route" -j DNAT --to-destination 192.168.200.1:6607
[0:0] -A zone_sun_postrouting -m comment --comment "!fw3: Custom sun postrouting rule chain" -j postrouting_sun_rule
[0:0] -A zone_sun_postrouting -d 192.168.200.1/32 -p tcp -m tcp --dport 6607 -m comment --comment "!fw3: Post route" -j SNAT --to-source 192.168.200.2
[0:0] -A zone_sun_postrouting -m comment --comment "!fw3" -j MASQUERADE
[0:0] -A zone_sun_prerouting -m comment --comment "!fw3: Custom sun prerouting rule chain" -j prerouting_sun_rule
[0:0] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[0:0] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[0:0] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Mon Jun 27 13:05:50 2022