At least set the DoH canary domain (simply add it to your local adblock blacklist) for a start (efahl's suggestion is more comprehensive, of course).
As others have mentioned, you might need to setup DNS Hijacking. AdBlock has this feature also, by enabling the "Force Local DNS".
Thanks everyone for the responses.
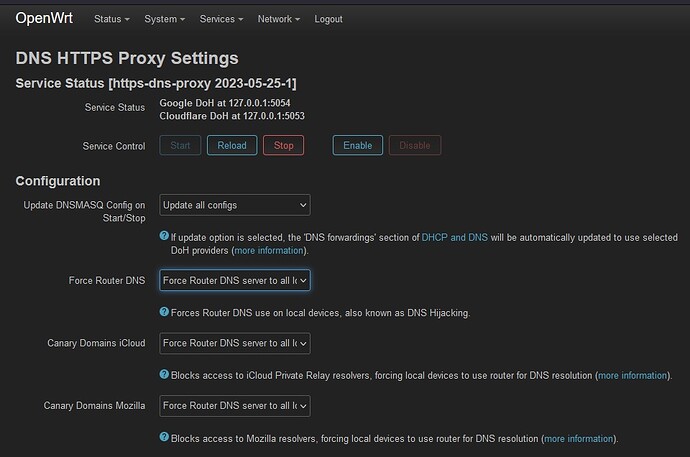
I already have "Force local dns" turned on on Adblock, but I think the issue might be related to the fact that I'm using DNS over HTTPS
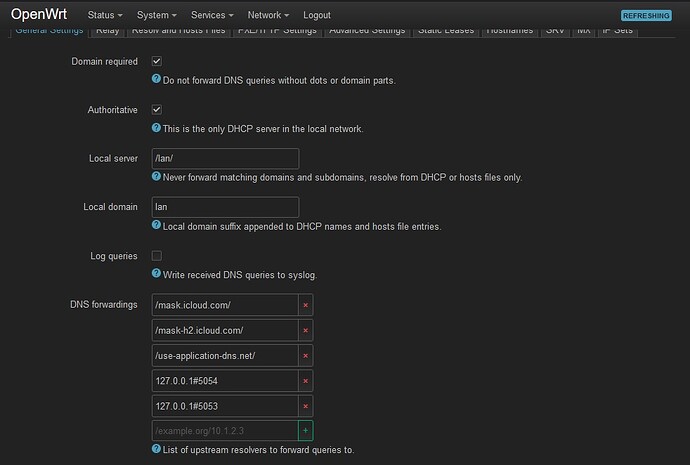
This is what my adblock, dnsoverhhtps and dns config looks like
Oh.. I'm also using "HTTPS DNS Proxy". You don't need to enable AdBlock's "Force Local DNS" because the dns proxy already takes care of that. It's actually redundant if enabling it also in Adblock.
For your issue, the script that you are thinking of might help. @efahl suggestions will help you go in the right direction. I really haven't tested the scenario you are mentioning on edge and chrome when in incognito but If I've got time I might look into it.
Thanks for the quick reply
Yes, I did try the script but it's only for fw4 so I did it manually and nothing has changed so far, Chrome and Edge keep using their own DNS and accessing websites that should be blocked. I will keep investigating.
EDIT: Ive also tried adding use-application-dns.net to the adblock blocklist as @slh suggested.
EDIT2: This all only occurs when I set up 8.8.8.8 on my PC. If I put 192.168.1.1 everything gets blocked on both chrome and edge. Just wanted to know what can I do to force all clients to use the local dns instead of whatever the client cfg says.
Your experience is kind of weird. I know I've done some similar test but not on incognito and I'm sure they're being blocked properly. I'll do some experiments later and see if I can replicate your issue.
Edge and Chrome might be doing some HTTPS-OVER-DNS but that shouldn't already happen as it should already be handled by the forced dns by the https dns proxy. But let's see.
There is one more thing you can do, but I'm not sure if your xiaomi 4a has enough space to add it. Using BanIP and enabling the doh feed to block all known DNS from your internal network.
You can test this if this works without installing BanIP by adding a test firewall rule to reject, for example 8.8.8.8, in your internal network and see if Edge and Chrome was still able to browse the blocked domain during those few minutes/seconds your router is still staring the adblock service. Oh and by the way, if this works, it means somehow Edge and Chrome was able to bypass the forced dns which again weird.
Oh wait.. I just realized something on your config @anon43134599. The forced ports on AdBlock.
- Don't include WAN
- change the forced ports to 53, 853, 5353

When I checked the startup sequence, AdBlock is started before https-dns-proxy. Dns proxy is started on the end portion of the boot process.
Try these changes first before doing the test blocking thing.
Note: You might need to cleanup the generated port forwardings of adblock. Got to Firewall -> Port Fowarding to check.
Thanks, I've followed the steps above and no results. The weirdest part is that I just installed banip and simple adblock to block the same sites and I still can access them so I guess there's some kind of misconfiguration somewhere, unrelated to adblock I believe.
Thanks!
There is no misconfiguration, it's just a timing issue. Most routers is not powerful enough to boot very fast enough to load all necessary service in time.
Your issue is coming from the fact, that upon boot routers allow users to start browsing as long as the internet connection is already up while it's booting other services. I've tested this on a VM with 2.4Ghz quad core power and still there is a minute or two before all services finishes its startup (like adblock and banip).
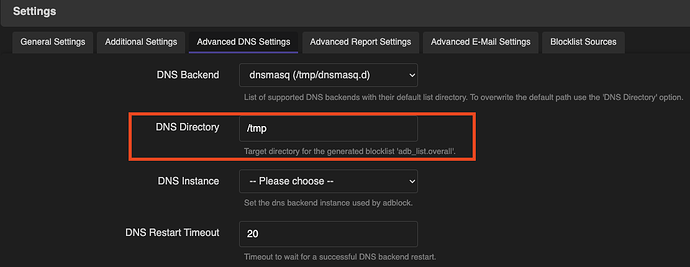
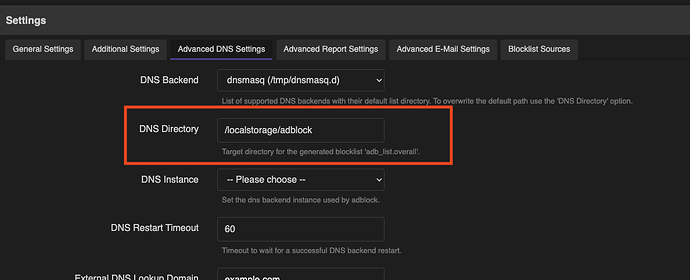
A probable workaround is moving the "DNS Directory" in the "Advanced DNS Settings" in AdBlock to a location that survives bootup. Unless the specified location is in a USB drive (which your device can't have), it will probably in a location that is in the flash portion of the router which in turn "not recommended" as there is a maximum a maximum read/write for any flash based memory. Remember flash mems of routers can't be easily replaced or can't be replaced at all. This limits the number of times you can save/delete/update a file.
In theory, by changing the said directory to somewhere that survives bootup, dnsmasq will load the list upon start the adb_list.overall which contains the processed domains for blocking by AdBlock. And this will make sure blocklist is loaded already even before AdBlock has finished it's startup process.
I've tested the above scenario and it works even before AdBlock had started. For the test i've even forced AdBlock to startup 60 seconds after the test router has booted.
The
/localstorage/adblock is a directory that is not part of the tempfs (/tmp folder) which survives a reboot (even a full shutdown/power off then startup/power on) of the test router.
I've opened one of the known porn sites (as porn is blocked network wide on both my actual and test routers) even before AdBlock was able to start.
With the above solution, you don't need to actually do a script to detect if adblock has finished running or not. Only caveat, you will need to store the "DNS Directory" in a location that will be probably part of the flash memory (like for example /root).
Thanks for the detailed response, really appreciate.
But I say that I think this is a misconfiguration issue somewhere because this only occurs when, let's say, I configure my PC dns to 8.8.8.8 instead of 192.168.1.1.
If I use 192.168.1.1 as DNS on every device, everything works and every device is blocked from accessing those sites 2 minutes after the router has booted so AdBlock works. I wish I knew whats preventing ooenwrt from forcing all clients to use 192.168.1.1 and enjoy the benefits of AdBlock, banip etc
Thanks again for all your help
If Chrome detects your machine’s DNS as being capable of DoH it will silently switch to DoH with that DNS service.
As @AcidSlide said, use banIP to block all DNS servers.
In banip Blocklist Feed Selection, select doh feed.
To test banIP is blocking them ping 8.8.8.8, you will get a no reply and the bellow log from banip:
Sun Jun 18 12:35:54 2023 kern.warn kernel: [156562.761673] banIP/fwd-lan/rej/dohv4: IN=br-lan OUT=wan MAC=xx SRC=xx DST=8.8.8.8 LEN=60 TOS=0x00 PREC=0x00 TTL=127 ID=53501 PROTO=ICMP TYPE=8 CODE=0 ID=1 SEQ=21
It won't be possible to use the blocked DNS servers (listed in doh feed) if they are blocked with banIP.
You can get the DNS Canary domain for free from oisd_big and doh_blocklist sources (possibly others, those are where I see them in my lists). Might just be safest to add it explicitly to the blocklist, that will ensure it's there regardless of what lists are configured...
i would just like to add an additional info regarding moving the "DNS Directory" configuration in AdBlock (as i've mentioned in this comment: Adblock support thread - #2456 by AcidSlide). This new comment is regarding moving it to a USB flash/drive location. I'm just going slightly off topic here but the issue raised to me was because I pointed out moving the file generated by AdBlock to a USB drive.
Somebody from our local tech group in our country pointed out to me (you know who you are ![]() hehe) the danger of putting up files needed upon boot up of the router on the USB as there is a chance when booting up, the USB won't be mounted (obviously due to some error) which in turn wreck havoc on the router. Now this issue usually only happens if the mount point of the usb is in somewhere like
hehe) the danger of putting up files needed upon boot up of the router on the USB as there is a chance when booting up, the USB won't be mounted (obviously due to some error) which in turn wreck havoc on the router. Now this issue usually only happens if the mount point of the usb is in somewhere like /mnt/sda1 which is the usual default mounting of OpenWRT.
The issue is, just in case the router was unable to mount the USB to /mnt/sda1 upon bootup it will wreck havoc (possibility is high) on the main routers flash module while it's trying to read/write the necessary files it needed to finish booting (like the AdBlock directory for the blocklist needed by dnsmasq). And this has happened numerous times already to peeps here using OpenWRT which in turn maxed out the maximum writes that can be made on the flash memory. The problem here is that the /mnt folder is (by default) is located in the flash memory.
To circumvent this, use the tempfs folder as the mounting folder (which is the /tmp) for the mounting points of the USB flash/drives.
Example, instead of /mnt/sda1 use /tmp/sda1 or /tmp/usb1 instead. This will make sure even in the even that the USB wasn't mounted, it still just using the tempfs.
Hi @dibdot,
The feed url for adguard_tracking is now invalid.
Old URL: https://raw.githubusercontent.com/AdguardTeam/cname-trackers/master/combined_disguised_trackers_justdomains.txt
New URL: https://raw.githubusercontent.com/AdguardTeam/cname-trackers/master/data/combined_disguised_trackers_justdomains.txt
Hi, @dibdot !
I believe openphish list should be removed from any DNS blocking app. It contains list of phishing URLs rather than just domain names. Blocking full domain is excessive in this case.
Today and a few weeks ago, the blacklist reset. Today I added one hostname from the DNS report page, and when I switched to the blacklist, there was just the one hostname.
How to prevent resetting the blacklist?
OpenWrt 22.03.5 r20134-5f15225c1e / LuCI openwrt-22.03 branch git-23.119.80898-65ef406
Belkin RT3200
Status / Version
enabled / 4.1.5
Blocked Domains
10,955
Active Sources
custom, doh_blocklist, utcapitole, yoyo
DNS Backend
dnsmasq (-), /tmp/dnsmasq.d
Run Utils
download: /bin/uclient-fetch, sort: /usr/libexec/sort-coreutils, awk: /bin/busybox
Run Interfaces
trigger: -, report: any
Run Directories
base: /tmp, backup: /etc/adblock, report: /tmp/adblock-Report, jail: /tmp
Run Flags
backup: ![]() , flush: ✘, force:
, flush: ✘, force: ![]() , search: ✘, report:
, search: ✘, report: ![]() , mail: ✘, jail: ✘
, mail: ✘, jail: ✘
Last Run
reload, 0m 54s, 494/408/395, 2023-06-29T03:00:54-06:00
Hi @ahz, welcome to the OpenWrt forums!
I have not had your experience, adding from reports, doing over a dozen sysupgrades, my blacklist is maintained. Did you do anything recently like re-install adblock or do a system upgrade or whatever that might have caused this?
The blacklist should be included in the "saved" files by the adblock installation, you can check it using sysupgrade -l to make sure it's included in backups and upgrades. Here's how I just looked at the setup:
$ cat /etc/adblock/adblock.blacklist
inc.hp.com
hpeprint.com
www1.hp.com
www2.hp.com
$ sysupgrade -l | grep adblock
/etc/adblock/adblock.blacklist
/etc/adblock/adblock.whitelist
/etc/config/adblock
If you run that last command and don't see those files, then something isn't installed correctly.
We leverage something like this in adblock-lean as part of our various tests that all is well with the processed and loaded blocklist (which may include local and/or combination of merged remote blocklists) like so:
Please don't point your backup directory to a flash based directory used by adblock core.