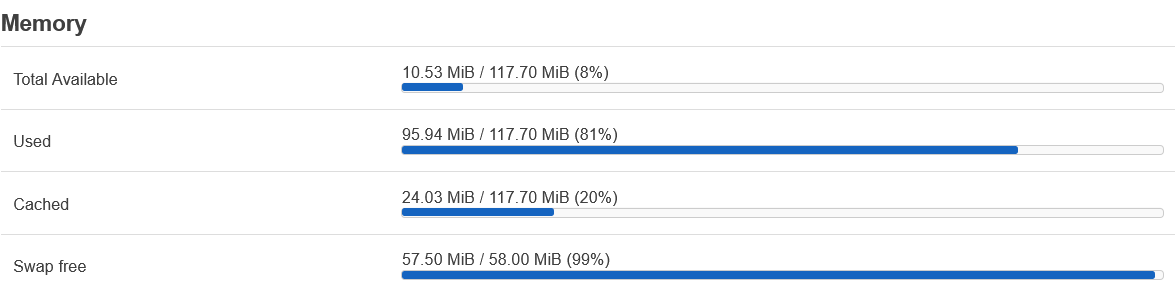
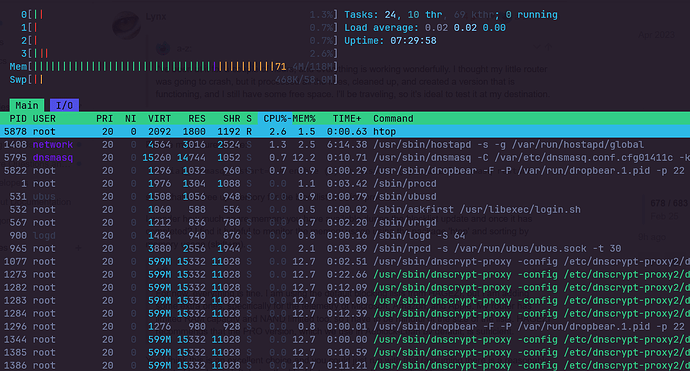
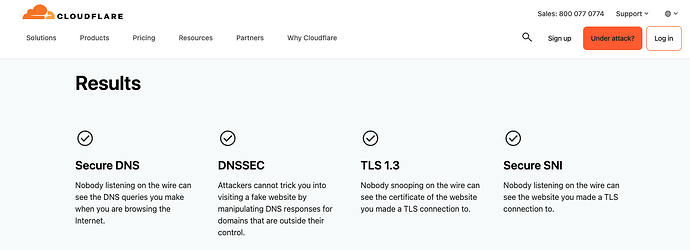
the point being, its a manualy installed add-on instead of built properly into the images with say a proper uci config
I'll happily make it into a package for you for £10,000?
bit ridiculous price... any decent coder could package this in a few hours. moving on now!
Evidence A: Openwrt 128 Mb Ram Linksys E5600
Evidence B : Using Hagezi pro + microsoft + amazon and apple lists.
Extra Packages: Htop, Nano, TravelMate,
I'll try later the other recommendations for the list I need some memory extra because I need to add the WireGuard package since this router is traveling again with me.
I use dnyproxy2 for because it does the dns hijacking and makes also use of DNS DoH so I can filter all the annoying ads that want to go under radar with google dns or their own dns hardware coded.
I mean I can try to use stubby but I just want to be able to bypass dns rules in hotels/airport/corporate while traveling. so DoH is a nice way to do it. Also Unbound would be a good idea and it will be my own recursive dns server but I never tried to install in OpenWrt it seems is like a PITA.
do we have to do something to update that?
you can use dns-over-https, low ram
yup.
debug cloudflare:

now with browser integrity check
plus getting ads blocked with adblock-lean
I may need to reduce the list in order to save ram memory but I'm using the zram package too.
great but I meant, dns over https package from openwrt instead of dnscrypt-proxy2
I did tried before but the thing was when openwrt before 22.x was using iptables 3 was relative easy to enforce dns and make rules and after 22.x they added nft instead ip3 and I could not do dns hijacking so easily at least I didn't know how to do it. So for me was easier to use the dnsencrypt proxy2 to be able to do the hijacking.
I'm checking this thread DNS-over-HTTPS packages - #2 by Ramon let me try
DNS hijacking is easy - it’s just:
https://openwrt.org/docs/guide-user/firewall/fw3_configurations/intercept_dns
Thank you Lynx, yes I remember to read the FW3 configurations but those rules uses FW3 and openwrt 21.02 was the last version to use them. In 22.03 changed to NFtables (FW4) I couldn't make it work at the time and when I asked in the forums, no body seems to know how to do it. So I found easier just to use the dnsproxy2 to do the dns hijacking/forcing instead dealing with NFT.
I think i could uninstall the packges for NFT then reinstall FW3 Iptables.
No stubby has some issues, I couldn't make it to work it out even with some tutorials is not DoH just DoT. I'll sacrifice some ram and I'll stay with dnsproxy2
The instructions on that page work just fine with fw4. As in the necessary nftables rules are created with those same instructions.
Otherwise I’m not seeing the benefit in using dnscrypt-proxy over simple stubby. With stubby requests also go via dnsmasq and sent out via port 853 using DNS over TLS. I use the Cloudflare Family DNS over TLS resolver. Stubby is supposedly faster than using DNS over HTTP.
See:
https://openwrt.org/docs/guide-user/services/dns/dot_dnsmasq_stubby
hi. I was on an older version of ad-block lean and figure I update to the latest. After running these cmds, router failed on checking dnsmasq instance.
wget https://raw.githubusercontent.com/lynxthecat/adblock-lean/main/adblock-lean -O /etc/init.d/adblock-lean
chmod +x /etc/init.d/adblock-lean
service adblock-lean gen_config # generates default config in /root/adblock-lean/config
vi /root/adblock-lean/config # modify default config as required
uci add_list dhcp.@dnsmasq[0].addnmount='/bin/busybox' && uci commit # to enable use of compressed blocklist
service adblock-lean enable
error:
root@ac1750:~# service adblock-lean start
Started adblock-lean.
No existing compressed or uncompressed blocklist identified.
No local blocklist identified.
Downloading new blocklist file part(s).
Downloading new blocklist file part from: https://raw.githubusercontent.com/hagezi/dns-blocklists/main/dnsmasq/pro.txt.
Download of new blocklist file part from: https://raw.githubusercontent.com/hagezi/dns-blocklists/main/dnsmasq/pro.txt sucee ded (downloaded file size: 6924 KB; line count: 252698).
Sanitizing blocklist file part.
Checking for any rogue elements.
Successfully generated preprocessed blocklist file with 252698 line(s).
Removing duplicates and forming new preprocessed blocklist file.
No local allowlist identified.
Processed blocklist file size: 6924 KB.
Performing dnsmasq --test on the processed blocklist.
dnsmasq --test output: dnsmasq: syntax check OK.
The dnsmasq --test on the processed blocklist passed.
New blocklist file check passed.
Successfully imported new blocklist file for use by dnsmasq with size: 1809 KB.
Restarting dnsmasq.
Restart of dnsmasq completed.
Checking dnsmasq instance.
No instance of dnsmasq detected with new blocklist.
The dnsmasq check failed with new blocklist file.
No previous blocklist file found.
seems to be the same problem I had, check the comments above
Are you referring to this post? I believe the author had updated github.
yes, ok, but I had the same errors.
just to see, could you try to put that disabled ; compress_blocklist=0
ok. Setting to compress_blocklist to 0 works.
compress_blocklist=0
root@ac1750:~# service adblock-lean start
Started adblock-lean.
No existing compressed or uncompressed blocklist identified.
No local blocklist identified.
Downloading new blocklist file part(s).
Downloading new blocklist file part from: https://raw.githubusercontent.com/hagezi/dns-blocklists/main/dnsmasq/pro.txt.
Download of new blocklist file part from: https://raw.githubusercontent.com/hagezi/dns-blocklists/main/dnsmasq/pro.txt suceeded (downloaded file size: 6924 KB; line count: 252698).
Sanitizing blocklist file part.
Checking for any rogue elements.
Successfully generated preprocessed blocklist file with 252698 line(s).
Removing duplicates and forming new preprocessed blocklist file.
No local allowlist identified.
Processed blocklist file size: 6924 KB.
Performing dnsmasq --test on the processed blocklist.
dnsmasq --test output: dnsmasq: syntax check OK.
The dnsmasq --test on the processed blocklist passed.
New blocklist file check passed.
Successfully imported new blocklist file for use by dnsmasq with size: 6924 KB.
Restarting dnsmasq.
Restart of dnsmasq completed.
Checking dnsmasq instance.
The dnsmasq check passed with new blocklist file.
New blocklist installed with good line count: 252698.
ok, so it is the same.
Yes we did. The issue there related to sh not being accessible and the fix was to use busybox sh. Perhaps the issue you are seeing is different. Could you post the relevant lines from logread when compress blocklist is set to enabled? Which version of OpenWrt are you running? Since this feature only works in newer versions, we should probably add a check in that respect.
Running ad-lean on:
Model: TP-Link Archer C7 v4
Firmware Version: OpenWrt 22.03.3 r20028-43d71ad93e / LuCI openwrt-22.03 branch git-22.361.69894-438c598