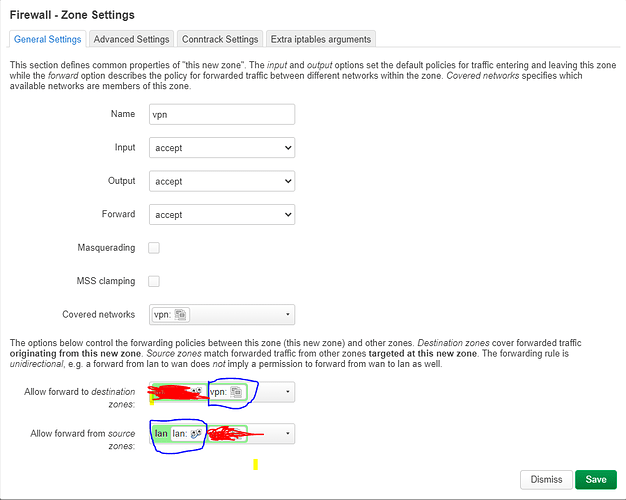
@psherman @mk24 have implemented changes you both have suggested, sharing new status;
what works -
- Connection between 2 routers using wireguard works,
- Internet works in both locations
- Wireguard client can access all Tunnel IP (192.168.9.1) and Lan (192.168.0.1/24) allocated in server
- Server can only access Tunnel IP in client (192.168.9.3) and Lan (192.168.1.1)
- Zerotier works, now i can access Zerotier client (farmhouse) without wireguard connection
- Another Peer2/client2 (Iphone) which also connected to server (Home), can access Peer 1 (farmhouse) 192.168.1.1 and 192.168.9.3 both
doesn't work
- Server can't access farmhouse subnet e.g. 192.168.1.127 (but it can access 192.168.1.1 only)
this time sharing some result of tcpdup monitoring while attemting to access farmhouse subnet 192.168.1.127 from Home subnet 192.168.0.189, it might support diagnosis
root@farmhouse:~# tcpdump -i br-lan host 192.168.1.127 -vv
21:43:31.448952 IP (tos 0x0, ttl 235, id 21113, offset 0, flags [DF], proto TCP (6), length 52)
ec2-43-204-103-22.ap-south-1.compute.amazonaws.com.31006 > 192.168.1.127.40796: Flags [.], cksum 0xc09d (correct), seq 3, ack 546, win 849, options [nop,nop,TS val 3178480494 ecr 10247046], length 0
21:43:32.549642 IP (tos 0x0, ttl 126, id 2419, offset 0, flags [DF], proto TCP (6), length 52)
192.168.0.189.54033 > 192.168.1.127.80: Flags [S], cksum 0xe0b0 (correct), seq 3706937228, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
21:43:32.587132 IP (tos 0x0, ttl 126, id 2420, offset 0, flags [DF], proto TCP (6), length 52)
192.168.0.189.54034 > 192.168.1.127.80: Flags [S], cksum 0x1e40 (correct), seq 2391109738, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
21:43:32.806121 IP (tos 0x0, ttl 126, id 2421, offset 0, flags [DF], proto TCP (6), length 52)
192.168.0.189.54038 > 192.168.1.127.80: Flags [S], cksum 0x418b (correct), seq 3204324514, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
21:43:33.560130 IP (tos 0x0, ttl 126, id 2422, offset 0, flags [DF], proto TCP (6), length 52)
192.168.0.189.54033 > 192.168.1.127.80: Flags [S], cksum 0xe0b0 (correct), seq 3706937228, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
21:43:33.591112 IP (tos 0x0, ttl 126, id 2423, offset 0, flags [DF], proto TCP (6), length 52)
192.168.0.189.54034 > 192.168.1.127.80: Flags [S], cksum 0x1e40 (correct), seq 2391109738, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
21:43:33.821096 IP (tos 0x0, ttl 126, id 2424, offset 0, flags [DF], proto TCP (6), length 52)
192.168.0.189.54038 > 192.168.1.127.80: Flags [S], cksum 0x418b (correct), seq 3204324514, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
21:43:35.562136 IP (tos 0x0, ttl 126, id 2425, offset 0, flags [DF], proto TCP (6), length 52)
192.168.0.189.54033 > 192.168.1.127.80: Flags [S], cksum 0xe0b0 (correct), seq 3706937228, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
21:43:35.597113 IP (tos 0x0, ttl 126, id 2426, offset 0, flags [DF], proto TCP (6), length 52)
192.168.0.189.54034 > 192.168.1.127.80: Flags [S], cksum 0x1e40 (correct), seq 2391109738, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
21:43:35.829105 IP (tos 0x0, ttl 126, id 2427, offset 0, flags [DF], proto TCP (6), length 52)
192.168.0.189.54038 > 192.168.1.127.80: Flags [S], cksum 0x418b (correct), seq 3204324514, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
21:43:36.285822 IP (tos 0x0, ttl 64, id 40752, offset 0, flags [DF], proto UDP (17), length 88)
192.168.1.127.48141 > ec2-35-154-85-188.ap-south-1.compute.amazonaws.com.6000: [udp sum ok] UDP, length 60
21:43:36.288137 IP (tos 0x0, ttl 64, id 12665, offset 0, flags [DF], proto UDP (17), length 88)
192.168.1.127.48141 > ec2-3-108-32-185.ap-south-1.compute.amazonaws.com.6000: [udp sum ok] UDP, length 60
21:43:36.383834 IP (tos 0x0, ttl 236, id 13333, offset 0, flags [DF], proto UDP (17), length 72)
ec2-35-154-85-188.ap-south-1.compute.amazonaws.com.6000 > 192.168.1.127.48141: [udp sum ok] UDP, length 44
21:43:36.415475 IP (tos 0x0, ttl 236, id 37178, offset 0, flags [DF], proto UDP (17), length 72)
ec2-3-108-32-185.ap-south-1.compute.amazonaws.com.6000 > 192.168.1.127.48141: [udp sum ok] UDP, length 44
21:43:36.702450 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.127 tell farmhouse.lan, length 28
21:43:36.705227 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.127 is-at 50:2b:73:a0:11:92 (oui Unknown), length 28
^C
23 packets captured
23 packets received by filter
0 packets dropped by kernel
![]() )
)