How can I duplicate this feature of Tomato? in the GUI? Thanks.
EDIT: So sorry, I forgot to add the image.
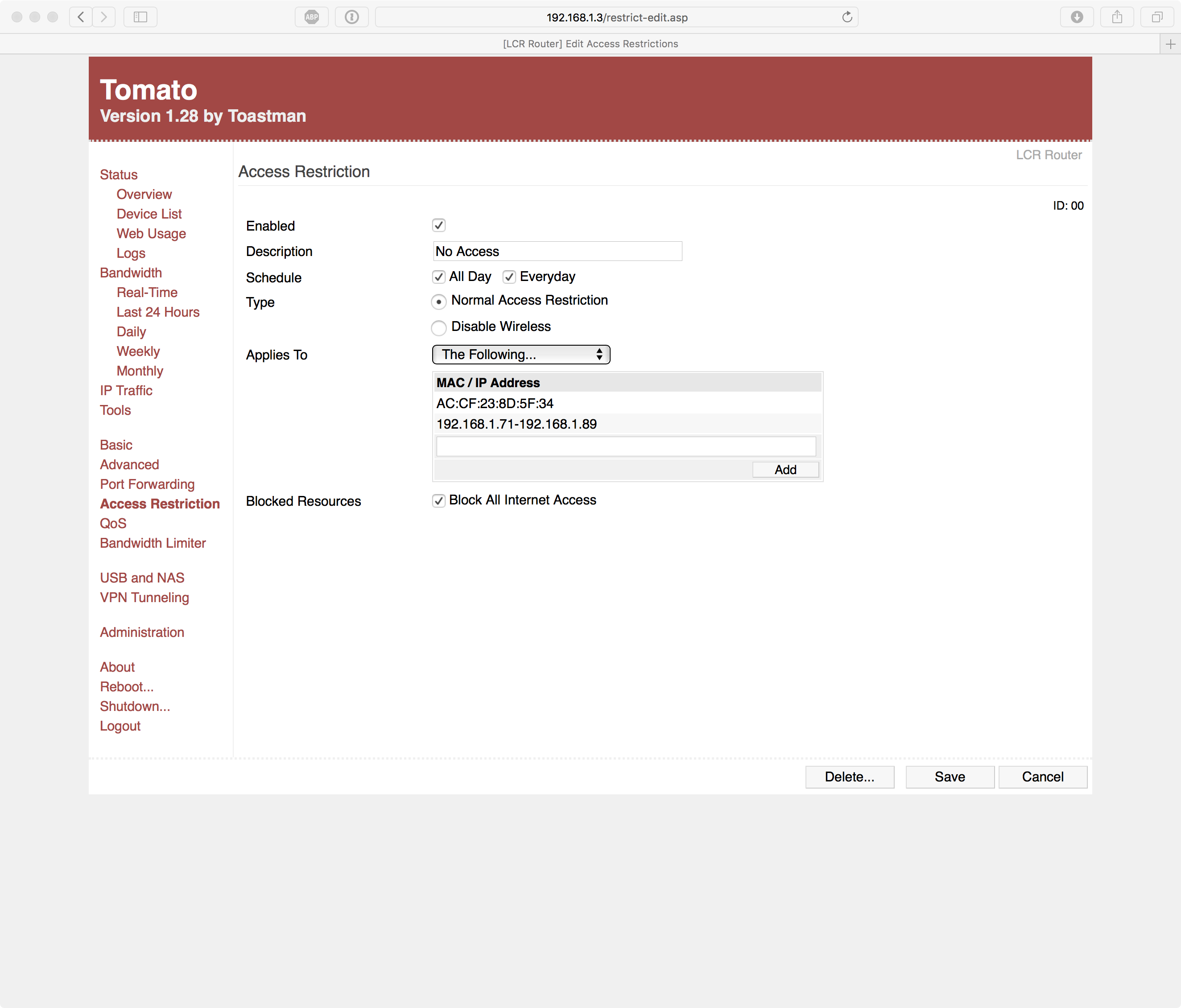
How can I duplicate this feature of Tomato? in the GUI? Thanks.
EDIT: So sorry, I forgot to add the image.

Please, better describe what's you're seeking...as LEDE only has a single user (root).
I think you wish to add user's and groups to LuCI, if so, see: [SOLVED] Add new user from UCI
Hopefully the picture helps.
AAAH! I've seen your edit.
You do this in firewall. It MUST be a Traffic Rule. At the bottom of the rule, you can set days and times.
MAC filtering is available on an interface-by-interface basis
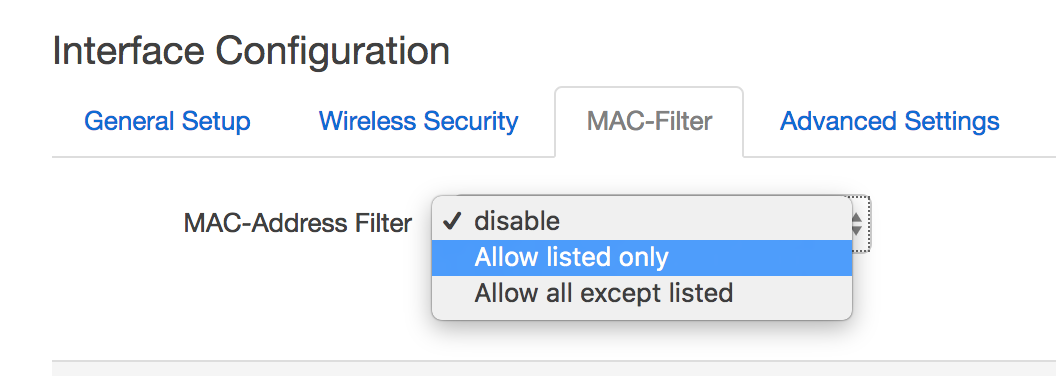
@jeff, this is incorrect. You showed a picture in Wireless. Your picture is a menu that enables and disables an access list for MACs that can/cannot connect to a given SSID.
The correct rule is made in FIREWALL > TRAFFIC RULES. Placing the rule in FIREWALL will work whether the device is wireless or wired.
I agree with @lleachii that if you want to prevent access to resources by wired clients, then an ingress firewall rule is appropriate as well.
Depending on your infrastructure and intent, you may also need to apply MAC filtering at the WiFi level, especially if you wish to restrict wireless-to-wireless as these packets may be handled by the WiFi interface itself or a bridge, and never go through the kernel firewall. I don't think that client isolation is revealed in the LuCI interface, but can be configured (see, for example, https://medium.com/openwrt-iot/lede-openwrt-setting-up-client-isolation-72cc38b15b1d). Full isolation has its drawbacks as well, such as peer-to-peer services that many enjoy, like iOS AirDrop.
Is that what you are searching for?
https://openwrt.org/docs/user-guide/services/parental-controls
Yes that is pretty well it @tmomas. I didn't think of parental control as this is to prevent rogue internet access by network devices that don't ever need it to do their job.
The next issue is that I don't have parental controls on my Archer C7 build from @r00t. Is it installable? I cannot find it.
You create your own parental control by following the guide @tmomas linked to.
Using LuCI -
Network → Firewall → Traffic Rules → New forward rule
OK, I've finally gotten back to this, and I want to define a range of source LAN addresses to reject. How would I enter 192.168.1.71-89? I tried 192.168.1.71-192.168.1.89 also and both said invalid.
You would enter IP range in CDIR notation.
That range is invalid...network's begin on even numbers...
If you really don't know CIDR notation, you should probably use standard Class C ranges for all your LANs, they always end in /24 and the last octet range is always 0-255.
See: https://en.wikipedia.org/wiki/Classless_Inter-Domain_Routing
Can't iprange be used instead?
iptables-mod-iprange - 1.4.21-3 - iptables extensions for matching ip ranges. Matches: - iprange
kmod-ipt-iprange - 4.4.92-1 - Netfilter (IPv4) module for matching ip ranges Includes: - iprange
I am familiar with CIDR notation but it's been almost 20 years since I took just the first semester of CCNA in high school.
Yes I remember that and I am happy not to use it. I cannot use iprange or kernel modules because of the optimized Archer build I loaded.
See this thread on creating an ipset and including it in a port forwarding rule...
Hi jwoods,
you won't need custom fw rules. It can be on your existing rules. I also restrict connections only from certain IPs. Create standard fw rule in "Firewall - Port Forwards". After this, open /etc/config/firewall and add this section :
config ipset
option external 'name_of_ipset_list'
option match 'src_net'
option family 'ipv4'
option storage 'hash'
Than find your redirect and add line option ipset 'name_of_ipset_list'
Save, restart firewall or device and it should work. Now if you type "ipset list", you should see your ipset list(s) with "References:" number according to number of redirects using this list.
I hope I didn't forget something 