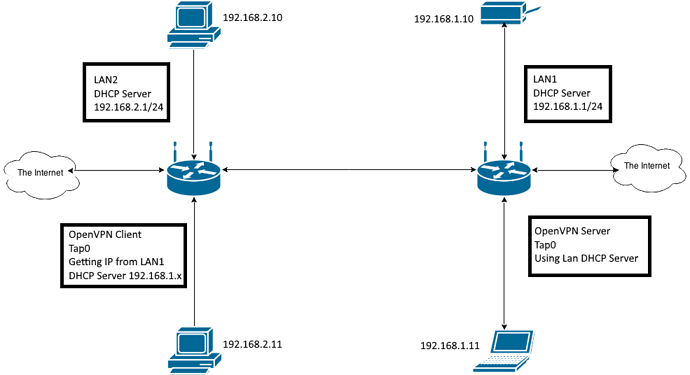
Need some help with my current setup.
I have 1 router running openvpn as a tap server, this router has a lan address of 172.20.1.1 and openvpn uses the lans dhcp server to push 172.20.1.x address to openvpn clients.
The second router has openvpn as a tap client which uses a 192.168.1.x address on the tap interface pushed by router 1. This router also has its own lan address of 192.168.2.1 and uses DHCP to push ips to its own lan clients,
I have a connection between the 2 routers and i can browse router 1 (server) from router 2 (client) and its lan of 172.20.1.x from the openvpn client router and devices from 192.168.1.x lan.
BUT i can not browse anything on the client lan from router 1 openvpn server. I know this is because the client lan uses 192.168.1.x and its not routed to the openvpn server. How can i achieve this???
Forgive the picture as it uses different ips but same setup
Openvpn Server (Lan1)
Network
config interface 'lan'
option type 'bridge'
option proto 'static'
option ipaddr '172.20.1.1'
option netmask '255.255.255.0'
option ip6assign '64'
list dns '62.6.40.162'
list dns '62.6.40.178'
list dns '8.8.8.8'
list dns '8.8.4.4'
option ifname 'eth0.1 tun0 tap0'
config device 'lan_eth0_1_dev'
option name 'eth0.1'
option macaddr '9a:2e:04:67:81:34'
config interface 'wan'
option ifname 'eth0.2'
option proto 'pppoe'
option username '**************************'
option password '**************************'
option ipv6 'auto'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr '9a:2e:04:67:81:35'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix '56'
option peerdns '0'
list dns '2620:119:35::35'
list dns '2620:119:53::53'
config interface 'Tap_TCP'
option proto 'none'
option ifname 'tap0'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
config route
option interface 'Tap_TCP'
option target '192.168.1.0'
option netmask '255.255.255.0'
option gateway '172.20.1.241'
Firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option drop_invalid '1'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
option network 'lan Tap_TCP'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option target 'ACCEPT'
option dest_port '*****'
option name 'Allow Forwarded VPN TAP Request -> <device>'
option src 'wan'
option family 'ipv4'
list proto 'tcp'
list proto 'udp'
Openvpn Config
config openvpn 'VPN_Tap'
option dev 'tap0'
option port '*****'
option ifconfig_pool_persist '/etc/openvpn/ccd/Home_VPN_TAP/ipp.txt'
option cipher 'AES-256-CBC'
option auth 'SHA512'
option tls_server '1'
option tls_version_min '1.2'
option log '/var/run/openvpn.Home_VPN_TAP0.log'
option log_append '/var/run/openvpn.Home_VPN_TAP0.log'
option status '/var/run/openvpn.Home_VPN_TAP0.status 5'
option verb '5'
option keepalive '10 120'
option client_to_client '1'
option persist_key '1'
option persist_tun '1'
option sndbuf '393216'
option rcvbuf '393216'
option user 'nobody'
option group 'nogroup'
option float '1'
option fast_io '1'
option auth_nocache '1'
option mtu_test '0'
option server_bridge '172.20.1.1 255.255.255.0 172.20.1.240 172.20.1.245'
option comp_lzo 'yes'
option ca '/etc/openvpn/keys/ca.crt'
option dh '/etc/openvpn/keys/dh4096.pem'
option cert '/etc/openvpn/keys/server.crt'
option key '/etc/openvpn/keys/server.key'
option down_pre '0'
option script_security '0'
option tls_auth '/etc/openvpn/keys/ta.key 0'
option max_clients '5'
option enabled '1'
list tls_cipher 'TLS-ECDHE-RSA-WITH-AES-256-GCM-SHA384'
list push 'sndbuf 393216'
list push 'rcvbuf 393216'
list push 'dhcp-option DNS 172.20.1.1'
option proto 'tcp-server'
Openvpn Client (Lan2)
Network
config interface 'lan'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option ifname 'eth0.1'
config device 'lan_eth0_1_dev'
option name 'eth0.1'
option macaddr 'b6:c8:94:64:72:77'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr 'b6:c8:94:64:72:78'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
config interface 'VPN_Tap'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '172.20.1.241'
option ifname 'tap0 eth0.1'
Firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option drop_invalid '1'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option mtu_fix '1'
option masq '1'
option network 'lan VPN_Tap'
config forwarding
option src 'lan'
option dest 'wan'
Openvpn Config
config openvpn 'VPN_Tap'
option float '1'
option client '1'
option comp_lzo 'yes'
option dev 'tap0'
option reneg_sec '0'
option persist_key '1'
option nobind '1'
option remote_cert_tls 'server'
option ca '/etc/openvpn/keys/ca.crt'
option cert '/etc/openvpn/keys/bthh5.crt'
option key '/etc/openvpn/keys/bthh5.key'
option cipher 'AES-256-CBC'
option auth 'SHA512'
option tls_auth '/etc/openvpn/keys/ta.key 1'
option tls_version_min '1.2'
option log '/var/log/VPN_TAP0.log'
option log_append '/var/log/VPN_TAP0.log'
option status '/var/log/VPN_TAP0.status 5'
option verb '5'
option keepalive '10 120'
option persist_tun '1'
option sndbuf '393216'
option rcvbuf '393216'
option user 'nobody'
option group 'nogroup'
option auth_nocache '1'
option proto 'tcp-client'
option tls_client '1'
list tls_cipher 'TLS-ECDHE-RSA-WITH-AES-256-GCM-SHA384'
option port '*****'
option down_pre '0'
list remote 'somedomain.name.com'
option pull '1'
option enabled '1'
option fast_io '1'
option client_to_client '0'
Thanks in advance.