Hi there, just wondering if you have any progress with your OpenWrt installation on the predator w6, got this router but the acer default system is so limited, just useless.
you didn't read the thread, and followed the links, did you ?
I had it working on the 2.4G and 5G bands, 6G doesn't seem to be working, I don't think the openwrt utils have been updated to a working state for 6G yet. Somehow I lost my ability to load openwrt on the device, the boot menu no longer comes up and it boots straight away into the stock firmware.
I kinda think we should have an OpenWRT statesman try to get a contact at Acer to sort this out. Acer is using OpenWRT as a basis for their stock firmware and should at least make their source code and build process available to the community so we can get it to the point where we can flash a firmware from their stock firmware update interface. It seems like a license violation if they don't give us that much.
BTW, the hardware is well built. If we can get OpenWRT sorted on it, this could be the recommended go-to 6E wifi router. I just don't get why hardware vendors don't see the sales opportunity of well-supported OpenWRT.
Openwrt extends the life of their devices, making them sell less new devices.
Try to boot info fail safe mode of stock fw and
mount_root
fw_setenv bootmenu_delay 10
fw_setenv bootdelay 10
reboot
For the 6G, I had to use a different country code (GB or JP) and set the following in /etc/config/wireless
config wifi-device 'radio1'
...
option band '6g'
option htmode 'HE160'
option cell_density '0'
option channel 'auto'
option country 'GB'
Try to set channel manually if ACS won't work, and don't touch any 6g radio settings on luci which will break it, enabling 2.4g radio seems to help 6g discovery for devices
Also upgrading stock fw seems to break openwrt partition and will need to reflash to fix it
Would love to know if others managed to make boot persist though, currently I had to hook up a laptop besides the router to boot into openwrt
W6d differ only with lack of 6GHz radio? Or something more?
Hi,
I just got W6d and I noticed two differences:
- 4 antennas instead of 6 due to lack of 6GHz radio as you pointed out
- 2A/12V instead of 3A/12V power adapter
Serial connection can be established without opening the case and without soldering.
USB TTL adapter is needed, standard serial connection parameters 115200 8N1, pins layout is as described in git commit:
[BUTTON] GND - RX - TX [USB]
More general info regarding serial
Few words regarding Acer firmware:
- Not available to download from Acer ‘Product Support’ website https://www.acer.com/us-en/support/product-support/Predator_Connect_W6d_Wi-Fi_6_Router
- In Acer firmware WebGui (System -> Firmware update), there is no possibility to manually upload file with firmware, there is only option to ‘Check new’ to see if an update is available, however... Firmware automatically updates itself once device is connected to the Internet - looks like there is no control over automatic firmware updates
- I captured serial output and tcpdump trace during automatic firmware update, but in wireshark traces I could only see TLS connections (everything encrypted...) towards:
- qb10-service1.quantatw.com -> during FW Update Check
- qb10-service5.quantatw.com -> during FW download (42MB was downloaded from that address before FW update)
- After update to latest Acer firmware (W6d_2.11.340318), there was no U-boot delay and it was needed to perform steps highlighted few posts above after booting into fail safe mode of stock fw:
mount_root
fw_setenv bootmenu_delay 10
fw_setenv bootdelay 10
reboot
Cheers,
Przemek
Hi,
I’m preparing to install Open WRT on W6d (not regular W6) model with currently available image for W6, however before doing that, I would like to make a backup from U-boot level to be able to restore original Acer firmware if anything goes wrong.
I know that U-Boot is not part of Open WRT, however maybe someone knows how to make ‘raw’ partitions backup from U-Boot level?
Something similar to steps below from Linux level (found here on forum):
1/ list mtd partitions
cat /proc/mtd
2/ backup a partition
dd if=/dev/mtd11 of=/media/usb/backup_mtd11.bin
3/ restore a partition
mtd -r /media/usb/backup_mtd11.bin /dev/mtd11
However I believe it would be needed to upload partition backups to tftp server instead of USB stick - I do not see ‘usb’ command in the U-Boot help for W6d.
Official docs not so helpful:
mmc info from U-Boot:
MT7986> mmc info
Device: mmc@11230000
Manufacturer ID: ec
OEM: 0
Name: SM0000
Bus Speed: 52000000
Mode: MMC High Speed (52MHz)
Rd Block Len: 512
MMC version 5.1
High Capacity: Yes
Capacity: 3.6 GiB
Bus Width: 8-bit
Erase Group Size: 512 KiB
HC WP Group Size: 16 MiB
User Capacity: 3.6 GiB
Boot Capacity: 4 MiB ENH
RPMB Capacity: 4 MiB ENH
Boot area 0 is not write protected
Boot area 1 is not write protected
MT7986> mmc list
mmc@11230000: 0 (eMMC)
MT7986>
mmc part from U-Boot:
MT7986> mmc part
Partition Map for MMC device 0 -- Partition Type: EFI
Part Start LBA End LBA Name
Attributes
Type GUID
Partition GUID
1 0x00000000 0x00000021 "gpt"
attrs: 0x0000000000000000
type: 0fc63daf-8483-4772-8e79-3d69d8477de4
(linux)
guid: 35c58bb6-91ce-11ed-85bf-a81e84c31052
2 0x00002000 0x000023ff "u-boot-env"
attrs: 0x0000000000000000
type: 0fc63daf-8483-4772-8e79-3d69d8477de4
(linux)
guid: 19a4763a-6b19-4a4b-a0c4-8cc34f4c2ab9
3 0x00002400 0x000033ff "factory"
attrs: 0x0000000000000000
type: 0fc63daf-8483-4772-8e79-3d69d8477de4
(linux)
guid: 8142c1b2-1697-41d9-b1bf-a88d76c7213f
4 0x00003400 0x000043ff "fip"
attrs: 0x0000000000000000
type: 0fc63daf-8483-4772-8e79-3d69d8477de4
(linux)
guid: 18de6587-4f17-4e08-a6c9-d9d3d424f4c5
5 0x00004400 0x000143ff "kernel"
attrs: 0x0000000000000000
type: 0fc63daf-8483-4772-8e79-3d69d8477de4
(linux)
guid: 971f7556-ef1a-44cd-8b28-0cf8100b9c7e
6 0x00014400 0x001143ff "rootfs"
attrs: 0x0000000000000000
type: 0fc63daf-8483-4772-8e79-3d69d8477de4
(linux)
guid: 309a3e76-270b-41b2-b5d5-ed8154e7542b
7 0x00114400 0x001243ff "kernel1"
attrs: 0x0000000000000000
type: 0fc63daf-8483-4772-8e79-3d69d8477de4
(linux)
guid: a975393e-a9bc-491f-8133-aeecf6075307
8 0x00124400 0x002243ff "rootfs1"
attrs: 0x0000000000000000
type: 0fc63daf-8483-4772-8e79-3d69d8477de4
(linux)
guid: 32798804-a1a7-4f95-ad5a-48939498675b
9 0x00224400 0x002293ff "qcidata"
attrs: 0x0000000000000000
type: 0fc63daf-8483-4772-8e79-3d69d8477de4
(linux)
guid: 3c607e69-0038-4195-a819-77157883e2df
10 0x00229400 0x0022e3ff "qcidata1"
attrs: 0x0000000000000000
type: 0fc63daf-8483-4772-8e79-3d69d8477de4
(linux)
guid: 613e2af8-cfe5-4701-8e67-facda9ffdd71
11 0x0022e400 0x0032e3ff "rootfs_data"
attrs: 0x0000000000000000
type: 0fc63daf-8483-4772-8e79-3d69d8477de4
(linux)
guid: 5881ba72-d78f-4cbb-8fef-871aeb4b8eef
12 0x0032e400 0x0072e3ff "user_data"
attrs: 0x0000000000000000
type: 0fc63daf-8483-4772-8e79-3d69d8477de4
(linux)
guid: e6f92786-dc2f-4b91-b33c-92b3f18c2548
MT7986>
lsblk from stock firmware
root@acerconnect:/# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
mmcblk0 179:0 0 3.6G 0 disk
├─mmcblk0p1 179:1 0 17K 0 part
├─mmcblk0p2 179:2 0 512K 0 part
├─mmcblk0p3 179:3 0 2M 0 part
├─mmcblk0p4 179:4 0 2M 0 part
├─mmcblk0p5 179:5 0 32M 0 part
├─mmcblk0p6 179:6 0 512M 0 part
│ └─dm-verity 254:0 0 42.9M 1 dm /rom
├─mmcblk0p7 179:7 0 32M 0 part
├─mmcblk0p8 259:0 0 512M 0 part
├─mmcblk0p9 259:1 0 10M 0 part /qcidata
├─mmcblk0p10 259:2 0 10M 0 part /qcidata1
├─mmcblk0p11 259:3 0 512M 0 part /overlay
└─mmcblk0p12 259:4 0 2G 0 part /data
mmcblk0boot0 179:8 0 4M 1 disk
mmcblk0boot1 179:16 0 4M 1 disk
root@acerconnect:/#
Thanks in advance,
Przemek
Hi,
I installed OpenWrt on my Acer W6d, played a little bit with it and here are my sad conclusions.
There is no snand memory where factory fw is installed- everything is kept in eMMC. Dual boot works in the following way - there are "kernel" and "rootfs" partitions referred as slot 0 and "kernel1" and "rootfs1" partitions referred as slot 1. Partitions layout is as follows:
root@acerconnect:/# blkid
/dev/mmcblk0p1: PTTYPE="PMBR"
/dev/mmcblk0p2: PARTLABEL="u-boot-env" PARTUUID="19a4763a-6b19-4a4b-a0c4-8cc34f4c2ab9"
/dev/mmcblk0p3: PARTLABEL="factory" PARTUUID="8142c1b2-1697-41d9-b1bf-a88d76c7213f"
/dev/mmcblk0p4: PARTLABEL="fip" PARTUUID="18de6587-4f17-4e08-a6c9-d9d3d424f4c5"
/dev/mmcblk0p5: PARTLABEL="kernel" PARTUUID="971f7556-ef1a-44cd-8b28-0cf8100b9c7e"
/dev/mmcblk0p6: TYPE="squashfs" PARTLABEL="rootfs" PARTUUID="309a3e76-270b-41b2-b5d5-ed8154e7542b"
/dev/mmcblk0p7: PARTLABEL="kernel1" PARTUUID="a975393e-a9bc-491f-8133-aeecf6075307"
/dev/mmcblk0p8: TYPE="squashfs" PARTLABEL="rootfs1" PARTUUID="32798804-a1a7-4f95-ad5a-48939498675b"
/dev/mmcblk0p9: UUID="d2829ff8-fc66-445a-949d-d4cdfaffc52e" BLOCK_SIZE="1024" TYPE="ext4" PARTLABEL="qcidata" PARTUUID="3c607e69-0038-4195-a819-77157883e2df"
/dev/mmcblk0p10: UUID="2a275f1b-0b86-4993-bef1-dab07937c25d" BLOCK_SIZE="1024" TYPE="ext4" PARTLABEL="qcidata1" PARTUUID="613e2af8-cfe5-4701-8e67-facda9ffdd71"
/dev/mmcblk0p11: LABEL="rootfs_data" UUID="1cb2a3bd-7c92-4748-bd2c-7a8c8a0bd450" BLOCK_SIZE="4096" TYPE="f2fs" PARTLABEL="rootfs_data" PARTUUID="5881ba72-d78f-4cbb-8fef-871aeb4b8eef"
/dev/mmcblk0p12: UUID="b9d81119-f74e-49da-8f36-0d68d3733c5a" BLOCK_SIZE="4096" TYPE="ext4" PARTLABEL="user_data" PARTUUID="e6f92786-dc2f-4b91-b33c-92b3f18c2548"
/dev/mapper/dm-verity: TYPE="squashfs"
root@acerconnect:/#
In U-Boot, there is an environment variable that decides from which slot system boots up:
dual_boot.current_slot=0
Partitions that are used to boot up are referred as "boot" and the other partitions are referred as "upgrade" - new firmware is installed on "upgrade" partitions, once upgrade is completed, slot from which system boots is changed.
After booting from slot 0 (dual_boot.current_slot=0), /rom is mounted at "rootfs" partition:
root@acerconnect:/# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
mmcblk0 179:0 0 3.6G 0 disk
├─mmcblk0p1 179:1 0 17K 0 part "gpt"
├─mmcblk0p2 179:2 0 512K 0 part "u-boot-env"
├─mmcblk0p3 179:3 0 2M 0 part "factory"
├─mmcblk0p4 179:4 0 2M 0 part "fip"
├─mmcblk0p5 179:5 0 32M 0 part "kernel"
├─mmcblk0p6 179:6 0 512M 0 part "rootfs"
│ └─dm-verity 254:0 0 42.9M 1 dm /rom
├─mmcblk0p7 179:7 0 32M 0 part "kernel1"
├─mmcblk0p8 259:0 0 512M 0 part "rootfs1"
├─mmcblk0p9 259:1 0 10M 0 part /qcidata "qcidata"
├─mmcblk0p10 259:2 0 10M 0 part /qcidata1 "qcidata1"
├─mmcblk0p11 259:3 0 512M 0 part /overlay "rootfs_data"
└─mmcblk0p12 259:4 0 2G 0 part /data "user_data"
mmcblk0boot0 179:8 0 4M 1 disk
mmcblk0boot1 179:16 0 4M 1 disk
root@acerconnect:/#
Additionally, if we check kernel parameters, "kernel" and "rootfs" partitions are referred as "boot" and "kernel1" and "rootfs1" are referred as "upgrade":
root@acerconnect:/# cat /proc/cmdline
...
boot_param.boot_kernel_part=PARTUUID=971f7556-ef1a-44cd-8b28-0cf8100b9c7e
boot_param.boot_rootfs_part=PARTUUID=309a3e76-270b-41b2-b5d5-ed8154e7542b
boot_param.upgrade_kernel_part=PARTUUID=a975393e-a9bc-491f-8133-aeecf6075307
boot_param.upgrade_rootfs_part=PARTUUID=32798804-a1a7-4f95-ad5a-48939498675b
...
After booting from slot 1 (dual_boot.current_slot=1), /rom is mounted at "rootfs1" partition:
root@acerconnect:/# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
mmcblk0 179:0 0 3.6G 0 disk
├─mmcblk0p1 179:1 0 17K 0 part
├─mmcblk0p2 179:2 0 512K 0 part
├─mmcblk0p3 179:3 0 2M 0 part
├─mmcblk0p4 179:4 0 2M 0 part
├─mmcblk0p5 179:5 0 32M 0 part "kernel"
├─mmcblk0p6 179:6 0 512M 0 part "rootfs"
├─mmcblk0p7 179:7 0 32M 0 part "kernel1"
├─mmcblk0p8 259:0 0 512M 0 part "rootfs1"
│ └─dm-verity 254:0 0 42.6M 1 dm /rom
├─mmcblk0p9 259:1 0 10M 0 part /qcidata
├─mmcblk0p10 259:2 0 10M 0 part /qcidata1
├─mmcblk0p11 259:3 0 512M 0 part /overlay
└─mmcblk0p12 259:4 0 2G 0 part /data
mmcblk0boot0 179:8 0 4M 1 disk
mmcblk0boot1 179:16 0 4M 1 disk
root@acerconnect:/#
In kernel parameters, "kernel1" and "rootfs1" partitions are referred as "boot" and "kernel" and "rootfs" are referred as "upgrade":
root@acerconnect:/# cat /proc/cmdline
...
boot_param.boot_kernel_part=PARTUUID=a975393e-a9bc-491f-8133-aeecf6075307
boot_param.boot_rootfs_part=PARTUUID=32798804-a1a7-4f95-ad5a-48939498675b
boot_param.upgrade_kernel_part=PARTUUID=971f7556-ef1a-44cd-8b28-0cf8100b9c7e
boot_param.upgrade_rootfs_part=PARTUUID=309a3e76-270b-41b2-b5d5-ed8154e7542b
...
Initially, in my router, slot 1 was active, sotck fw W6d_1.04.308515 was there, after automatic upgrade, stock fw version W6d_2.11.340318 appeared in slot 0 and system was booting from slot 0.
By playing with dual_boot.current_slot variable, I was able to switch between old and new stock fw.
Before installing OpenWrt, I changed boot slot to 1 (old stock fw), Open Wrt was installed in slot 0 (newer stock fw was wiped out). With this approach, I can perform upgrade of stock fw and wipe out OpenWrt - it does not work the other way round, because it is not possible to download image with stock fw and perform downgrade because stock fw upgrade is done automatically over encrypted connection.
Unfortunately I have the same issue with mtkboardboot as described by colleagues above, however I found some more details.
After OpenWrt installation in slot 0, I changed boot slot to 0 and tried to boot from it, but unfortunately stock firmware was loaded. After checking the boot logs, I found that system tried initially to boot from slot 0 where OpenWrt is installed, but due to failed signature check, router started to load stock fw from slot 1:
Trying to boot from image slot 0
Reading from 0x880000 to 0x40000000, size 0x200 ... OK
Reading from 0x880000 to 0x40000000, size 0x39e7ec ... OK
## Checking hash(es) for FIT Image at 40000000 ...
Hash(es) for Image 0 (kernel-1): crc32+ sha1+
Hash(es) for Image 1 (fdt-1): crc32+ sha1+
Reading from 0x2880000 to 0x4039e7ec, size 0x200 ... OK
Reading from 0x2880000 to 0x4039e7ec, size 0x5de0b0 ... OK
No rootfs node found in FIT image!
Error: rootfs verification failed
Firmware integrity verification failed
Failed to boot from current image slot, error -74
Saving Environment to MMC... Writing to MMC(0)... OK
Trying to boot from image slot 1
Reading from 0x22880000 to 0x40000000, size 0x200 ... OK
Reading from 0x22880000 to 0x40000000, size 0x363cdb ... OK
## Checking hash(es) for FIT Image at 40000000 ...
Hash(es) for Image 0 (kernel-1): crc32+ sha1+
Hash(es) for Image 1 (fdt-1): crc32+ sha1+
Reading from 0x24880000 to 0x40363cdc, size 0x200 ... OK
Reading from 0x24880000 to 0x40363cdc, size 0x2a96c83 ... OK
Hash(es) for rootfs: crc32+ sha1+
Firmware integrity verification passed
In order to avoid signature check, OpenWrt needs to be booted with the following U-Boot commands that load image from eMMC without signature check:
// boot without signature check
mmc read 0x40000000 0x00004400 0x0010000
fdt addr $(fdtcontroladdr)
fdt rm /signature
bootm 0x40000000
According to OpenWrt installation instructions from git commit, environment variable bootcmd can be set to include those commands:
setenv bootcmd 'mmc read 0x40000000 0x00004400 0x0010000; fdt addr $(fdtcontroladdr); fdt rm /signature; bootm 0x40000000';
saveenv
Once bootcmd variable is set, after interrupting the Autoboot process when prompted by sending '0' twice, it is possible to boot system with 'boot' command from U-Boot:
boot - boot default, i.e., run 'bootcmd' // according to U-Boot help
First entry which is selected if Autoboot process is not interrupted, is mtkboardboot command, because it is the default U-Boot entry as defined by U-Boot environment variables:
bootmenu_0=Startup system (Default)=mtkboardboot
bootmenu_1=Upgrade firmware=mtkupgrade fw
bootmenu_2=Upgrade ATF BL2=mtkupgrade bl2
bootmenu_3=Upgrade ATF FIP=mtkupgrade fip
bootmenu_4=Upgrade eMMC partition table=mtkupgrade gpt
bootmenu_5=Upgrade single image=mtkupgrade simg
bootmenu_6=Load image=mtkload
It is possible to change this entry from U-Boot to include boot command instead of mtkboardboot:
MT7986> setenv bootmenu_0 'Startup system (Default)=boot'
MT7986> saveenv
Saving Environment to MMC... Writing to MMC(0)... OK
MT7986>
After such change and execution of 'bootmenu' command that starts U-Boot menu and selecting first entry 'Startup system (Default)', system executes 'bootcmd' command, it reads eMMC memory and boots without signature check.
Unfortunately, after restart, as colleagues mentioned in posts above, first default entry is reset to mtkboardboot command:
bootmenu_0=Startup system (Default)=mtkboardboot
I found that there is special environment variable 'preboot' that can contain script which is executed before autoboot. It was not defined, so I crated it to change bootmenu_0 before autoboot:
setenv preboot setenv bootmenu_0 'Startup system (Default)=boot'
saveenv
But unfortunately, it looks that preboot variable is not used by stock U-Boot, it is not present after system restart - according to information that I have found, it is used if CONFIG_USE_PREBOOT=y - looks that this was not set during stock U-Boot build.
I tried to change bootmenu_0 variable from stock fw:
root@acerconnect:/# fw_setenv bootmenu_0 'Startup system (Default)=boot'
root@acerconnect:/#
root@acerconnect:/# fw_printenv bootmenu_0
bootmenu_0=Startup system (Default)=boot
root@acerconnect:/#
root@acerconnect:/# fw_printenv bootcmd
bootcmd=mmc read 0x40000000 0x00004400 0x0010000; fdt addr $(fdtcontroladdr); fdt rm /signature; bootm 0x40000000
root@acerconnect:/#
But again, after reboot in U-Boot it get backs to mtkboardboot causing that next boot will be with signature check, it will fail and stock firmware from another slot will be booted. It looks that variable bootmenu_0=Startup system (Default)=mtkboardboot is part of default U-Boot environment (created during U-Boot build) and any changes to this variable will be overwritten after the restart.
CONCLUSION:
Acer provided router with decent platform (2 GHz quad core CPU, 1GB RAM, 4GB eMMC), they used OpenWrt 21.02 as base for their stock firmware, however they locked U-Boot bootloader so that it is not possible to normally boot vanilla OpenWrt. The only way to boot vanilla OpenWrt is to connect serial cable, interrupt autoboot and boot OpenWrt without signature check. It needs to be done after every system restart which makes this router not suitable for daily use because for every restart it is needed to connect laptop with USB TTL adapter and interrupt autoboot.
In my opinion, new U-Boot is needed in order to use vanilla OpenWrt on Acer W6 / W6d routers.
@mesnigan , @cbxbiker61 , @cronop , @blkadder , @diogenes - what is your opinion ?
Cheers,
Przemek
Is this statement really true (also for the W6 without D)?
I could not find anything in the previous instructions that OpenWrt is not persistent.
I've been thinking about it for a while now and wanted to flash my W6 shortly.
Greetings.
Hi Eric,
On the other hand, I did not find anyone posting that vanilla OpenWrt is persistent on W6, I see only posts where people complain about mtkboardboot issue ![]()
And unfortunately I'm 99% percent sure the same situation is on W6 (without D) - in logs from W6 posts above I see the same staff meaning booting from slots and signature check of image during boot up process. So the situation will be the same - after reboot, bootmenu_0 variable in U-Boot will be reset to mtkboardboot causing that next boot will be with signature check, signature check will fail for vanilla OpenWrt and stock firmware from another slot will be booted.
Cheers,
Przemek
Hi @mesnigan ,
If you have time, would you be able to post here boot logs for W6 when booting from slot 0 and from slot 1 with mtkboardboot?
Just change the slot and execute mtkboardboot:
// boot from slot 0
setenv dual_boot.current_slot 0
mtkboardboot
// boot from slot 1
setenv dual_boot.current_slot 1
mtkboardboot
Thanks in advance,
Przemek
Here you go
slot 0
F0: 102B 0000
FA: 1040 0000
FA: 1040 0000 [0200]
F9: 103F 0000
F3: 1006 0033 [0200]
F3: 4001 00E0 [0200]
F3: 0000 0000
V0: 0000 0000 [0001]
00: 0000 0000
BP: 2400 0041 [0000]
G0: 1190 0000
EC: 0000 0000 [2000]
T0: 0000 0276 [010F]
Jump to BL
NOTICE: BL2: v2.6(release):de65b3e9d-dirty
NOTICE: BL2: Built : 15:22:40, Oct 28 2022
NOTICE: WDT: disabled
NOTICE: CPU: MT7986 (2000MHz)
NOTICE: EMI: Using DDR4 settings
NOTICE: EMI: Detected DRAM size: 1024MB
NOTICE: EMI: complex R/W mem test passed
NOTICE: Verifying BL Anti-Rollback Version ... bl_ar_ver:0=0+ OK
NOTICE: Verifying BL Anti-Rollback Version ... bl_ar_ver:0=0+ OK
NOTICE: Verifying BL Anti-Rollback Version ... bl_ar_ver:0=0+ OK
NOTICE: Verifying BL Anti-Rollback Version ... bl_ar_ver:0=0+ OK
NOTICE: Verifying BL Anti-Rollback Version ... bl_ar_ver:0=0+ OK
NOTICE: BL2: Booting BL31
NOTICE: BL31: v2.6(release):de65b3e9d-dirty
NOTICE: BL31: Built : 15:22:47, Oct 28 2022
U-Boot 2022.07-rc3 (Oct 28 2022 - 15:21:39 +0800), Build: jenkins-YX6_MT7986-AX7800-294
CPU: MediaTek MT7986
Model: mt7986-rfb
DRAM: 1 GiB
Core: 68 devices, 19 uclasses, devicetree: separate
MMC: mmc@11230000: 0
Setting bus to 0
Loading Environment from MMC... OK
In: serial@11002000
Out: serial@11002000
Err: serial@11002000
Net: eth0: ethernet@15100000
mtkautoboot gpio_reset:1
*** U-Boot Boot Menu ***
1. Startup system (Default)
2. Upgrade firmware
3. Upgrade ATF BL2
4. Upgrade ATF FIP
5. Upgrade eMMC partition table
6. Upgrade single image
7. Load image
0. U-Boot console
Press UP/DOWN to move, ENTER to select, ESC/CTRL+C to quit
Hit any key to stop autoboot: 0
MT7986> setenv dual_boot.current_slot 0
MT7986> mtkboardboot
Trying to boot from image slot 0
Reading from 0x880000 to 0x40000000, size 0x200 ... OK
Reading from 0x880000 to 0x40000000, size 0x3bb1c0 ... OK
## Checking hash(es) for FIT Image at 40000000 ...
Hash(es) for Image 0 (kernel-1): crc32+ sha1+
Hash(es) for Image 1 (fdt-1): crc32+ sha1+
Reading from 0x2880000 to 0x403bb1c0, size 0x200 ... OK
Reading from 0x2880000 to 0x403bb1c0, size 0x1180ecc ... OK
No rootfs node found in FIT image!
Error: rootfs verification failed
Firmware integrity verification failed
Failed to boot from current image slot, error -74
Saving Environment to MMC... Writing to MMC(0)... OK
Trying to boot from image slot 1
Reading from 0x22880000 to 0x40000000, size 0x200 ... OK
Reading from 0x22880000 to 0x40000000, size 0x363cdb ... OK
## Checking hash(es) for FIT Image at 40000000 ...
Hash(es) for Image 0 (kernel-1): crc32+ sha1+
Hash(es) for Image 1 (fdt-1): crc32+ sha1+
Reading from 0x24880000 to 0x40363cdc, size 0x200 ... OK
Reading from 0x24880000 to 0x40363cdc, size 0x2c21c5f ... OK
Hash(es) for rootfs: crc32+ sha1+
Firmware integrity verification passed
## Loading kernel from FIT Image at 46000000 ...
Using 'config-1' configuration
Verifying Hash Integrity ... sha1,rsa2048:fit_key+ OK
Trying 'kernel-1' kernel subimage
Description: ARM64 OpenWrt Linux-5.4.225
Type: Kernel Image
Compression: lzma compressed
Data Start: 0x460000e8
Data Size: 3527936 Bytes = 3.4 MiB
Architecture: AArch64
OS: Linux
Load Address: 0x48080000
Entry Point: 0x48080000
Hash algo: crc32
Hash value: b79241c0
Hash algo: sha1
Hash value: c250b70c33a7ba40d9e41f3c86424494eb35122d
Verifying Hash Integrity ... crc32+ sha1+ OK
## Loading fdt from FIT Image at 46000000 ...
Using 'config-1' configuration
Verifying Hash Integrity ... sha1,rsa2048:fit_key+ OK
Trying 'fdt-1' fdt subimage
Description: ARM64 OpenWrt mt7986a-ax7800-2500wan-emmc-rfb-sb device tree blob
Type: Flat Device Tree
Compression: uncompressed
Data Start: 0x4635d73c
Data Size: 24376 Bytes = 23.8 KiB
Architecture: AArch64
Hash algo: crc32
Hash value: 4d93a7d1
Hash algo: sha1
Hash value: 15ac1ac045311cadcb019095e8fafee5a4361971
Verifying Hash Integrity ... crc32+ sha1+ OK
Booting using the fdt blob at 0x4635d73c
Uncompressing Kernel Image
Loading Device Tree to 000000007f7ee000, end 000000007f7f6f37 ... OK
Starting kernel ...
[ 0.000000] Booting Linux on physical CPU 0x0000000000 [0x410fd034]
[ 0.000000] Linux version 5.4.225 (jenkins@BU10-bl2-Jenkins) (gcc version 8.4.0 (OpenWrt GCC 8.4.0 r0-c7f996bcb)) #0 SMP Fri Feb 24 07:03:21 2023
[ 0.000000] Machine model: MediaTek MT7986a RFB
[ 0.000000] earlycon: uart8250 at MMIO32 0x0000000011002000 (options '')
[ 0.000000] printk: bootconsole [uart8250] enabled
[ 0.000000] On node 0 totalpages: 261136
[ 0.000000] DMA32 zone: 4096 pages used for memmap
[ 0.000000] DMA32 zone: 0 pages reserved
[ 0.000000] DMA32 zone: 261136 pages, LIFO batch:63
[ 0.000000] psci: probing for conduit method from DT.
[ 0.000000] psci: PSCIv1.1 detected in firmware.
[ 0.000000] psci: Using standard PSCI v0.2 function IDs
[ 0.000000] psci: MIGRATE_INFO_TYPE not supported.
[ 0.000000] psci: SMC Calling Convention v1.0
[ 0.000000] percpu: Embedded 20 pages/cpu s44376 r8192 d29352 u81920
[ 0.000000] pcpu-alloc: s44376 r8192 d29352 u81920 alloc=20*4096
[ 0.000000] pcpu-alloc: [0] 0 [0] 1 [0] 2 [0] 3
[ 0.000000] Detected VIPT I-cache on CPU0
[ 0.000000] CPU features: detected: GIC system register CPU interface
[ 0.000000] CPU features: kernel page table isolation disabled by kernel configuration
[ 0.000000] Built 1 zonelists, mobility grouping on. Total pages: 257040
[ 0.000000] Kernel command line: console=ttyS0,115200n1 loglevel=8 earlycon=uart8250,mmio32,0x11002000 root=/dev/dm-0 rootwait rootfstype=squashfs,f2fs boot_param.no_split_rootfs_data boot_param.boot_kernel_part=PARTUUID=a975393e-a9bc-491f-8133-aeecf6075307 boot_param.boot_rootfs_part=PARTUUID=32798804-a1a7-4f95-ad5a-48939498675b boot_param.upgrade_kernel_part=PARTUUID=971f7556-ef1a-44cd-8b28-0cf8100b9c7e boot_param.upgrade_rootfs_part=PARTUUID=309a3e76-270b-41b2-b5d5-ed8154e7542b boot_param.env_part=PARTUUID=19a4763a-6b19-4a4b-a0c4-8cc34f4c2ab9 boot_param.rootfs_data_part=PARTUUID=5881ba72-d78f-4cbb-8fef-871aeb4b8eef boot_param.boot_image_slot=1 boot_param.upgrade_image_slot=0 boot_param.dual_boot dm-mod.create="dm-verity,,,ro,0 90384 verity 1 PARTUUID=32798804-a1a7-4f95-ad5a-48939498675b PARTUUID=32798804-a1a7-4f95-ad5a-48939498675b 4096 4096 11298 11299 sha256 4fae638245f52ce6e50b59eeec848e7439099179727213572aae4cedcbc9359f 212a5d7279e56d3b74df6346a8a8c4a4f7b5596e15fb2eb97f14e7a99c62
[ 0.000000] Dentry cache hash table entries: 131072 (order: 8, 1048576 bytes, linear)
[ 0.000000] Inode-cache hash table entries: 65536 (order: 7, 524288 bytes, linear)
[ 0.000000] mem auto-init: stack:off, heap alloc:off, heap free:off
[ 0.000000] Memory: 1013392K/1044544K available (7294K kernel code, 544K rwdata, 2084K rodata, 448K init, 291K bss, 31152K reserved, 0K cma-reserved)
slot 1
F0: 102B 0000
FA: 1040 0000
FA: 1040 0000 [0200]
F9: 103F 0000
F3: 1006 0033 [0200]
F3: 4001 00E0 [0200]
F3: 0000 0000
V0: 0000 0000 [0001]
00: 0000 0000
BP: 2400 0041 [0000]
G0: 1190 0000
EC: 0000 0000 [2000]
T0: 0000 0276 [010F]
Jump to BL
NOTICE: BL2: v2.6(release):de65b3e9d-dirty
NOTICE: BL2: Built : 15:22:40, Oct 28 2022
NOTICE: WDT: disabled
NOTICE: CPU: MT7986 (2002MHz)
NOTICE: EMI: Using DDR4 settings
NOTICE: EMI: Detected DRAM size: 1024MB
NOTICE: EMI: complex R/W mem test passed
NOTICE: Verifying BL Anti-Rollback Version ... bl_ar_ver:0=0+ OK
NOTICE: Verifying BL Anti-Rollback Version ... bl_ar_ver:0=0+ OK
NOTICE: Verifying BL Anti-Rollback Version ... bl_ar_ver:0=0+ OK
NOTICE: Verifying BL Anti-Rollback Version ... bl_ar_ver:0=0+ OK
NOTICE: Verifying BL Anti-Rollback Version ... bl_ar_ver:0=0+ OK
NOTICE: BL2: Booting BL31
NOTICE: BL31: v2.6(release):de65b3e9d-dirty
NOTICE: BL31: Built : 15:22:47, Oct 28 2022
U-Boot 2022.07-rc3 (Oct 28 2022 - 15:21:39 +0800), Build: jenkins-YX6_MT7986-AX7800-294
CPU: MediaTek MT7986
Model: mt7986-rfb
DRAM: 1 GiB
Core: 68 devices, 19 uclasses, devicetree: separate
MMC: mmc@11230000: 0
Setting bus to 0
Loading Environment from MMC... OK
In: serial@11002000
Out: serial@11002000
Err: serial@11002000
Net: eth0: ethernet@15100000
mtkautoboot gpio_reset:1
*** U-Boot Boot Menu ***
1. Startup system (Default)
2. Upgrade firmware
3. Upgrade ATF BL2
4. Upgrade ATF FIP
5. Upgrade eMMC partition table
6. Upgrade single image
7. Load image
0. U-Boot console
Press UP/DOWN to move, ENTER to select, ESC/CTRL+C to quit
Hit any key to stop autoboot: 0
MT7986> setenv dual_boot.current_slot 1
MT7986> mtkboardboot
Trying to boot from image slot 1
Reading from 0x22880000 to 0x40000000, size 0x200 ... OK
Reading from 0x22880000 to 0x40000000, size 0x363cdb ... OK
## Checking hash(es) for FIT Image at 40000000 ...
Hash(es) for Image 0 (kernel-1): crc32+ sha1+
Hash(es) for Image 1 (fdt-1): crc32+ sha1+
Reading from 0x24880000 to 0x40363cdc, size 0x200 ... OK
Reading from 0x24880000 to 0x40363cdc, size 0x2c21c5f ... OK
Hash(es) for rootfs: crc32+ sha1+
Firmware integrity verification passed
## Loading kernel from FIT Image at 46000000 ...
Using 'config-1' configuration
Verifying Hash Integrity ... sha1,rsa2048:fit_key+ OK
Trying 'kernel-1' kernel subimage
Description: ARM64 OpenWrt Linux-5.4.225
Type: Kernel Image
Compression: lzma compressed
Data Start: 0x460000e8
Data Size: 3527936 Bytes = 3.4 MiB
Architecture: AArch64
OS: Linux
Load Address: 0x48080000
Entry Point: 0x48080000
Hash algo: crc32
Hash value: b79241c0
Hash algo: sha1
Hash value: c250b70c33a7ba40d9e41f3c86424494eb35122d
Verifying Hash Integrity ... crc32+ sha1+ OK
## Loading fdt from FIT Image at 46000000 ...
Using 'config-1' configuration
Verifying Hash Integrity ... sha1,rsa2048:fit_key+ OK
Trying 'fdt-1' fdt subimage
Description: ARM64 OpenWrt mt7986a-ax7800-2500wan-emmc-rfb-sb device tree blob
Type: Flat Device Tree
Compression: uncompressed
Data Start: 0x4635d73c
Data Size: 24376 Bytes = 23.8 KiB
Architecture: AArch64
Hash algo: crc32
Hash value: 4d93a7d1
Hash algo: sha1
Hash value: 15ac1ac045311cadcb019095e8fafee5a4361971
Verifying Hash Integrity ... crc32+ sha1+ OK
Booting using the fdt blob at 0x4635d73c
Uncompressing Kernel Image
Loading Device Tree to 000000007f7ee000, end 000000007f7f6f37 ... OK
Starting kernel ...
[ 0.000000] Booting Linux on physical CPU 0x0000000000 [0x410fd034]
[ 0.000000] Linux version 5.4.225 (jenkins@BU10-bl2-Jenkins) (gcc version 8.4.0 (OpenWrt GCC 8.4.0 r0-c7f996bcb)) #0 SMP Fri Feb 24 07:03:21 2023
[ 0.000000] Machine model: MediaTek MT7986a RFB
[ 0.000000] earlycon: uart8250 at MMIO32 0x0000000011002000 (options '')
[ 0.000000] printk: bootconsole [uart8250] enabled
[ 0.000000] On node 0 totalpages: 261136
[ 0.000000] DMA32 zone: 4096 pages used for memmap
[ 0.000000] DMA32 zone: 0 pages reserved
[ 0.000000] DMA32 zone: 261136 pages, LIFO batch:63
[ 0.000000] psci: probing for conduit method from DT.
[ 0.000000] psci: PSCIv1.1 detected in firmware.
[ 0.000000] psci: Using standard PSCI v0.2 function IDs
[ 0.000000] psci: MIGRATE_INFO_TYPE not supported.
[ 0.000000] psci: SMC Calling Convention v1.0
[ 0.000000] percpu: Embedded 20 pages/cpu s44376 r8192 d29352 u81920
[ 0.000000] pcpu-alloc: s44376 r8192 d29352 u81920 alloc=20*4096
[ 0.000000] pcpu-alloc: [0] 0 [0] 1 [0] 2 [0] 3
[ 0.000000] Detected VIPT I-cache on CPU0
[ 0.000000] CPU features: detected: GIC system register CPU interface
[ 0.000000] CPU features: kernel page table isolation disabled by kernel configuration
[ 0.000000] Built 1 zonelists, mobility grouping on. Total pages: 257040
[ 0.000000] Kernel command line: console=ttyS0,115200n1 loglevel=8 earlycon=uart8250,mmio32,0x11002000 root=/dev/dm-0 rootwait rootfstype=squashfs,f2fs boot_param.no_split_rootfs_data boot_param.boot_kernel_part=PARTUUID=a975393e-a9bc-491f-8133-aeecf6075307 boot_param.boot_rootfs_part=PARTUUID=32798804-a1a7-4f95-ad5a-48939498675b boot_param.upgrade_kernel_part=PARTUUID=971f7556-ef1a-44cd-8b28-0cf8100b9c7e boot_param.upgrade_rootfs_part=PARTUUID=309a3e76-270b-41b2-b5d5-ed8154e7542b boot_param.env_part=PARTUUID=19a4763a-6b19-4a4b-a0c4-8cc34f4c2ab9 boot_param.rootfs_data_part=PARTUUID=5881ba72-d78f-4cbb-8fef-871aeb4b8eef boot_param.boot_image_slot=1 boot_param.upgrade_image_slot=0 boot_param.dual_boot dm-mod.create="dm-verity,,,ro,0 90384 verity 1 PARTUUID=32798804-a1a7-4f95-ad5a-48939498675b PARTUUID=32798804-a1a7-4f95-ad5a-48939498675b 4096 4096 11298 11299 sha256 4fae638245f52ce6e50b59eeec848e7439099179727213572aae4cedcbc9359f 212a5d7279e56d3b74df6346a8a8c4a4f7b5596e15fb2eb97f14e7a99c62
[ 0.000000] Dentry cache hash table entries: 131072 (order: 8, 1048576 bytes, linear)
[ 0.000000] Inode-cache hash table entries: 65536 (order: 7, 524288 bytes, linear)
[ 0.000000] mem auto-init: stack:off, heap alloc:off, heap free:off
[ 0.000000] Memory: 1013392K/1044544K available (7294K kernel code, 544K rwdata, 2084K rodata, 448K init, 291K bss, 31152K reserved, 0K cma-reserved)
Thanks for the logs, it confirms that situation is the same on W6 and W6d models, OpenWrt is not persistent after router restart in both cases...
Hi @cbxbiker61
Did you manage to compile a modified u-boot and change menu option 0 to boot the existing OpenWRT image ?
It looks that in device tree (in the part that is removed in order to boot vanilla OpenWrt) there is a key "fit_key":
MT7986> fdt list /signature
signature {
key-fit_key {
};
};
MT7986>
And later on, this key is used for hash integrity verification:
MT7986> setenv dual_boot.current_slot 1
MT7986> mtkboardboot
Trying to boot from image slot 1
Reading from 0x22880000 to 0x40000000, size 0x200 ... OK
Reading from 0x22880000 to 0x40000000, size 0x363cdb ... OK
## Checking hash(es) for FIT Image at 40000000 ...
Hash(es) for Image 0 (kernel-1): crc32+ sha1+
Hash(es) for Image 1 (fdt-1): crc32+ sha1+
Reading from 0x24880000 to 0x40363cdc, size 0x200 ... OK
Reading from 0x24880000 to 0x40363cdc, size 0x2c21c5f ... OK
Hash(es) for rootfs: crc32+ sha1+
Firmware integrity verification passed
## Loading kernel from FIT Image at 46000000 ...
Using 'config-1' configuration
>>>>>>>>>> Verifying Hash Integrity ... sha1,rsa2048:fit_key+ OK
Trying 'kernel-1' kernel subimage
Description: ARM64 OpenWrt Linux-5.4.225
Type: Kernel Image
Compression: lzma compressed
Data Start: 0x460000e8
Data Size: 3527936 Bytes = 3.4 MiB
Architecture: AArch64
OS: Linux
Load Address: 0x48080000
Entry Point: 0x48080000
Hash algo: crc32
Hash value: b79241c0
Hash algo: sha1
Hash value: c250b70c33a7ba40d9e41f3c86424494eb35122d
Verifying Hash Integrity ... crc32+ sha1+ OK
## Loading fdt from FIT Image at 46000000 ...
Using 'config-1' configuration
>>>>>>>>>> Verifying Hash Integrity ... sha1,rsa2048:fit_key+ OK
Trying 'fdt-1' fdt subimage
...
I don't think it is possible that vanilla Open Wrt image would somehow pass this kind of verification done by stock Acer U-Boot so in my opinion new U-Boot is the only way forward in order to have persistent vanilla OpenWrt on W6/W6d devices...
Cheers,
Przemek
So, only option to have persistent Openwrt is exchange Uboot. But what if BL2 before loading UBoot will also check Uboot signature?
I have W6 and confirm no openwrt after restart - always execute mtkboardboot
Indeed, this is a valid question.
I think that when ATF (Arm Trusted Firmware) is in use, both BL2 and U-Boot itself are generated and it is possible to replace both.
According to the below tutorial, after compiling ATF, there should be bl2.img and fip.bin files and BL2 should be put in boot0 partition (bl2 partition does not exist for eMMC in GPT).
https://forum.openwrt.org/t/tutorial-build-customize-and-use-mediatek-open-source-u-boot-and-atf/134897
However, it might be possible that security goes even deeper and BL2 image itself is verified by BL1 BootROM...
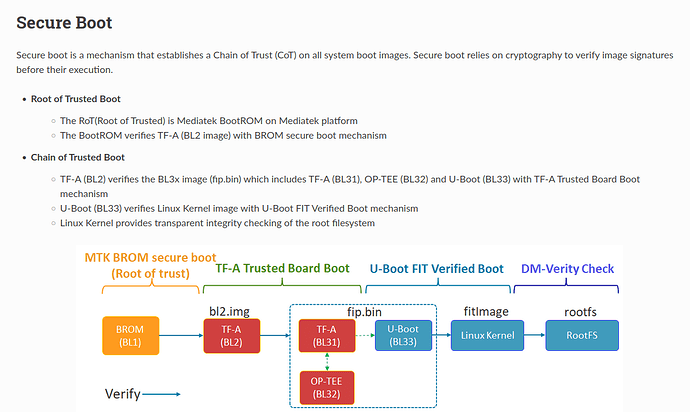
Secure Boot
So many open questions with those routers...
Cheers,
Przemek
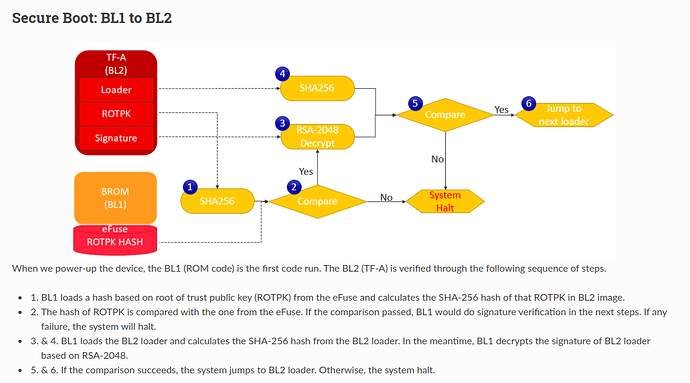
Apparently Acer enables the full-chain secure boot.
That means BL2 is definitely signed and will be verified by BootROM.
You can't replace the stock BL2 without signing it with the same RSA private key Acer is using.