I have been able to make 802.11r work - it was a long process and would not have been possible without the help of the forum here and Reddit posts - my setup is a bit more complicated as I use multiple tagged vlans and Radius auth for one of the SSID. I hope the following will help people trying to get this going. All this was done using 21.02.1 - I replaced iw with iw-full and use hostapd-wolfssl - as this is a dumb AP wpad is not used - I am not sure if the iw change is required - I need full hostapd as I use Radius auth.
Let me start by saying that the Gui 'automatic' setup just did not work for me - there are many people that say it does, I am am sure it does for many, but I wonder if people test it properly - by far the best method I found for Android is to use the WiFiman app - select Signal Mapper, and walk around - if you see BSSID to BSSID transitions it is working fine. If you see Disconnected to BSSID transition in WiFiman, 11r is NOT working.
If you don't have access to Android, your next best option is to enable level 1 debug for hostapd process and look for the FT string. Again please note you need to verify that the client you are using for testing does support 802.11r - without that you might be wasting your time ( see below how to test your client ).
Here are the steps I took to make my setup work:
- Test my clients for 802.11r support ( used both Android 11 and 12 ) using profiler script
- Obtain BSSID for all the SSID used for roaming on all access points used
- Generate config using helper.py script
- Update /etc/config/wireless and restart with wifi reload command
- Test using WiFiman or enable loglevel 1 for hostapd
-
Testing clients - in my case I used Kali Linux and follow the steps on link - the only problem I run into was that my newer Wifi adapter was not supported - otherwise it does work and can generate fair bit of info - the output is saved in /var/www/html/profiler
-
Obtain BSSID - I have two APs, each with 3 SSID, on both 2.4 and 5Ghz - right now only one SSID is used for roaming ie used by mobile devices - the others are for fixed IOT devices - in my case the wlan0 and wlan1 are assigned - to avoid mistakes with MAC addresses I would recommend to cut&paste. The command I used to quickly find the relation between SSID and BSSID was:
ssh to AP
egrep '^(ssid|bssid|interface|bss)=' /var/run/hostapd-phy*.conf
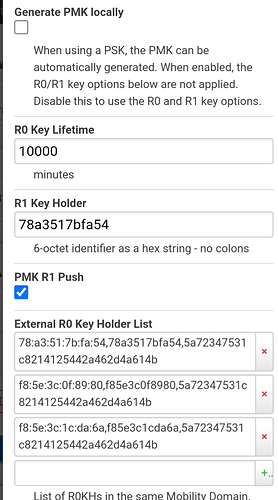
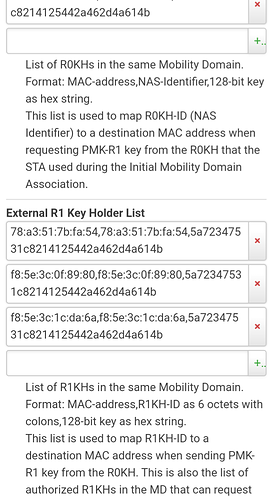
- Generate config using helper.py (link)- it will create output that can be used with uci or added directly to the wireless config - I used the config method
On any system that can run Python3
cd /tmp
wget https://raw.githubusercontent.com/walidmadkour/OpenWRT-UCI-helper-802.11r/master/helper.py
chmod +x helper.py
./helper.py 0 -ap XX:XX:XX:XX:XX:XX -ap YY:YY:YY:YY:YY:YY -ap ... --format config
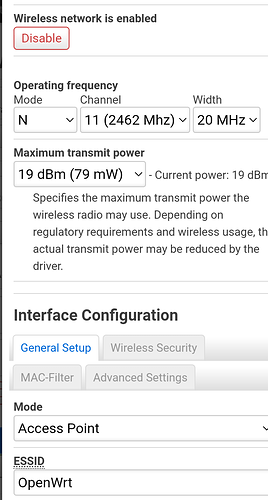
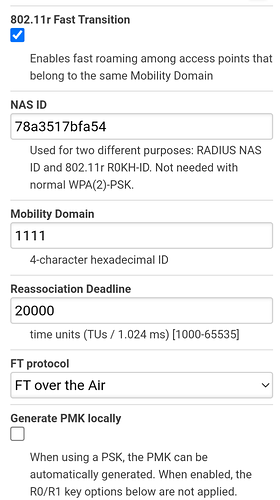
- Ssh to your AP and use the output of the above command to update the wireless config - please make sure to match the correct SSID with the helper output - also I needed to add the following options to each SSID used for roaming:
vi /etc/config/wireless
config wifi-iface 'wifinetX'
...
option reassociation_deadline '20000'
option ft_over_ds '0'
option ft_psk_generate_local '0'
wifi reload
- Test - as mentioned before WiFiman was the simplest way to test it as it clearly shows when roaming - you will see BSSID to BSSID transitions under the Signal Mapper button - to get there:
- connect your phone to the SSID used for roaming
- start Wifiman
- select Wireless menu - will display list of all networks
- select your SSID
- you should see a blue button 'Signal Mapper' - if you don't see the button, you have not selected the SSID your phone is connected to.
As with any problem, once you have a working solution it, it is much easier to go back - you can look at removing some things from the config, and even trying the Gui method - I would backup the /etc/config/wireless file - at least the manual method does work and is a good starting point for people that are having difficulty getting 802.11r going - good luck.